ISEC 601 – FINAL GROUP TEACHING AID
List of Group Members: Pranshu Amin – 30302031; Hillary Ogoke – 30141713; Joy Aroh – 30302221; Israel Oni – 30085933; Mohammed Arab – 30129092
Introduction to E-Voting
For centuries, democratic elections have relied on paper ballots as the foundation of trust. Paper voting is simple, auditable, and familiar. Citizens can watch ballots being cast, counted, and stored. While this physical process is slow and costly, it offers a high degree of transparency and verifiability that has earned widespread public confidence.
In the digital age, however, governments and organizations have sought ways to make elections more accessible, efficient, and scalable. Electronic voting (e-voting) promises faster tallying, remote participation, and reduced administrative costs, while also offering the potential to strengthen security through cryptographic techniques such as encryption, digital signatures, homomorphic tallying, and zero-knowledge proofs [2]. Estonia is a leading example: since 2005, it has implemented nationwide Internet voting in eleven elections, giving researchers rich evidence of both its benefits and vulnerabilities [1].
Despite this promise, large-scale adoption of e-voting has been limited. Paper systems, though imperfect, are resistant to certain digital threats, whereas e-voting introduces new risks: malware on voter devices, insider manipulation of systems, denial-of-service attacks, and the challenge of balancing anonymity with verifiability [3][4]. Even advanced cryptographic systems, while powerful in theory, must contend with the realities of usability, scalability, and public trust.
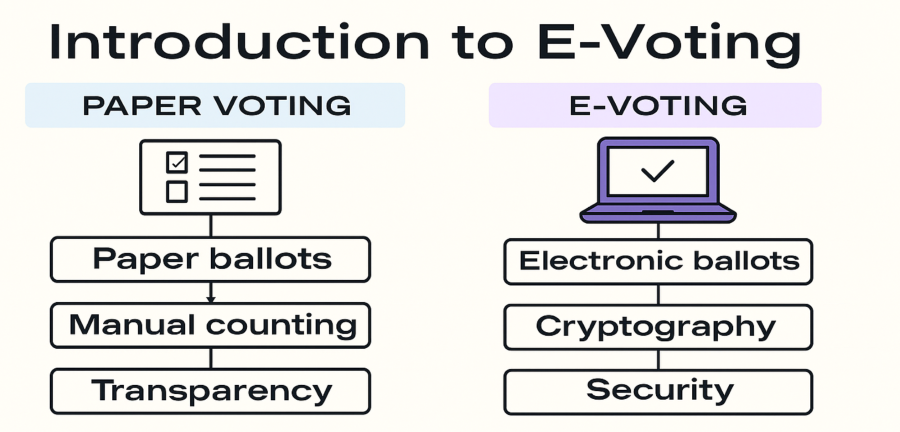
Figure 1: Flow diagram comparing traditional paper voting with electronic voting (created by the author using ChatGPT, 2025).
Our teaching aid is a website that brings these concepts to life. It allows you to step through a realistic voting simulation, explore the technical cryptographic mechanisms that secure e-voting, and experiment with an Attack Lab to see how vulnerabilities can compromise elections and how defenses work. This hands-on platform is designed to make complex concepts tangible, interactive, and easy to understand. Please read this pre-document completely before using the website, as it provides essential background that will help you grasp the concepts and get the most from the simulation and Attack Lab (Website link: https://evote-demo.netlify.app/).
Case Studies: Real-World Attempts at Electronic Voting
Electronic voting systems have been piloted or adopted in several countries, with mixed outcomes. These case studies highlight how cryptographic tools are used in practice and why secure, trustworthy e-voting remains difficult to achieve.
Estonia: A Long-Term Success Story
Estonia is the most prominent example of a national e-voting system, in use since 2005. Voters authenticate with a government-issued ID card containing a secure chip that stores a private key, which is used to digitally sign their encrypted ballot. The ballots are encrypted using public-key cryptography and anonymized through mix-nets before tallying. More recently, zero-knowledge proofs (ZKPs) such as Bulletproofs have been introduced to enhance verifiability [3].
As of the 2023 national parliamentary elections, more than 50% of Estonian voters cast ballots online [4]. Despite this success, concerns remain. Critics warn that malware on voters’ personal devices could alter votes before encryption, and remote voting cannot fully prevent coercion or vote buying. Newer research in 2025 also highlights traffic analysis inference attacks as a threat, since encrypted vote submission may still leak metadata [3]. Estonia demonstrates that strong cryptography can make national e-voting possible, but it cannot eliminate all risks.
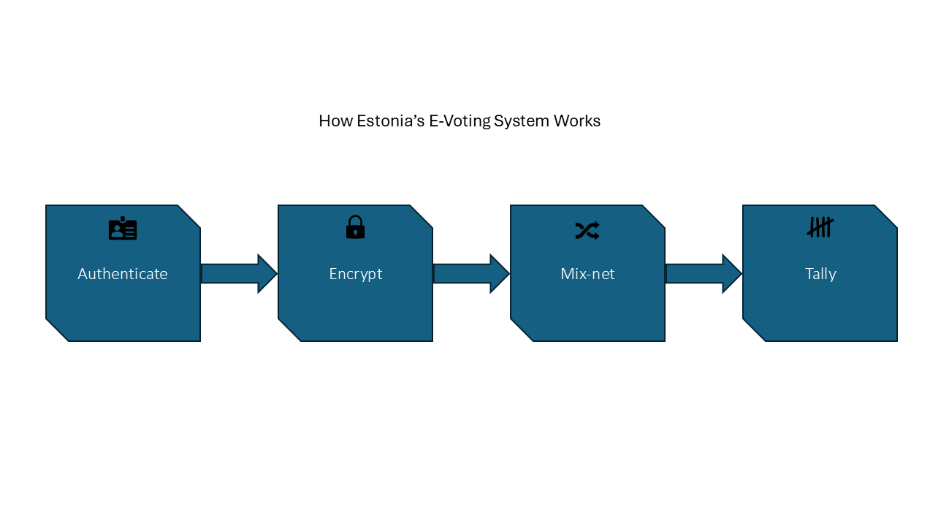
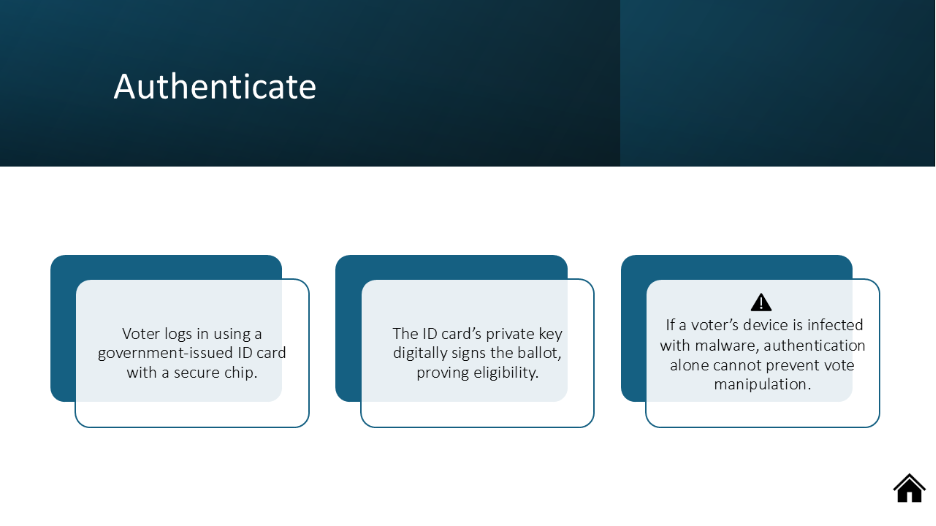
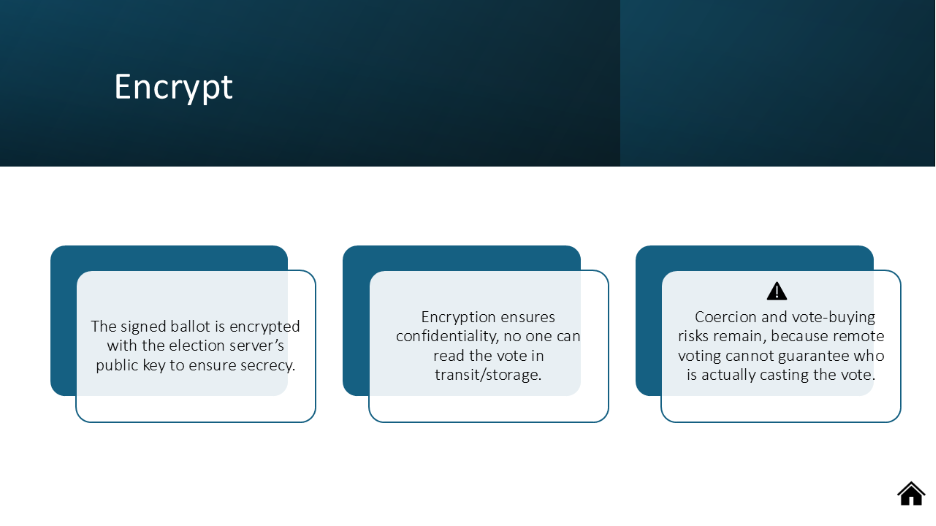

Figure 2: Interactive E-Voting Steps (created by Joy Aroh)
Switzerland: Ambition and Setbacks
Switzerland has long aimed to design an e-voting system with complete verifiability, relying on return codes and zero-knowledge proofs (ZKPs) to let voters and auditors confirm ballot integrity. However, in 2019 researchers uncovered serious flaws in the Swiss Post system. They demonstrated that votes could be altered without detection, breaking the guarantee of universal verifiability, and that protocol weaknesses in the mix-net could allow insiders to manipulate encrypted tallies while still producing valid-looking proofs [5], [6]. These findings forced the suspension of nationwide deployment and highlighted how even well-designed cryptographic systems can fail in implementation, shaking public trust.
Since 2023, Switzerland has cautiously relaunched e-voting through restricted cantonal trials under strict federal licences. These pilots include independent audits and public intrusion tests; a 2024 test logged nearly 10,000 hacking attempts with no critical breaches [7]. As of 2025, Switzerland continues limited e-voting trials in four cantons under renewed federal licences through 2027. Recent audits confirm improvements but flagged remaining cryptographic parameterization issues, and Swiss Post has launched a new public bug-bounty intrusion test to strengthen transparency and resilience [8], [9]. However, experts stress that the system’s complexity and trust assumptions remain barriers to wider rollout. Switzerland’s cautious progress underscores that cryptographic strength must be paired with transparency and incremental adoption to build durable public trust.
United States: Resistance to Internet Voting
The United States has largely rejected internet voting at the federal and state level, citing high risks to election integrity. Pilot projects such as Voatz, a blockchain-based mobile voting app, explored digital signatures and end-to-end verifiability. However, independent analyses by MIT researchers in 2020 found that Voatz was vulnerable to man-in-the-middle attacks, server-side manipulation, and metadata leakage that could reveal voter identities. These flaws meant ballots could potentially be altered or deanonymized, undermining both secrecy and integrity [10].
Federal authorities, including the National Institute of Standards and Technology (NIST) and the Cybersecurity and Infrastructure Security Agency (CISA), classify electronic ballot return as “high risk.” Instead, the U.S. continues to emphasize paper ballots and risk-limiting audits as more trustworthy safeguards [11]. While academic proposals for blockchain and homomorphic tallying persist, experts agree these approaches do not solve challenges like coercion, malware, and denial-of-service attacks [12]. The U.S. case shows that in a high-threat environment, cryptography alone cannot overcome the operational and societal risks of online voting.
Cryptographic Foundations of Secure E-Voting
For an e-voting system to be trusted, it must guarantee more than just efficient vote casting and counting. It must enforce fundamental security properties that ensure integrity, privacy, fairness, and verifiability of the electoral process. The following table summarizes the core security requirements of e-voting systems and shows why cryptography is indispensable for achieving them. These properties form the foundation upon which encryption, digital signatures, mix-nets, homomorphic tallying, and other cryptographic tools are applied.
Table 1: Core Security Properties in Cryptographic E-Voting Systems
| Property | Description | Citation |
| Non-repudiation | A voter cannot later claim they did not cast a vote. | [16] |
| Integrity | Ensures that the vote remains unchanged during transmission or storage and prevents impersonation of voters. | [16] |
| Confidentiality / Privacy | No one should be able to link a voter’s identity to their vote. | [16] |
| Authentication / Legality | Ensures that only valid voters can vote. | [16] |
| Uniqueness | Each voter ID must be unique, ensuring that no voter can cast more than one ballot. | [16] |
| Verifiable | After the results are announced, the votes should be verifiable by both auditors and voters. | [16] |
| Impartiality | Only trusted authorities can decrypt the votes; other participants should not have access. | [16] |
| Coercion resistance | Ballots are cast without any external pressure or coercion on voters. | [17] |
| Receipt freeness | Voters cannot prove how they voted. | [17] |
To make these security properties possible, e-voting systems rely on several cryptographic building blocks:
- Key generation involves creating elliptic curve key pairs for both the authority and the users. For the authority, the public key is shared among multiple authorities as part of a threshold secret sharing scheme, which helps prevent corruption during the voting process. Additionally, a verification mechanism allows each authority to mathematically verify their own key shares, ensuring correctness and integrity [15].
- Blind signatures allow voters to have their votes authenticated without the authorities ever seeing their actual choices. While homomorphic encryption can authenticate users, it may link a voter to their selection. With blind signatures, the authority signs the vote using its share of private keys, and the voter also signs it with their private key. Before submission, the vote is blinded, ensuring that the authority cannot determine who voted for whom, thereby preserving voter anonymity [15].
- Encryption & Decryption – Although homomorphic encryption is utilized, the actual encryption method for casting votes is asymmetric RSA encryption. Voters encrypt their ballots using the authority’s public key then sign it with their private key. After the votes are tallied, the authority combines their key shares to reconstruct the private key and decrypt the results [15].
- Homomorphic encryptions enable computations to be performed directly on encrypted data without the need for decryption. In the context of voting, this allows authorities to extract aggregate information while keeping individual ballots private. For example, additive homomorphic encryption (also known as Paillier encryption) allows the authority to compute the total number of votes for a candidate without revealing how each individual voted. Multiplicative homomorphic encryption (also known as ElGamal encryption) can be used to calculate the product of votes [14].
In most cases, a partial homomorphic encryption scheme is sufficient, as it supports only one type of operation on the ciphertext. Fully homomorphic encryption is also possible, but it requires significantly more computational resources [14].
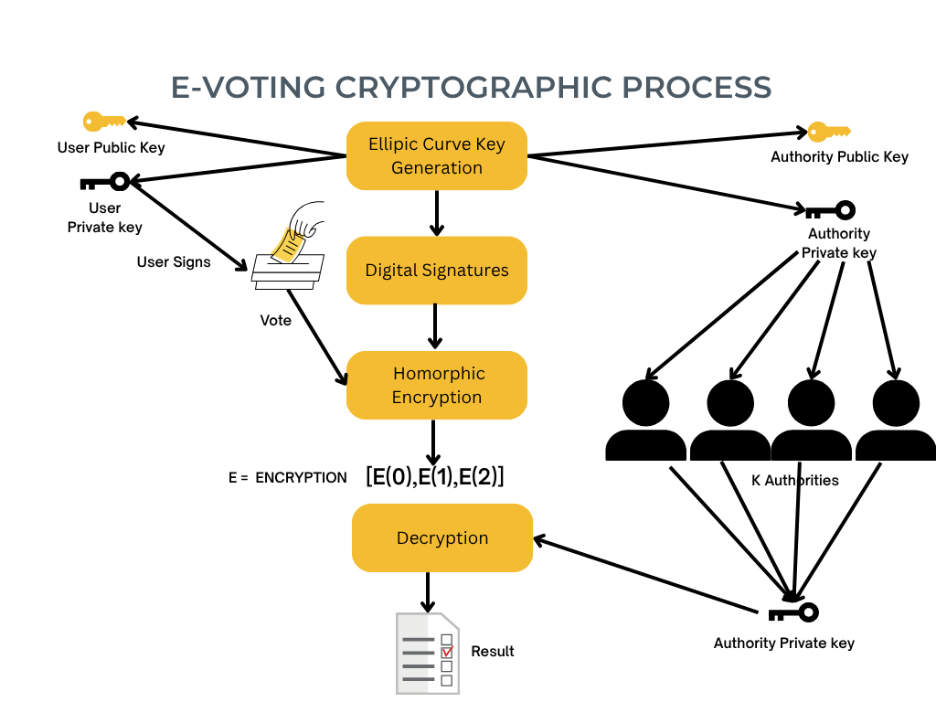
Figure 2. E-voting cryptographic process illustrating key generation, digital signatures, homomorphic encryption, and threshold decryption by multiple authorities to produce verifiable results (created by Israel Oni).
Challenges in Secure E-Voting
Even with strong cryptographic foundations, electronic voting systems face real-world challenges that complicate secure deployment. These challenges arise not only from technical constraints but also from human, organizational, and political factors. The table below summarizes the key challenges in e-voting, their impact, and some mitigation strategies with real-world examples.
Table 2: Challenges in Electronic Voting Systems
| Challenge | Description | Mitigation | Example/Facts |
| Anonymity vs. Verifiability | Anonymity protects voter privacy, while verifiability allows voters and auditors to confirm that votes are correctly tallied. Achieving both simultaneously is technically hard because stronger verifiability can weaken anonymity. | Use cryptographic protocols like homomorphic tallying, and zero-knowledge proofs to balance both goals [21]. | In Estonia’s e-voting system, encrypted votes are separated from voter signatures and processed through a mix-net that re-encrypts and shuffles them, generating a proof of correct permutation to preserve voter anonymity while enabling verifiability [22]. |
| Malware on Voter Devices | Remote voting depends on personal devices (phones, PCs), which may be infected with malware that alters, blocks, or leaks votes before encryption. Cryptography cannot fix an already compromised client [21]. | Encourage supervised polling stations or trusted hardware tokens. Provide independent verification channels such as out-of-band confirmation codes. | In 2010, researchers hacked Washington, D.C.’s online voting pilot within 48 hours, changing ballots and adding the university fight song [23]. |
| Coercion and Vote Buying | Without supervised polling places, voters at home may be pressured or bribed. If receipts reveal votes, it becomes easy to sell votes. | Design receipt-free systems and coercion-resistant protocols, such as Benaloh challenges or re-voting mechanisms that allow a coerced vote to be overridden later [21]. | Studies show remote voting environments make voters vulnerable to subtle family or workplace coercion [24]. |
| Insider Threats | Election officials or system operators may abuse their privileged access to alter results, leak data, or weaken safeguards. Insiders are often harder to detect than outsiders. | Use distributed trust models (e.g., threshold cryptography) so no single authority can manipulate results [21]. | In demonstrations, insider misuses are often simulated by toggles (e.g., key misuse) in teaching systems to show loss of integrity. |
| Denial-of-Service (DoS) Attacks | Attackers can flood servers or bulletin boards to prevent voters from casting or verifying ballots, undermining availability. | Use load balancing, redundancy, and decentralized infrastructures like peer-to-peer bulletin boards. | Large-scale DoS attacks have targeted online services during elections in multiple countries, delaying access to voting portals [24]. |
| Compromised Random Number Generator | Weak or predictable randomness can leak information about encrypted ballots or break zero-knowledge proofs. | Use audited, verifiable randomness sources (e.g., publicly observable beacons). | In Swiss e-voting trials, flaws in randomness generation weakened ballot secrecy, contributing to suspension of trials [7]. |
| Scalability | National elections involve millions of votes, requiring secure cryptographic operations at a scale. Performance bottlenecks can reduce usability and availability. | Optimize with efficient protocols (e.g., elliptic curve cryptography, batch verification). | Estonia’s e-voting system achieved large-scale adoption by simplifying its cryptographic design, but it continues to face criticism due to remaining security vulnerabilities [24]. |
| Trust and Public Confidence | Even if cryptographically secure, systems must be perceived as fair and transparent. Public mistrust can invalidate an otherwise working system. | Use open-source software, third-party audits, and voter-verifiable protocols to build confidence. | Switzerland suspended its e-voting program in 2019 after researchers revealed vulnerabilities, undermining trust [25]. |
Glossary
| Term | Description |
| ECDSA (Elliptic Curve Digital Signature Algorithm) | A digital signature scheme based on elliptic curve cryptography. It is used to verify authenticity and ensure that data has not been tampered with. |
| NPC (Non-Playable Character) | A simulated voter controlled by the system, not by a real person. NPCs are used in the demo to model realistic voting behavior without requiring live participants. |
| OAEP (Optimal Asymmetric Encryption Padding) | A padding scheme used with RSA encryption to make it more secure and prevent certain types of attacks, such as chosen ciphertext attacks. |
| PEM (Privacy-Enhanced Mail) | Originally a standard for secure email, today PEM mostly refers to the Base64-encoded file format used to store and share cryptographic keys and certificates (e.g., public/private keys). |
| RSA-OAEP (Rivest–Shamir–Adleman with Optimal Asymmetric Encryption Padding) | A secure encryption method that combines RSA public-key cryptography with OAEP padding, providing stronger protection for encrypted data such as ballots or keys. |
| SHA-256 (Secure Hash Algorithm 256-bit) | A cryptographic hash function that produces a fixed-length 256-bit digest. It is widely used to ensure data integrity, as even the smallest change in input produces a completely different output. |
Citations
[1] P. Ehin, “Internet voting in Estonia 2005–2019: Evidence from eleven elections,” ResearchGate, 2022. [Online]. Available: https://www.researchgate.net/publication/361335825_Internet_voting_in_Estonia_2005-2019_Evidence_from_eleven_elections. [Accessed: Sep. 19, 2025].
[2] S. T. Ali and J. Murray, “An Overview of End-to-End Verifiable Voting Systems,” in Real-World Electronic Voting: Design, Analysis and Deployment, F. Hao and P. Y. A. Ryan, Eds. Boca Raton, FL, USA: CRC Press, 2016, pp. 173–217. doi: 10.1201/9781315371290.
[3] P. Ehin, M. Solvak, J. Willemson, and P. Vinkel, “Internet voting in Estonia 2005–2019: Evidence from eleven elections,” Government Information Quarterly, vol. 39, no. 4, p. 101718, Oct. 2022, doi: 10.1016/j.giq.2022.101718.
[4] E. Piirmets, “How did Estonia carry out the world’s first mostly online national elections,” e-Estonia, Mar. 07, 2023. [Online]. Available: https://e-estonia.com/how-did-estonia-carry-out-the-worlds-first-mostly-online-national-elections/. [Accessed: Sep. 25, 2025].
[5] A. Belousova, F. Marchiori, and M. Conti, “Inference attacks on encrypted online voting via traffic analysis,” arXiv.org, 2025. [Online]. Available: https://arxiv.org/abs/2509.15694v1. [Accessed: Sep. 25, 2025].
[6] Swiss Federal Chancellery, “Release of source code leads to discovery of flaw in Swiss Post’s new e-voting system,” Admin.ch, 2019. [Online]. Available: https://www.news.admin.ch/en/nsb?id=74307. [Accessed: Sep. 25, 2025].
[7] SWI swissinfo.ch, “Hackers uncover ‘significant’ flaw in Swiss Post e-voting,” SWI swissinfo.ch, Mar. 12, 2019. [Online]. Available: https://www.swissinfo.ch/eng/politics/universal-verifiability-_hackers-uncover-significant-flaw-in-swiss-post-e-voting/44818224. [Accessed: Sep. 25, 2025].
[8] SWI swissinfo.ch, “Hackers find only minor issues with Swiss Post’s e-voting system,” SWI swissinfo.ch, Aug. 08, 2024. [Online]. Available: https://www.swissinfo.ch/eng/democracy/hackers-find-just-minor-issues-with-swiss-posts-e-voting-system/86396893. [Accessed: Sep. 25, 2025].
[9] Swiss Federal Chancellery, “The Federal Council renews basic licences for online voting,” Admin.ch, 2025. [Online]. Available: https://www.news.admin.ch/en/newnsb/ZLw6w1GV_UdJKDocuT0sX. [Accessed: Sep. 25, 2025].
[10] Swiss Post, “Cyber attackers sought: Swiss Post begins endurance test for e-voting system,” Swiss Post, Jul. 28, 2025. [Online]. Available: https://digital-solutions.post.ch/en/e-government/blog/cyber-attackers-sought-swiss-post-begins-endurance-test-for-e-voting-system. [Accessed: Sep. 25, 2025].
[11] M. Specter, J. Koppel, and D. Weitzner, “The Ballot is Busted Before the Blockchain: A Security Analysis of Voatz, the First Internet Voting Application Used in U.S. Federal Elections,” Massachusetts Institute of Technology, Tech. Rep., Feb. 2020. [Online]. Available: https://internetpolicy.mit.edu/wp-content/uploads/2020/02/SecurityAnalysisOfVoatz_Public.pdf.
[12] Cybersecurity and Infrastructure Security Agency (CISA), “Risk management for electronic ballot delivery, marking, and return,” CISA.gov, May 08, 2020. [Online]. Available: https://www.cisa.gov/resources-tools/resources/risk-management-electronic-ballot-delivery-marking-and-return. [Accessed: Sep. 26, 2025].
[13] S. Chouhan and G. Sharma, “A New Era of Elections: Leveraging Blockchain for Fair and Transparent Voting,” arXiv.org, 2025. [Online]. Available: https://arxiv.org/abs/2502.16127. [Accessed: Sep. 26, 2025].
[14] J.-J. Chin, “A Review of Cryptographic Electronic Voting,” Symmetry, vol. 14, no. 5, article 858, 2022. doi: 10.3390/sym14050858. [Online]. Available: https://www.mdpi.com/2073-8994/14/5/858. [Accessed: Sep. 28, 2025].
[15] Y.-X. Kho, S.-H. Heng, and J.-J. Chin, “A Review of Cryptographic Electronic Voting,” Symmetry, vol. 14, no. 5, p. 858, 2022. doi: 10.3390/sym14050858. [Online]. Available: https://doi.org/10.3390/sym14050858. [Accessed: Sep. 29, 2025].
[16] L. Li, “An Electronic Voting Scheme Based on ElGamal Homomorphic Encryption for Privacy Protection,” Journal of Physics: Conference Series, vol. 1544, no. 1, p. 012036, 2020. doi: 10.1088/1742-6596/1544/1/012036. [Online]. Available: https://doi.org/10.1088/1742-6596/1544/1/012036. [Accessed: Sep. 29, 2025].
[17] S. Park, J. Choi, J. Kim, and H. Oh, “A New Threshold Homomorphic Encryption Scheme for Secure Voting,” IACR Cryptology ePrint Archive, Report 2024/1003, 2024. [Online]. Available: http://eprint.iacr.org/2024/1003.pdf. [Accessed: Sep. 29, 2025].
[18] D. F. Aranha, H. Ribeiro, and A. L. O. Paraense, “Crowdsourced integrity verification of election results: An experience from Brazilian elections,” ResearchGate. [Online]. Available: https://www.researchgate.net/publication/299424370_Crowdsourced_integrity_verification_of_election_results_An_experience_from_Brazilian_elections. [Accessed: Sep. 28, 2025].
[19] S. Bell, J. Benaloh, M. D. Byrne, D. DeBeauvoir, B. Eakin, G. Fisher, P. Kortum, N. McBurnett, J. Montoya, M. Parker, O. Pereira, P. B. Stark, D. S. Wallach, and M. Winn, “STAR-Vote: A Secure, Transparent, Auditable, and Reliable Voting System,” USENIX Journal of Election Technology and Systems (JETS), vol. 1, no. 1, Aug. 2013. [Online]. Available: https://www.usenix.org/system/files/conference/evtwote13/jets-0101-bell.pdf. [Accessed: Sep. 28, 2025].
[20] F. Zhang and K. Kim, “ID-Based Blind Signature and Ring Signature from Pairings,” in Advances in Cryptology — ASIACRYPT 2002, Lecture Notes in Computer Science, vol. 2501, pp. 533–547, 2002. doi: 10.1007/3-540-36178-2_33. [Online]. Available: https://www.iacr.org/archive/asiacrypt2002/25010533/25010533.pdf. [Accessed: Sep. 28, 2025].
[21] A. Belousova, F. Marchiori, and M. Conti, “Inference attacks on encrypted online voting via traffic analysis,” arXiv preprint arXiv:2509.15694, 2025. [Online]. Available: https://arxiv.org/abs/2509.15694v1. [Accessed: Sep. 25, 2025].
[22] A. Rebane, “E-voting,” Infoturve (Information Security), University of Tartu, 2021. [Online]. Available: https://courses.cs.ut.ee/2021/infsec/fall/main/e-voting. [Accessed: Sep. 25, 2025].
[23] H. Halderman, S. Wolchok, and E. Wustrow, “Attacking the Washington, D.C. Internet Voting System,” in Proc. Financial Cryptography and Data Security (FC), 2012. [Online]. Available: https://ericw.us/trow/dc-internet-voting-fc.pdf. [Accessed: Sep. 25, 2025].
[24] R. Carback and A. Sherman, “Observations from Scantegrity and other remote voting trials,” UMBC Technical Report, 2009. [Online]. Available: https://cisa.umbc.edu/wp-content/uploads/sites/468/2017/09/carback_sherman_TISF09.pdf. [Accessed: Sep. 25, 2025].
[25] Swiss Post, “E-Voting – Electronic vote casting for Switzerland,” Swiss Post, 2019. [Online]. Available: https://www.post.ch/en/about-us/profile/swiss-post-and-politics/swiss-post-in-the-digital-world/e-voting-electronic-vote-casting-for-switzerland. [Accessed: Sep. 25, 2025].


Teaching Aid Walk Through: https://youtu.be/-4pxgpYrzxE
DISSCUSION QUESTIONS
1) To what extent can future online voting systems ensure privacy, authentication, and the integrity of votes?
2) Considering the significant resources required, is pursuing secure and truly anonymous online voting a worthwhile investment?
3) Even with strong security measures, can online voting realistically address concerns such as voter coercion or vote buying in unsupervised settings?
4) Should the management of online voting systems rest with a trusted central authority, or would decentralized approaches such as blockchain offer greater protection against conflicts of interest?
5) In what ways might online voting enhance accessibility and participation for groups facing barriers to traditional voting, such as individuals with disabilities or citizens living abroad?