When most people think of data breaches, they imagine stolen credit cards or leaked emails. But in 2023, DNA testing giant 23andMe exposed something far more intimate: its customers’ genetic information. Fast forward to June 2025, and UK regulators fined the company £2.3 million for failing to protect sensitive genetic data. This included family trees, health reports, and ancestry details belonging to more than 150,000 British residents [1], [4].
This blog will explore three key issues:
- Jurisdiction and accountability – how countries can fine companies under data protection laws, regardless of where those companies are headquartered.
- The legitimacy of the fines – why penalties like these are not only allowed but necessary, especially when dealing with data as permanent and personal as DNA.
- Data deletion and prevention – whether it’s truly possible to erase genetic data once shared, and what both companies and individuals can do to better safeguard their accounts against credential-stuffing and weak authentication practices.
Jurisdiction and Accountability: Why the UK Could Fine, but the US and Canada Could Not
Although 23andMe is a US-based company, its operations in the UK fall under UK data protection laws (GDPR), giving the Information Commissioner’s Office (ICO) the authority to fine them. In contrast, the US lacks equivalent federal protection for consumer genetic data. The Health Insurance Portability and Accountability Act (HIPAA) only cover healthcare providers and insurers, not direct-to-consumer DNA companies [3].
This creates a sharp divide, while a hospital’s mishandling of genetic data could trigger strict penalties under health law, a consumer genetics company like 23andMe is governed by weaker consumer protection system. These laws do not provide the same enforcement power, leaving regulators with limited ability to impose meaningful fines, even when the compromised data is as sensitive and irreversible as DNA.
As Harvard law scholar I. Glenn Cohen explains, when customers share their DNA with a company like 23andMe, “you are treated by the law essentially as a consumer, not as the patient” [3]. In practice, this means that genetic testing customers do not benefit from the same rights and protections that medical patients receive. The result is a significant regulatory gap, US authorities cannot impose fines even for breaches of highly personal genetic information.
Canada faces similar challenges. While its privacy commissioner investigated the breach alongside the ICO, Canadian law (PIPEDA) currently does not allow for monetary penalties [2].
PIPEDA vs. GDPR vs. HIPAA: Analysis
Table 1: Extracted from Digital Samba: How Much Overlap Is There Between GDPR in the EU, HIPAA in the US & PIPEDA in Canada? [7]
| Aspect | GDPR | HIPAA | PIPEDA |
| Jurisdiction | EU Member States | United States | Canada |
| Applicability | Any organization handling EU data. | Healthcare providers and plans. | Private sector organizations. |
| Type of data covered | Personal data (names, contacts, financial info, etc.) | Healthcare data (PHI, records, insurance, payments) | Personal info (contacts, financial, employment, etc.) |
| Data transfer abroad | Allowed to countries with adequate protection; otherwise SCCs/BCRs needed | No direct rules; PHI transfers require BAAs | Requires consent and disclosure of risks for foreign transfers |
| Personally Identifiable Information (PII) encryption at rest & transit | Required | Requires appropriate safeguards to protect PHI. | Not explicitly required |
| Controlled access to sensitive data | Mandates controlled access to personal data, especially sensitive data. Requires strict authentication, authorization, and monitoring measures. | Requires controlled access to protected health information (PHI). Enforces role-based access control through Business Associate Agreements (BAAs). | Does not specify any specific controls but mandates appropriate security safeguards. Organizations should control access to sensitive personal information and restrict it to authorized personnel. |
| Data breach notifications | 72 hours. | Within 60 days. | Within a reasonable time frame. |
Why This Fine Was Warranted
The £2.3m fine against 23andMe is more than a symbolic gesture, it serves as a clear message that companies profiting from sensitive personal data must be held accountable. Genetic information is especially vulnerable because it exposes health risks, ethnic background, and family ties. And unlike a password or credit card, DNA cannot be reset or replaced once it has been compromised [1]. By failing to implement standard security measures, 23andMe exposed millions of customers to identity risks, genetic discrimination, and potential misuse of their most personal data. Regulators were right to act decisively, and the fine was both allowed and warranted.
Data Deletion and Prevention: Can You Ever Really Erase DNA?
In response to the breach, many customers rushed to delete their accounts. But here’s the uncomfortable truth: deleting your data may not fully erase it. While 23andMe allows users to request account deletion through its privacy portal, genetic privacy experts have warned that remnants of anonymized data often remain [3]. And anonymization is not foolproof. Cross-referencing with other datasets can sometimes re-identify individuals.
California’s Attorney General has urged residents to delete their data and genetic samples after the company’s financial struggles but acknowledged that deletion might not mean a complete clean slate [3]. For example, users can request full erasure via 23andMe’s privacy portal, but the company warns that some data may still be retained due to legal obligations[3].
The Real Cost of Weak Authentication
The breach itself was made possible by credential stuffing, a common hacking method. Attackers used stolen username and password pairs from unrelated breaches, betting that users had recycled passwords across accounts. This was a topic we explored on a simpler level on day 2 of the course in regard to password hashing and the ‘reversing’ of a password hash. However, the specific method used by hackers leveraged automated tools to test these logins against 23andMe’s systems until thousands of accounts were compromised [5].
As a result, the ICO found that 23andMe failed to enforce even the most basic protections, such as:
- Multi-factor authentication (MFA)
- Stronger password requirements
- Adequate monitoring for abnormal login activity [1], [4]
This negligence was not just careless; it made exploitation inevitable. As Microsoft has reported, MFA could block 99.9% of credential stuffing attacks [6].
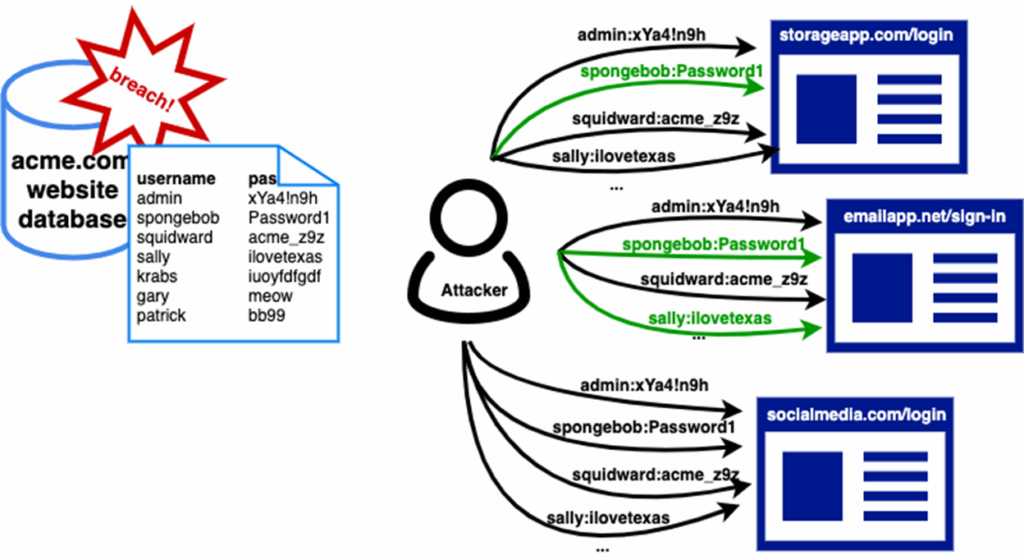
Figure 1: Credential stuffing attack flow [5]
Conclusion
The 23andMe case is a cautionary tale about the dangers of weak authentication and the gaps in privacy law. It shows why fines matter: without them, companies have little incentive to prioritize security.
Until privacy laws catch up, especially in Canada and the US, consumers remain vulnerable. And in the case of DNA data, once it’s stolen, there is no getting it back.
References
[1] A. Hern, “DNA testing firm 23andMe fined £2.3m by UK regulator for 2023 data hack,” The Guardian, Jun. 17, 2025. [Online]. Available: https://www.theguardian.com/technology/2025/jun/17/dna-testing-firm-23andme-fined-23m-by-uk-regulator-for-2023-data-hack
[2] A. L. Wolf, “23andMe fined millions for failing to protect customer data,” Cybersecurity Dive, Jun. 2025. [Online]. Available: https://www.cybersecuritydive.com/news/23andme-fined-ico-data-breach/723813/
[3] L. K. Guo, “23andMe Bankruptcy: What happens to your DNA data when a genetic testing giant fails?” Forbes, Jul. 10, 2025. [Online]. Available: https://www.forbes.com/sites/leslieguo/2025/07/10/23andme-bankruptcy-what-happens-to-your-dna-data
[4] R. Burgess, “UK watchdog fines 23andMe for ‘profoundly damaging’ data breach,” Wired UK, Jun. 18, 2025. [Online]. Available: https://www.wired.co.uk/article/23andme-uk-fine-data-breach
[5] OWASP Foundation, “Credential stuffing,” OWASP, 2024. [Online]. Available: https://owasp.org/www-community/attacks/Credential_stuffing
[6] OWASP Foundation, “Credential Stuffing Prevention – OWASP Cheat Sheet Series,” OWASP, 2024. [Online]. Available: https://cheatsheetseries.owasp.org/cheatsheets/Credential_Stuffing_Prevention_Cheat_Sheet.html
[7] Digital Samba, “How Much Overlap Is There Between GDPR in the EU, HIPAA in the US & PIPEDA in Canada?” Digital Samba Blog, Nov. 8, 2023. [Online]. Available: https://www.digitalsamba.com/blog/gdpr-vs-pipeda-vs-hipaa. [Accessed: 23-Sep-2025].


Great job Hillary. This is such an eye-opening post. I never really thought about how genetic data is in a completely different category, unlike a password or credit card, you can’t just ‘reset’ your DNA if it’s exposed. The fine makes sense, but it does make me wonder, do you think regulators should go beyond fines and start requiring stronger baseline security measures (like mandatory MFA or stricter password rules) for companies handling this kind of data? Otherwise, it feels like we’re always reacting after the fact.
Hi Joy, I completely agree that regulators should require mandatory MFA and stronger password policies. Part of the reason the UK was able to justify the fine is because they had clear evidence that, despite these being expected practices for organizations handling sensitive data, they weren’t consistently followed. Canada and the U.S. could definitely learn from this approach, not only to better protect user information, but also to make companies less vulnerable in the first place.
This was such an eye-opening read, Hilary. I personally categorize medical data as super highly sensitive because it can be exploited and manipulated on a lot of dangerous levels. Something that hit me while reading was the realization that genetic customers are classified separately from patients which is highly confusing because the business is medical and genetic services goes way beyond finding roots via DNA.
I absolutely agree that the law is weak and full of loopholes across regions, and I’m so sad to say that asides from strongly adopting the recommendations you have outlined, I do not see how we can put up defenses against this for the foreseeable future. Genetic data is so unique and sensitive (and specific to an individual) that people are ultimately on the wrong end of things, and a company like 23andMe can walk away on a technicality.
Thank you for sharing!
Thank you for your comment Dami!
It’s so interesting to have a look at medical data classification, and the types of data they protect and which ones are not covered. These companies are handling information that’s very personal, and very permanent. As mentioned in the post, you cannot change your DNA so it’s concerning that they’re not putting more thought into ensuring that this information remains secret on behalf of their users. The fines help, but it does not stop the problem. In my opinion, companies like 23andMe should absolutely be forced to put mandatory protections like MFA, encryption at rest, and breach detection protocols in place before being allowed to collect genetic data.
Thanks for sharing!
Hi Azeezat, I completely agree! Companies often get away with weaker security controls when operating across multiple countries. Thankfully, at least one regulator was able to hold them accountable. Still, all nations and private companies need to do better and hold themselves to a higher standard.
Quite shocking that the UK can fine 23andME, while United States and Canada can’t. I strongly believe DNA should be treated as a medical data worldwide because of how sensitive it is. Also, if my anonymised data can still be traced does the account ‘deletion’ really mean anything for end users? The credential stuffing angle is a bit disappointing, because it makes me question the company’s priorities. Since MFA can block most of these attacks, why wasn’t it made mandatory from the jumpstart?
Hi Gilberta,
I think all your concerns are completely valid. DNA should definitely be treated with more security and without better data laws in Canada/USA situations like these are bound to repeat themselves. Additionally, MFA was a requirement in the UK but not in USA and Canada due to how they categorize data collected by private organizations. It is an unfortunate mess to be honest!
The part on credential stuffing and weak authentication was revelatory. It’s mind-blowing that a company built solely around sensitive health data didn’t force multi-factor authentication to begin with. We’ve all been cautioned against ever reusing a password, but it’s always striking when such a vulnerable practice results in what is certainly one of the largest breaches to date. The post also connects the dots back to what we were taught in class about hashing and authentication, helping it make more sense why MFA and better monitoring need to just be assumptions. It is a textbook example of how basic security hygiene can stave off huge breaches.
Hi Ifeoma, I completely agree!
The fine imposed on 23andMe serves as a powerful reminder that inadequate authentication can lead to tangible consequences, particularly when the information at stake is permanent, such as DNA. In contrast to passwords, your genetic code cannot be reset once it has been revealed. Regulators were justified in their actions, yet the more significant problem is that legislation in the US and Canada still trails well behind Europe. Until privacy safeguards and enhanced authentication standards are widely adopted, consumers will continue to be at risk, and regarding DNA data, the risks could not be greater.
Hi Abdul, I completely agree!
It is amazing to see big companies still failing at the most basic level of security. This kind of incident is how you lose trust in a company. Regulations like GDPR and PIPEDA are important to maintain and abide by, but from the cybersecurity conference, there is still a lot of progress that needs to be made. Many companies still get away with not sharing their data breaches in Canada.
Hi Hicham, I completely agree!