Group: Angelica Hizsa, Teddy Kalp, Lisa Muli
The practice of securing communication by transforming plaintext into unreadable ciphertext, and vice versa, using mathematical algorithms and secret keys…What is Cryptography?
Introduction
So… Let’s talk about the exciting world of Cryptography, demystify the belief of its complexity, build on fundamental knowledge and challenge you to learn more about the fundamental, objectives, uses, methods and even humor regarding cryptography. How about we make a game of it and test your knowledge as you attempt to gain the highest score, in a game of Jeopardy. Each round will have category specific questions in the form of statements and answers required in the form of questions. Are you up for the challenge? What if we make it even more interesting and specialize the game to see how much you know about blockchains?

Blockchain of Trust
So why did we select blockchain as the specialty topic for our Jeopardy game? Blockchain technology is a revolutionary new way of storing and transferring data that is quickly gaining traction in a wide range of industries. At its core, blockchain combines cryptographic techniques and a decentralized architecture to provide three key features: confidentiality, integrity, and availability (CIA Triad).
Confidentiality is maintained through the use of public-key cryptography. Each participant in the blockchain network has a unique pair of keys, one public and one private. The public key is used to encrypt data, while the private key is used to decrypt it. This ensures that only authorized parties can access the information stored on the blockchain.
Integrity is maintained by using a hash function to create a unique digital fingerprint of each block in the chain. This fingerprint, or hash, is based on the data contained in the block and the hash of the previous block in the chain. This creates a tamper-evident chain that ensures that the data stored on the blockchain is valid and has not been altered. Additionally, a consensus mechanism is used to ensure that only valid transactions are added to the blockchain.
Finally, availability is provided by the decentralized nature of the blockchain. The public ledger is spread across multiple nodes in the network, ensuring that the network can continue to function and the data remains accessible even if one node goes offline. This also ensures that there is no single point of failure in the system, making it highly resilient and redundant.
For our project, we not only want to test out the knowledge of these foundations but also integrate some of the most interesting use cases for Blockchains and the type of material that will be found in the game
- Decentralization: The distributed nature of blockchain technology, where transactions are recorded across multiple nodes on a network, consequently eliminating the need for a central authority or intermediary.
- Consensus algorithms: The mechanisms by which the network reaches agreement on the state of the blockchain. Common examples include: Proof of Work, Proof of Stake, Proof of Authority
- Smart Contracts: Self-executing contracts with the terms of the agreement directly written into lines of code and stored within blocks on the network.
- Distributed Ledger Technology: A digital record-keeping system where multiple copies of a ledger are spread across a network of peers.
- Cryptography: This is crypto jeopardy, isn’t it?
- Tokenization: The process of creating a digital token, typically on a blockchain, that can represent a variety of assets. Most commonly known as the “NFTs” or as we like to call them “digital monkeys”
- Privacy and Anonymity: Techniques that protect the identity and transactional data of individuals and organizations using the cryptographic techniques used in blockchain networks
…..and many more, we don’t want to spoil the whole game for you.

Jeopardy Style
To further elaborate, a programmable game was selected as research showed it is a promising teaching approach that aids in fostering student learning, as well has shown to be an effective learning tool. The main focus is to share in-depth knowledge with users through a point based incentive structure ideally aiding in the retention of information that may or may not aid in correctly answering further complex questions. The game audience and users are assumed to be students or scholars but can be enjoyed by anyone with an interest or base knowledge of Cryptography.
Originally, there was no theme to convey the overall importance of Cryptography. The game had a multitude of random categories varying in topics all under the subject of cryptography. There was no shortage of research materials, but focus was lost, the game felt disorganized, and questions felt to be more complex. So a version theme was added, becoming the driver to questions, correlating categories sand overall giving the game a more focused feel. Now, with theme fundamental categories are present in addition to themed categorizes correlated to blockchain.
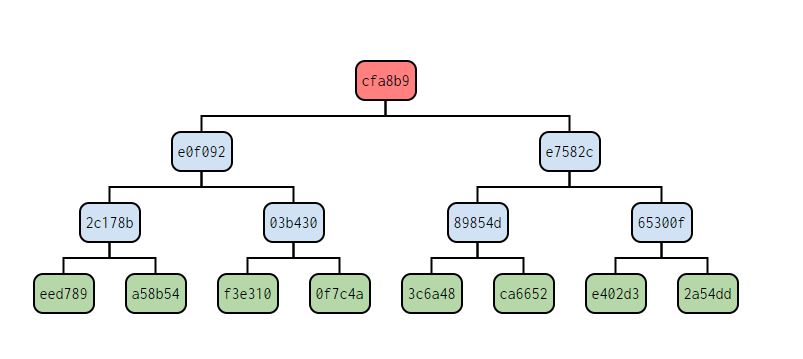
Merkle Trees
In addition, we have also added a Merkle Tree as a means of validation to the game and demonstrating a crucial component of blockchains. A Merkle Tree is a type of data structure that is used to validate the integrity of data in a distributed system. It works by taking a set of data, such as the clues and answers to the questions in a jeopardy game, and creating a hash of each piece of data. These hashes are then combined in pairs to create a new set of hashes, and this process is repeated until a single hash, called the root hash, is generated. We have chosen the SHA256 hashing algorithm to continuously hash these values. Now we can use this root hash as a fingerprint of the entire set of data, and any changes to the data can be detected by comparing the root hash to a previously recorded value. Not only this, but we can validate that answers are correct to clue by checking the proof against the Merkle Tree.
By implementing a Merkle Tree within our jeopardy game, it provides a way to ensure the integrity of the answers data and prevent malicious actors from tampering with it. This means that players can have confidence that the game is fair and that all players are playing on a level playing field.
Good Luck!
Remember that questions are category specific and the higher the points value the greater the complexity. Here’s a sneak peak of your challenge:
The game is currently in alpha development and will come out on Feb 3rd, make sure to come and test your knowledge!
Keep an eye out in the comments sections for the announcement of the release! We would also love suggestions from you, our peers, on what features you would like to see in this game. These can be cryptographically related or just something you are really keen on wanting to have in the game, all is welcome!
Source Code: https://github.com/tkalp/CryptoJeopardy
Bibliography
- T. Ali Syed, A. Alzahrani, S. Jan, M. S. Siddiqui, A. Nadeem and T. Alghamdi (2019), “A Comparative Analysis of Blockchain Architecture and its Applications: Problems and Recommendations,” in IEEE Access, vol. 7, pp. 176838-176869, 2019, doi: 10.1109/ACCESS.2019.2957660.
- Justinia T. (2019) Blockchain Technologies: Opportunities for Solving Real-World Problems in Healthcare and Biomedical Sciences. Acta Inform Med. 2019 Dec;27(4):284-291. doi: 10.5455/aim.2019.27.284-291. PMID: 32055097; PMCID: PMC7004292.
- Martinez, L., Gimenes, M., & Lambert, E. (2022). Entertainment Video Games for Academic Learning: A Systematic Review. Journal of Educational Computing Research, 60(5), 1083–1109. https://doi.org/10.1177/07356331211053848
- Monrat, A. A., Schelén, O., & Andersson, K. (2019). A survey of blockchain from the perspectives of applications, challenges, and opportunities. IEEE Access, 7, 117134-117151.
- Gamage, H. T. M., Weerasinghe, H. D., & Dias, N. G. J. (2020). A survey on blockchain technology concepts, applications, and issues. SN Computer Science, 1, 1-15.
- Yaga, D., Mell, P., Roby, N., & Scarfone, K. (2019). Blockchain technology overview. arXiv preprint arXiv:1906.11078.
- Massey, J. L. (1986). Cryptography—A selective survey. Digital Communications, 85, 3-25.

This is great! I’d like to try it, hopefully soon. Good job, guys 🙂
Interesting blog! I love watching jeopardy game because its educative so I’ll be waiting to test my knowledge on the crypto jeopardy.
Wow!! I eagerly look forward to trying my hands on it.
Wow! What a creative project! It’s super impressive that you guys coded your own Jeopardy game and implemented a Merkle tree.
I have one question about the blockchain basics introduced here. You mention that each participant in the blockchain has a pair of public and private keys. What exactly can each user decrypt with their private keys? Can they decrypt all information put into the blockchain by other users, or just some of it? If it’s just some of it, how is it determined who can decrypt what?
Hey!
That’s a great question! When I think of private and public keys on the blockchain, I think of them like this. Public keys are typically how you can identify entities within the blockchain using something like a wallet address. These addresses are publicly known so that anyone can encrypt messages using your public key. Private keys are used to sign transactions to prove that crypto assets that are being transferred are legitimate.
For example, let’s say Alice wants to send some crypto assets to Bob in a blockchain network.
1. Alice would generate a private and corresponding public key, which acts as an address on the network. On the Ethereum network it would be in some hex form e.g. 0x123…
2. Bob would also generate his own private and public key. Alice will know Bob’s public key and use it as the destination address for the transaction.
3. Alice would then use her private key to sign a transaction that transfers the crypto assets from her address to Bob’s address (Bob’s public key)
4. The transaction is then broadcasted to the network, and all of the nodes would verify the signature using Alice’s public key.
5. Once the transaction is confirmed, Bob can now access the fund using his private key.
Hope this example helps you understand how private/public keys on blockchain networks, they are used to be able to transfer, access, and verify crypto funds.
Thank you so much for this clear and detailed reply Teddy! That clarifies it for me.
Hey!
That’s a great question! When I think of private and public keys on the blockchain, I think of them like this. Public keys are typically how you can identify entities within the blockchain using something like a wallet address. These addresses are publicly known so that anyone can encrypt messages using your public key. Private keys are used to sign transactions to prove that crypto assets that are being transferred are legitimate.
For example, let’s say Alice wants to send some crypto assets to Bob in a blockchain network.
1. Alice would generate a private and corresponding public key, which acts as an address on the network. On the Ethereum network it would be in some hex form e.g. 0x123…
2. Bob would also generate his own private and public key. Alice will know Bob’s public key and use it as the destination address for the transaction.
3. Alice would then use her private key to sign a transaction that transfers the crypto assets from her address to Bob’s address (Bob’s public key)
4. The transaction is then broadcasted to the network, and all of the nodes would verify the signature using Alice’s public key.
5. Once the transaction is confirmed, Bob can now access the fund using his private key.
Hope this example helps you understand how private/public keys on blockchain networks, they are used to be able to transfer, access, and verify crypto funds.
Wow, I am impressed by the idea of learning about cryptography and blockchain through Crypto Jeopardy. The game appears to be a highly interactive and engaging way to understand this complex subject. As a suggestion, will you consider incorporating real-world examples into the game? This may make the game even more relevant and practical.
That’s a great suggestion, we will be planning on including some real-world scenarios within the game to test your knoweledge!
I’m looking forward to trying it out later 🙂
No breaking it! Just kidding 🙂
Amazing project!! Jeopardy game sounds like an exciting way to learn about cryptography and blockchain technology. I can’t wait to give it a try and test my knowledge.
Nice! I love your project. My favorite part is the Merkle Tree representation as it is such a slick concept and it’s just really cool that you chose to include it in the game.
Will you guys put a link to a tool to allow patrons to hash using the SHA-256 function? I think it would be helpful as you are also targeting curious persons with very limited knowledge (or hopefully no knowledge), who may not know that they can easily verify your hash values or even experiment with hashing their own strings.
That’s an awesome idea! I think that having a tool that can showcase using a SHA256 hash function would be really helpful to those that are unfamiliar with the concept. Also would allow players to verify the hash values used for the game. We will be including a small info screen on how to read the Merkle Tree showcased in the game, but a tool to play around with would be a nice addition.
Very cool how your group decided to create a Jeopardy game and implement a cryptography scheme to secure the actual game itself. I look forward to trying out your game!
Have you guys tried playing the game? What categories your find useful or fun? I myself found confidentialty, integrity may seem simple, their concepts are more precise and somewhat different from general conception in terms of Blockchain. You are encouraged to try out those categories. And have you hit any Daily Doubles?
Seems like and interesting Idea I could see this being used for online tests to store answers and an uncorruptible format. The one suggestion I would make; if you think it would help, would be to store payouts to questions in the same way. So you can trace back what question where normal and what ones are worth double. That way you can make sure the they are not cooking the books on the score.
That’s a great idea! Good additional layer of providing integrity for the game
OMG, this is so cool. I cant wait for the big announcement to play the game.
Cool game. Sounds fun and we learn also at the same time. Waiting for the announcement.
very informative blog. I have learned about blockchain jeopardy. I would like to try out the game that you guys are building.
Blog was so informative and creative with fun stuff…. Great work guys
Wow, you guys this is such a neat idea. Very creative. I feel like I’m going to learn something if I get to try out your game. Well done!
Woah.. Jeopardy game sounds interesting. Looking forward to try it out. Also the blog is amazing, to the point and easy to understand, the game is adding more to it.
As we are doing the jeopardy questions, i think the most difficult are to formulate questions that are kids, grandparents friendly. We focus on block chain, which is not so easy to explain, even to tech people. We managed to have some such questions though. And we try to add some funny questions.
I will be up next week and am offering a Coffee & snack prize to the person with the highest score! Please submit your highest score to teams for consideration.
Thank you, everyone!
Hi,
Thank you for your blog post. Your blog post is very interesting. I am most interested in Merkle Trees. It really can keep the integrity of information in each block. And the game you post is very fun.
My concerns are if each time a data to be used or revealed, it needs a lot of computational requirements for the validation. Will it massively reduce the speed of system when a Merkle Tree is very big. Will it consume too much energy to validate? That could effect the running of other processes.