Introduction:
At present, cybersecurity incidents are increasing day by day at an alarming rate. Attackers often find loopholes or weaknesses in the digital systems or infrastructure and exploit them for their personal gain, for damaging the reputation of organizations, and to exploit the privacy of users. Even the leading cybersecurity companies, like Palo Alto Networks, are also prone to cyberattacks. In late December 2024, Palo Alto Networks faced a serious security-related incident. Palo Alto Networks disclosed a security vulnerability affecting its PAN-OS software, which powers the firewall products of the company. The flaw is identified as CVE-2024-3393, which allowed hackers to exploit a denial-of-service (DoS) vulnerability, leading to firewall disruptions of the company [1] [2].
Technical Details of Vulnerability:
The main cause of CVE-2024-3393 was found in the DNS Security feature of PAN-OS. By sending the malicious packet through the firewall’s data plane, attackers exploit this vulnerability and force the firewall to reboot. Hackers continuously attempt to trigger this condition, which causes firewalls to enter maintenance mode and ultimately disrupts network security operations. This vulnerability impacts PAN-OS versions 10.X and 11.X as well as Prisma Access, which runs on PAN-OS version 10.2.8 and later or prior to 11.2.3 [3] [2].
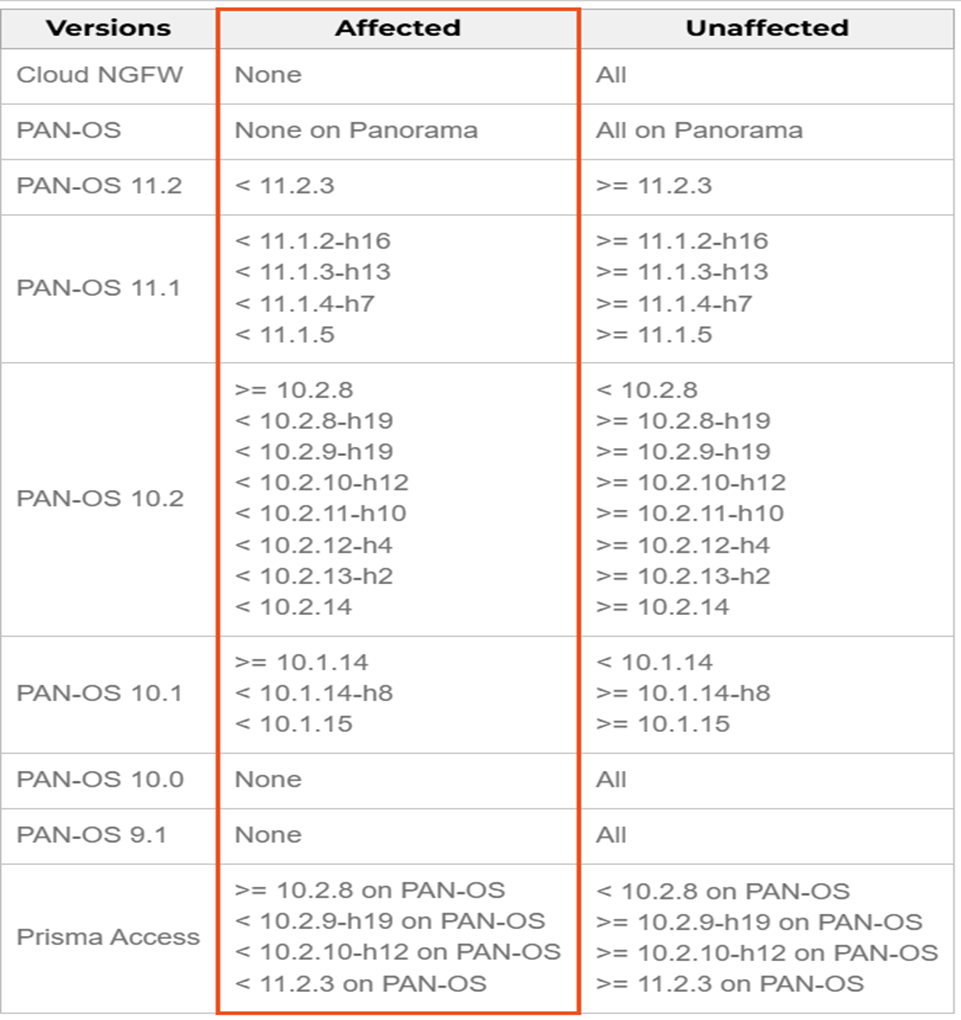
The CVE-2024-3393 vulnerability has been assigned a high severity CVSS score of 8.7 [3] [4].
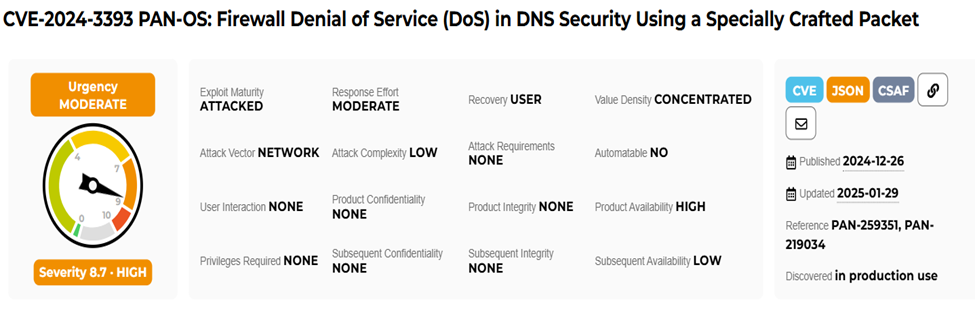
The Company Response:
The vulnerability was being actively exploited by the hackers and was accepted by Palo Alto Networks. They also confirmed that customers experienced outages when their firewalls blocked malicious DNS packets [1][2]. The company also released an advisory to inform customers on how to protect their environment and to provide transparency [2].
Mitigation and Patching:
Palo Alto Networks released patches for the affected PAN-OS versions. The fixes were implemented in PAN-OS versions 10.1.14-h8, 10.0.10-h12, 11.1.5, 11.2.3, and all later PAN-OS versions. However, the PAN-OS 11.0, which was also affected, did not receive any patch because it had reached its end-of-life (EOL) date on November 17. To mitigate the risk of exploitation, the customers are strongly advised to update their system to these versions [1].
For clients who are unable to update their system immediately, Palo Alto Networks provided workarounds and mitigation steps. Clients can disable DNS Security logging by setting the log severity to “none” for all configured DNS Security categories within each Anti-Spyware profile [3]. This can be done by navigating to:
1. Objects → Security Profiles → Anti-Spyware → DNS Policies → DNS Security for each Anti-Spyware profile.
2. For all configured DNS Security categories, change the Log Severity to “none”.
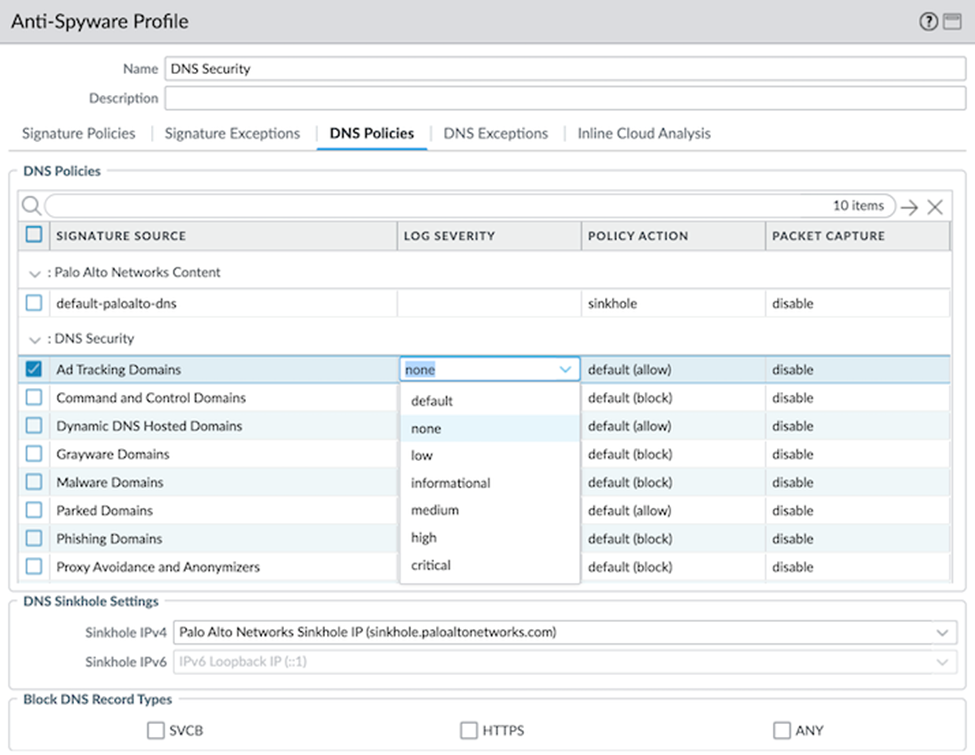
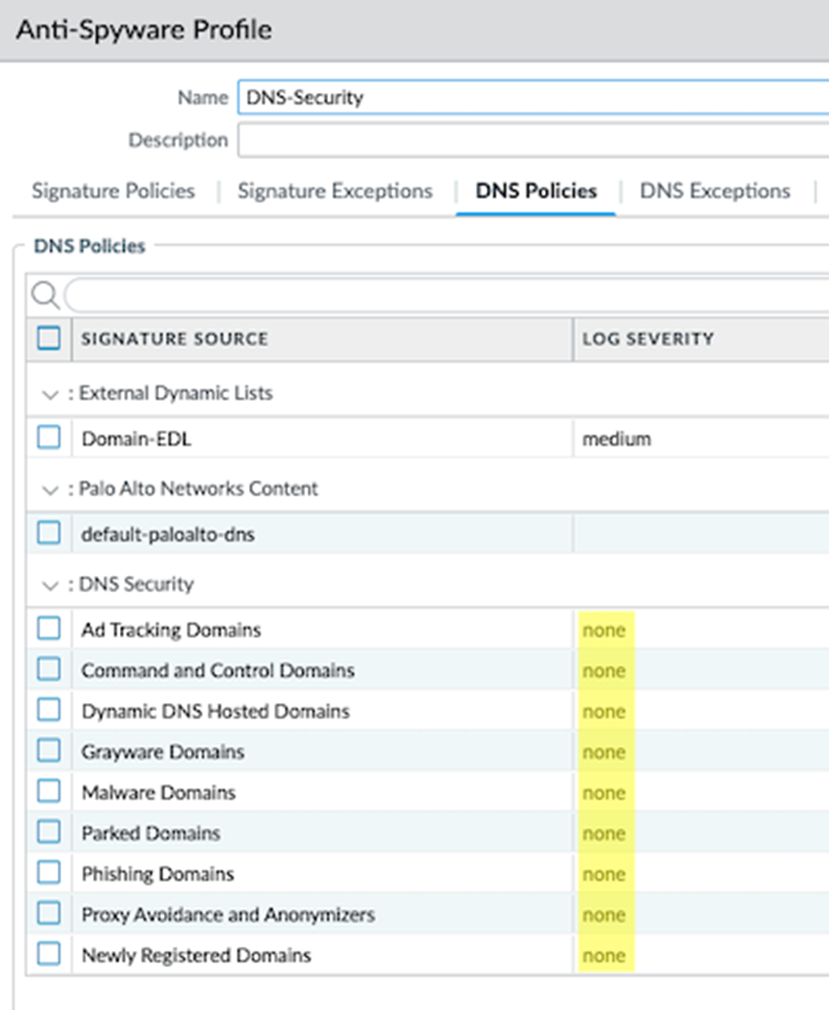
3. Commit the changes and remember to revert the log severity once the fixes are applied [3].
The customers who were using the firewalls managed by Strata Cloud Manager (SCM) were also advised to disable DNS Security logging as a temporary workaround [2].
Broader Implications:
This was not the only security related incident that was faced by Palo Alto Networks in recent times. . In November 2024, the company had warned users of potential remote code execution (RCE) vulnerability in the PAN-OS. Additionally, earlier that month, Palo Alto Networks confirmed the exploitation of critical zero-day vulnerabilities (CVE-2024-0012 and CVE-2024-9474) in their firewalls. This earlier incident already put Palo Alto Networks users at high alert. The Cybersecurity and Infrastructure Security Agency (CISA) had ordered all federal civilian agencies to patch the vulnerabilities that were found in November by December 9 [5]. “These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise,” warned CISA [6].
Conclusion:
This incident serves as a warning that security devices like firewalls also have flaws that need to be addressed as soon as possible. This incident also serves as a strong reminder to the organizations to have regular updates, the need for vigilance, and adherence to security best practices, which are using Palo Alto Networks products, and also reminds us of the need for and importance of a layered security approach to maintain protection even when primary security is compromised.
Reference:
2. https://thehackernews.com/2024/12/palo-alto-releases-patch-for-pan-os-dos.html
3. https://security.paloaltonetworks.com/CVE-2024-3393?utm_source=chatgpt.com
4. https://nvd.nist.gov/vuln/detail/CVE-2024-3393
5. https://therecord.media/palo-alto-networks-firewall-vulnerabilities-exploited-patched

Excellent post, Akshar!
Software vulnerabilities pose significant security risks, especially when originating from trusted vendors such as Palo Alto. The impact of these flaws can be substantial, often triggering cascading disruptions that affect thousands of IT services globally. A recent example is the incident involving CrowdStrike, where a security software update caused a widespread IT outage, leading to severe disruptions, including extensive airline delays [1]. Similarly, the Log4j vulnerability in Apache’s logging service resulted in widespread exploitation among Oracle customers [2]. These critical security flaws raise an ongoing debate regarding accountability for cybersecurity risks. While vendors respond promptly with patches, their mitigation efforts are inherently limited. Consequently, this highlights the increasing responsibility of customers in managing security risks. Organizations must proactively implement Threat Intelligence solutions to ensure real-time threat detection and maintain up-to-date security measures.
[1] Weston, D. (2024, July 20). Helping our customers through the CrowdStrike outage. The Official Microsoft Blog. https://blogs.microsoft.com/blog/2024/07/20/helping-our-customers-through-the-crowdstrike-outage
[2] Cybersecurity and Infrastructure Security Agency. (n.d.). Apache Log4j vulnerability guidance. U.S. Department of Homeland Security. Retrieved February 6, 2025, from https://www.cisa.gov/news-events/news/apache-log4j-vulnerability-guidance
“Great job, Akshar! This incident really highlights how sophisticated cyberattacks have become, proving that even top-tier security solutions like Palo Alto Networks firewalls aren’t invincible. It’s concerning to see such a critical vulnerability with a CVSS score of 8.7, especially since attackers can repeatedly exploit it to disable firewalls—the very systems designed to protect networks. The fact that CISA had to step in underscores the urgency of applying patches. This situation also reinforces the importance of adopting a layered security approach, as relying solely on firewalls isn’t enough when attackers can find ways to neutralize them.”
Hi Akshar, great post! I thoroughly enjoyed your topic, especially how you broke down the technical details of the CVE-2024-3393 vulnerability. Even strong security infrastructures like firewalls may become key points of failure when certain features are targeted, as demonstrated by the description of how the DNS Security feature in PAN-OS was used to launch a denial of service attack. Furthermore, the mitigation strategies you mentioned were especially interesting due to their ability to work around the disabled DNS security logging. This approach demonstrated how even slight configuration alterations can result in significant differences that reduce the present active threats. Lastly, the issue that stood out to me was that even a leading cybersecurity firm like Palo Alto Networks became susceptible to this kind of threat, bringing into discussion the ever-changing nature of cybersecurity threats.
Great work, Akshar! This justifies why security best practices need to be a priority for organisations, not just at the beginning of the design phase but throughout the run of their systems, even security systems. Ongoing proactive maintenance and regular evaluations are essential to safeguarding infrastructure.
Building a secure system requires group cooperation because everyone involved must help spot and lower security threats. A security system composed of several protection layers proves its worth in this incident. If one defence system breaks down, other security measures will keep functioning to maintain system protection.
Great work, Akshar! This justifies why security best practices need to be a priority for organisations, not just at the beginning of the design phase but throughout the run of their systems, even security systems. Ongoing proactive maintenance and regular evaluations are essential to safeguarding infrastructure.
Building a secure system requires group cooperation because everyone involved must help spot and lower security threats. A security system composed of several protection layers proves its worth in this incident. If one defence system breaks down, other security measures will keep functioning to maintain system protection.
Great findings, Akshar! Your insightful work highlights a significant security concern involving famous companies like Palo Alto Networks firewalls. It’s really alarming how the denial-of-service (DoS) vulnerability, identified as CVE-2024-3393, has been exploited by attackers to disrupt firewall operations.
This weakness resides in the DNS Security feature of the PAN-OS software and allows unauthenticated attackers to send malicious packets through the firewall’s data plane, causing it to reboot.
In my opinion, preventive measures such as attack surface reduction, Anycast network diffusion, and real-time adaptive threat monitoring can be implemented for safeguarding.
More DDoS prevention methods: https://www.cloudflare.com/learning/ddos/how-to-prevent-ddos-attacks/
Great findings, Akshar! Your insightful work highlights a significant security concern involving famous companies like Palo Alto Networks firewalls. It’s really alarming how the denial-of-service (DoS) vulnerability, identified as CVE-2024-3393, has been exploited by attackers to disrupt firewall operations.
This weakness resides in the DNS Security feature of the PAN-OS software and allows unauthenticated attackers to send malicious packets through the firewall’s data plane, causing it to reboot.
In my opinion, preventive measures such as attack surface reduction, Anycast network diffusion, and real-time adaptive threat monitoring can be implemented for safeguarding.
More DDoS prevention methods: https://www.cloudflare.com/learning/ddos/how-to-prevent-ddos-attacks/
Thank you for your post, Akshar! Cybersecurity is a critical topic, and I believe we have all heard the saying: It’s not a matter of if a cybersecurity attack will happen, but when. This highlights the importance of being prepared at all times. From reading your post, I find it particularly concerning that even companies specializing in cybersecurity are becoming targets of attacks. These are the very organizations that businesses rely on to protect their websites, yet they themselves are vulnerable.
Palo Alto Networks, a leading cybersecurity company, still faces technical vulnerabilities. Attackers have found ways to force their firewalls to reboot, demonstrating that even industry leaders have room for improvement. However, I appreciate their swift response, even for an end-of-life product, they took action to address the loophole. This proactive approach helps minimize business losses and reinforces customer trust in the company.