The event I will be speaking about is the recent rise in cyber incidents targeting Operational Technology systems (OT) and how these systems are increasingly converging with traditional IT networks. This convergence has made OT one of the most attractive and dangerous targets for cybercriminals. Unlike IT systems, which primarily handle data, OT systems control the physical processes behind power grids, hospitals, water treatment plants, and industrial operations. A single breach can move quickly from the digital world into real-world consequences such as blackouts, contaminated water, or delayed medical care.
Challenges:
One of the biggest challenges is that many of these systems are used daily by people who are not cybersecurity experts. Attackers are aware of this and often exploit human error as their entry point. They only need to trick one person out of a hundred, through a phishing email, a malicious link, or a weak password, and they can gain access to highly sensitive information. Once inside, the attacker has a foothold to move deeper into the network, sometimes unnoticed until it is too late.
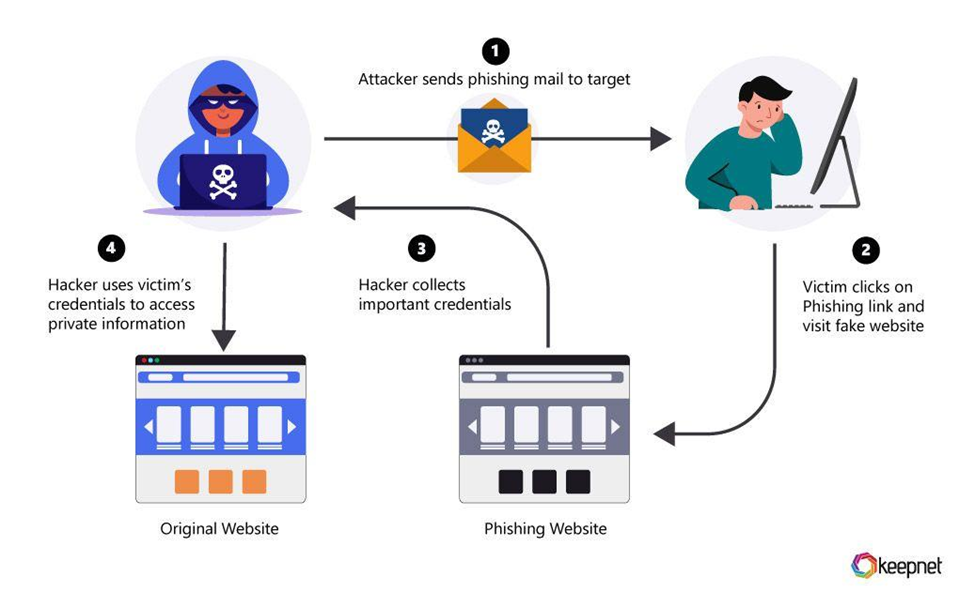
Figure 1. The technical flow of a phishing campaign involves the attacker sending a phishing email, the victim clicking a malicious link, credentials being harvested, and the attacker gaining unauthorized access.
(Source: Keepnet Labs, “How to Spot Phishing Emails: A Comprehensive Guide,” accessed September 18, 2025.)
Healthcare as a Case Study:
Healthcare is a good example of where OT and IT converge, and where the risks are very real. If medical staff are not well-trained to recognize threats, attackers can exploit them as the weakest link. During my internship at Alberta Health Services, I saw firsthand how important awareness is. The organization regularly simulated phishing attempts to test whether staff would click suspicious links, and those who fell for it were given more training. This approach shows that preparation and ongoing education are essential, but it also highlights that vulnerabilities are always present.
I also learned just how dependent modern healthcare has become on networked systems. At times, the network would go down for routine technical reasons, and suddenly hundreds of calls would flood into the service desk from nurses and staff unable to access patient information. These outages caused delays in treatment and even in scheduled surgeries. Now imagine the same situation caused not by a scheduled or random outage but by a targeted cyberattack. Without access to patient records, doctors would not know what medications a patient is taking or whether they have allergies, which could make treatment unsafe or even life-threatening.
Why OT Attacks Matter in Canada:
This is why the surge in OT-related cyber incidents in Canada is so concerning. The Canadian Cybersecurity Network has reported that threats against critical infrastructure are growing, fueled by both cybercriminals seeking profit and nation-state actors interested in disruption. As IT and OT systems become more interconnected, the potential attack surface only grows larger. Traditional security measures like firewalls are no longer enough; protections must include strong authentication, encryption of sensitive data, continuous monitoring, and incident response planning.
Conclusion:
In my view, cybersecurity in critical infrastructure is not optional; it is essential. Governments must do more to create pathways for qualified professionals to work in this field, whether through education programs, funding, or public-private partnerships. At the same time, staff at all levels should receive regular training so they understand the role they play in keeping systems safe. A cyberattack on a social media account might be inconvenient, but a cyberattack on a hospital or power grid could put lives at risk.
References:
Industrial Cyber. (2025, August 28). Canadian Cybersecurity Network report highlights surge in OT cyber incidents, rising critical infrastructure vulnerabilities. Retrieved September 18, 2025, from https://industrialcyber.co/reports/canadian-cybersecurity-network-report-highlights-surge-in-ot-cyber-incidents-rising-critical-infrastructure-vulnerabilities/
Keepnet Labs. (n.d.). How to Spot Phishing Emails: A Comprehensive Guide. Retrieved September 18, 2025, from https://keepnetlabs.com/blog/how-to-spot-phishing-emails-a-comprehensive-guide


Interesting post! I agree with you. Healthcare is one of the most attacked and sensitive areas in cyberthreats and they contain all our protected health information. I have recently seen a documentary about Aleksanteri Kivimäki in “Most Wanted: Teen Hacker” and how patients confidential documents about their psychotherapy treatments were leaked. It really emphasizes how disrupting and lifechanging this kind of breach of privacy can be for the victim.