Introduction
Mobile malware remains one of the greatest threats in the world of technology today with many unscrupulous apps bobbing up from time to time. A prime example is the recent FireScam Android app which impersonates the popular messaging platform Telegram. The fraudulent software has been developed to steal sensitive user data and it’s dangerous to say the least. This blog further elaborates how FireScam operates, its potential impact, and best practices to protect against such threats[1].
What is FireScam Malware?
As the name, FireScam suggests, the app in question is the perfect blend of neo cyber and scamming as it uses social engineering tactics to deceive the user into thinking that it is a paid version of the regular Telegram app. The end goal of FireScam is to gain access to the user’s private data, and selling the app online allows the developers to perform just that. The app is hosted on GitHub.io domain that mimic RuStore, Russia’s alternative app marketplace. Once the user installs the app, FireScam uses a dropper APK that installs the main payload to get extensive permission to monitor notifications, intercept SMS, capture clipboard data and e-commerce transactions. All the data captured is then uploaded in real time onto a secure Firebase database ensuring minimal risk of getting caught. The app then connects to a WebSocket to seamlessly execute remote commands and download the necessary information without being detected. The malware spreads by exploiting trust in legitimate-looking platforms, emphasizing the dangers of downloading apps from unverified sources[2].

Figure 1: RuStore clone hosted on a GitHub.io domain[5]
The Deceptive Strategy of FireScam
FireScam uses a well-coordinated phishing strategy to distribute its malware. The malware is hosted on a fake GitHub.io phishing website that imitates RuStore, Russia’s sanctioned application market. The malware also exploits victim’s trust in legitimate platforms. The phony app claims to offer premium Telegram services, preying on users seeking enhanced messaging features [5].
How Does FireScam Work?
- Disguised App: FireScam mimics the Telegram app to appear legitimate, tricking users into downloading it.
- Permissions Abuse: After installation, it requests extensive permissions under the guise of app functionality.
- Data Theft: The malware siphons sensitive information, including:
- Personal messages and media files.
- Login credentials and PINs.
- Banking and financial details.
- Command-and-Control (C2) Communication: FireScam connects to its C2 server to upload stolen data and receive instructions for further malicious activities.
FireScam’s Capabilities
FireScam is a meticulous data thief as it pays attention to detail targeting different kinds of sensitive information to exfiltrate. Everything begins with a parody of a web view login page where it tricks users into revealing their login details. Furthermore, the malware keeps track of clipboard usage, capturing data like passwords that the user copies, or autofill entries from their password manager. It also meticulously observes e-commerce transactions, in which case the user’s activity during online shopping is recorded so it can acquire sensitive payment details. Apart from this, FireScam also collects personal and some system data such as contact lists, SMS messages, and system logs which are all uploaded to its Firebase database. Once the data is extracted it is temporarily and then filtered for valuable information and thereafter erased to cover all traces from investigators[3].
Upon execution, FireScam leverages a deceptive WebView screen to steal Telegram credentials while establishing communication with a Firebase Realtime Database for real-time data uploads and device tracking. The malware also opens a persistent WebSocket connection with its Firebase command-and-control (C2) endpoint, allowing it to execute commands such as requesting specific data, triggering immediate uploads, downloading additional payloads, and adjusting surveillance settings. FireScam actively monitors screen activity, capturing events like app usage and screen on/off changes, and logs activities lasting over 1,000 milliseconds.
To achieve a complete form of the cyber surveillance, FireScam demonstrates advances spying capabilities by tracking every action done by the users including typing, dragging and dropping and clipboard copying or pasting. Its ability to exfiltrate categorized data to attackers underscores the critical need for heightened vigilance and robust security practices, especially for users relying on third-party app stores or downloading from unfamiliar sources[5].
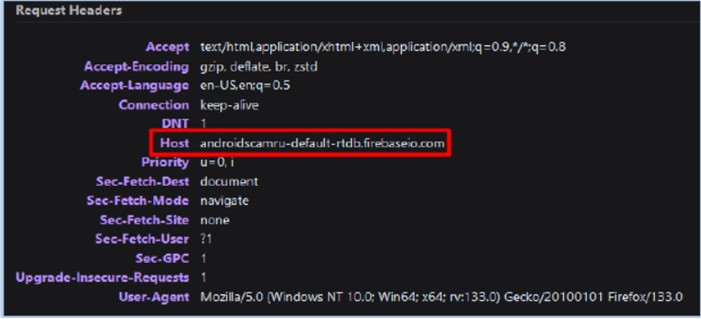
Figure 2: Exfiltrated content from compromised device on firebase database endpoint [5]
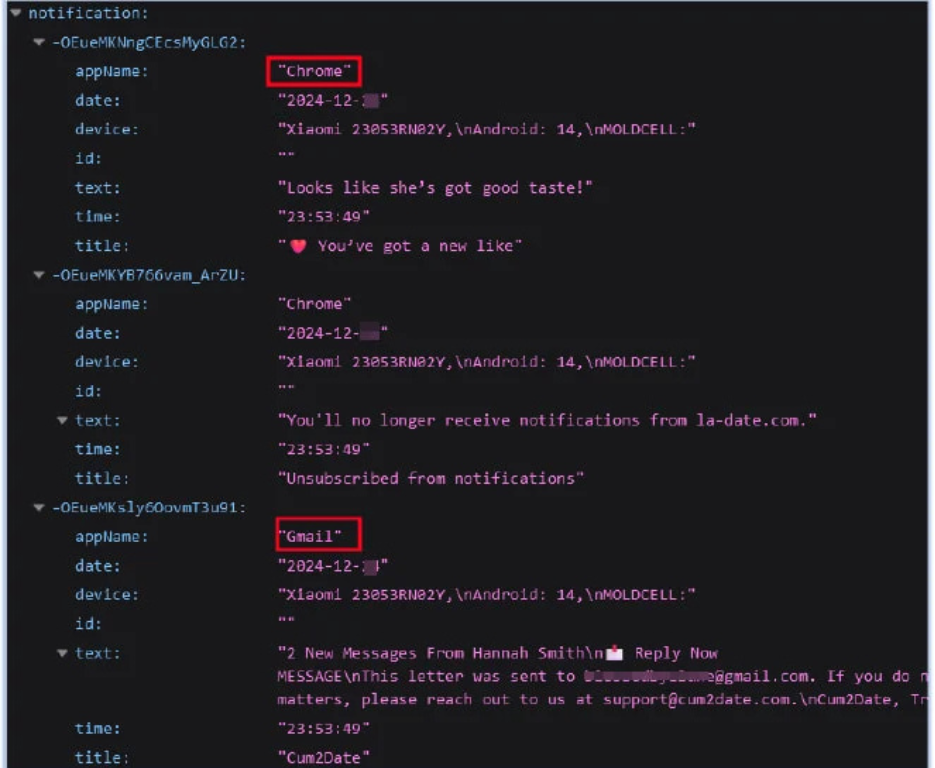
Figure 3: Exfiltrated content from compromised device on firebase database endpoint [5]
Who is at Risk?
Anyone downloading apps from unofficial or unverified sources is at risk. The malware specifically targets Android users and exploits vulnerabilities such as outdated operating systems or lack of security awareness.
Who is Behind FireScam?
While the exact operators remain unidentified, the malware’s sophisticated design suggests it originates from well-resourced cybercriminal groups. Its specific targeting of Russian platforms indicates a strategic alignment with local app store dynamics, possibly leveraging geopolitical trends[3].
How to Protect Against FireScam
- Stick to Official App Stores: Avoid downloading apps from third-party websites, especially those mimicking legitimate platforms.
- Enable Google Play Protect: Android’s built-in security feature blocks known threats.
- Verify App Authenticity: Cross-check app details, developer information, and reviews before installation.
- Educate Yourself: Stay informed about emerging malware threats to identify phishing attempts.
- Limit Permissions: Grant app permissions selectively and review existing permissions regularly.
Conclusion
The FireScam malware highlights the ongoing threats to mobile security, particularly on the Android platform. By leveraging fake app impersonation, attackers exploit users’ trust and access sensitive data. Proper understanding of these threats and proactive measures that counter them is essential for the protection of sensitive personal information of individuals and organizations. When engaging with apps on the internet, remember to be cautious and secure.
References
- https://www.scworld.com/news/firescam-android-malware-poses-as-telegram-app-to-steal-sensitive-data
- https://thehackernews.com/2025/01/firescam-android-malware-poses-as.html
- https://www.bleepingcomputer.com/news/security/new-firescam-android-data-theft-malware-poses-as-telegram-premium-app/
- https://www.kaspersky.com/resource-center/preemptive-safety/avoid-android-malware
- https://www.cyfirma.com/research/inside-firescam-an-information-stealer-with-spyware-capabilities/


This blog provides valuable insight into FireScam malware and its sophisticated methods of exploiting user trust – especially given the political situation happening in Russia at the present moment. With the sanctions in place, many Russians are finding themselves between a rock and a hard place when it comes to accessing applications, given that there’s a new ban every week and the threat of being cut off from the rest of the world. This makes a good section of the population vulnerable and your analysis highlights the need for user awareness and robust security measures. I do wonder though, what could be the potential consequences beyond individual user exploitation, such as the potential impact on enterprises or national security when credentials or other sensitive data is stolen en masse. There is also the potential for this malware to target specific regions or leverage geopolitical dynamic (part of cyber warfare?). Your blog is a great reminder of the growing risks in the mobile security landscape, especially in countries under political distress. How can we balance user convenience with stringent security measures in the face of such sophisticated threats, like this malware?
Interesting post. This is eye-opening especially because of the speed at which we download apps without verifying if it is the accurate one, especially with Android devices. User privacy is one of the most critical topics in the world today, and knowing that downloading a makeshift version of telegram could steal all an individual’s sensitive information is extremely alarming. Thanks for the insightful post. The consequences of this could easily exceed far beyond just stealing basic user information. This could be used by hacker groups or others as a means to steal even more critical data or could even be used as spear phishing or whaling attacks to target specific individuals. It is surprising how many people out there, even cybersecurity directors have been victims to phishing emails or other malicious endeavours.
This is a very interesting post, Michael! It is frightening to se how much information they can truly gather through advanced spying capabilities. Tracking every action done by the users including typing, dragging and dropping and clipboard copying or pasting will reveal tons of information that can be used against the users permission. Moreover, FireScams gain extensive permission to monitor notifications, intercept SMS, capture clipboard data and e-commerce transactions. This underscores the need for tight security measures not only at the company or organization level but also at the personal level. Like you mentioned, there are multiple methods to protect against FireScams. I usually cross-check app details, developer information, and reviews before installing any apps. Additionally, you mention enabling Google Play Protect which is an Android’s built-in security feature blocks known threats. Is there an Apple built-in version or is there some extension Apple users can install to ensure greater protection? Great Post Michael!
Wow! This is a great read and an eye opener to one of the endless schemes of these bad guys! If only we can pay attention to details and verify everything on the internet before trusting any app used with our personal details, I believe these scammers would have very few people fall into their traps but that seems almost impossible.
Security awareness is highly recommended for everyone maybe once in 2 months as the schemes never ends and we need to keep refreshing our security awareness mindsets to try fight off these scammers in the best way possible and it starts with each and everyone of us.
Wow! This is a great read and an eye opener to one of the endless schemes of these bad guys! If only we can pay attention to details and verify everything on the internet before trusting any app used with our personal details, I believe these scammers would have very few people fall into their traps but that seems almost impossible.
Security awareness is highly recommended for everyone maybe once in 2 months as the schemes never ends and we need to keep refreshing our security awareness mindsets to try fight off these scammers in the best way possible and it starts with each and everyone of us.
Wow! This is a great read and an eye opener to one of the endless schemes of these bad guys! If only we can pay attention to details and verify everything on the internet before trusting any app used with our personal details, I believe these scammers would have very few people fall into their traps but that seems almost impossible.
Security awareness is highly recommended for everyone maybe once in 2 months as the schemes never ends and we need to keep refreshing our security awareness mindsets to try fight off these scammers in the best way possible and it starts with each and everyone of us.
Wow! This is a great read and an eye opener to one of the endless schemes of these bad guys! If only we can pay attention to details and verify everything on the internet before trusting any app used with our personal details, I believe these scammers would have very few people fall into their traps but that seems almost impossible.
Security awareness is highly recommended for everyone maybe once in 2 months as the schemes never ends and we need to keep refreshing our security awareness mindsets to try fight off these scammers in the best way possible and it starts with each and everyone of us.
Wow! This is a great read and an eye opener to one of the endless schemes of these bad guys! If only we can pay attention to details and verify everything on the internet before trusting any app used with our personal details, I believe these scammers would have very few people fall into their traps but that seems almost impossible.
Security awareness is highly recommended for everyone maybe once in 2 months as the schemes never ends and we need to keep refreshing our security awareness mindsets to try fight off these scammers in the best way possible and it starts with each and everyone of us.
Wow! This is a great read and an eye opener to one of the endless schemes of these bad guys! If only we can pay attention to details and verify everything on the internet before trusting any app used with our personal details, I believe these scammers would have very few people fall into their traps but that seems almost impossible.
Security awareness is highly recommended for everyone maybe once in 2 months as the schemes never ends and we need to keep refreshing our security awareness mindsets to try fight off these scammers in the best way possible and it starts with each and everyone of us.
Wow! This is a great read and an eye opener to one of the endless schemes of these bad guys! If only we can pay attention to details and verify everything on the internet before trusting any app used with our personal details, I believe these scammers would have very few people fall into their traps but that seems almost impossible.
Security awareness is highly recommended for everyone maybe once in 2 months as the schemes never ends and we need to keep refreshing our security awareness mindsets to try fight off these scammers in the best way possible and it starts with each and everyone of us.
Wow! This is a great read and an eye opener to one of the endless schemes of these bad guys! If only we can pay attention to details and verify everything on the internet before trusting any app used with our personal details, I believe these scammers would have very few people fall into their traps but that seems almost impossible.
Security awareness is highly recommended for everyone maybe once in 2 months as the schemes never ends and we need to keep refreshing our security awareness mindsets to try fight off these scammers in the best way possible and it starts with each and everyone of us.
Wow! This is a great read and an eye opener to one of the endless schemes of these bad guys! If only we can pay attention to details and verify everything on the internet before trusting any app used with our personal details, I believe these scammers would have very few people fall into their traps but that seems almost impossible.
Security awareness is highly recommended for everyone maybe once in 2 months as the schemes never ends and we need to keep refreshing our security awareness mindsets to try fight off these scammers in the best way possible and it starts with each and everyone of us.
This blog is such an eye-opener! It really highlights how sneaky and dangerous malware like FireScam can be, especially with the challenges people in Russia are facing right now. With so many relying on unverified apps due to sanctions, the risk of having personal data stolen is so real—and scary.
What really struck me is how this doesn’t just stop at individuals. The ripple effects on businesses and even national security are huge. It’s alarming to think about how easily something like this could escalate into bigger cyberattacks.
This post is a great reminder for all of us to stay vigilant. We often download apps without a second thought, and that trust can be so easily exploited. It’s a call to be more cautious and to make security awareness a regular part of our lives. Thank you for such an informative and timely piece—it really makes you think!
Great post for spreading awareness, Michael! It can be used as some learning to ignorant smart phone user that FireScam is a malware on mobile targeting Android users. Disguised as a premium version of Telegram, it tricks victims into downloading malicious programs that steal sensitive information like messages, credentials, and even financial data. Such malware spreads via phony websites, permission abuse, or high-end spy modus operandi. Stick to official app stores, enable security features, and be watchful about granting too many app permissions. Such a great insight for present day security and privacy preserving perspective.
Really insightful post Michael. Super detailed breakdown of how Firescam works and what it’s capable of which is really scary. Especially for me who just last year swapped to an android phone. Though I do still feel pretty safe as like you said in the post this scam comes from downloading apps from untrusted third-party app stores. Which I find interesting as like you said it seems to be targeting Russians and might be using the geopolitical trends to its advantage. As I believe there’s lots of censorship in Russia and hence people are downloading VPNs more which I wonder might require them to go to these third-party app stores. Which eventually gets them compromised. They also might be specifically looking for Telegram which is one of the most secure messaging apps out there.