
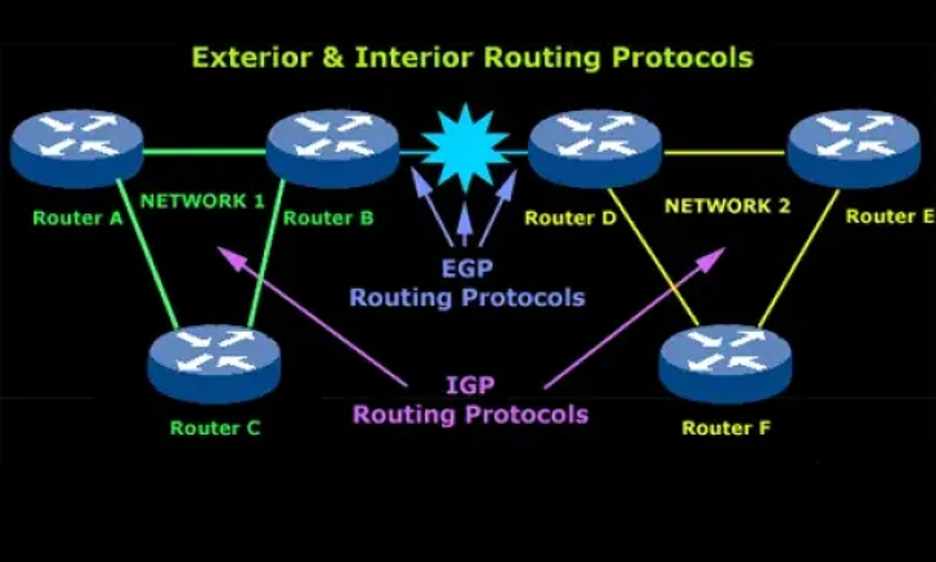
Understanding how routers communicate is crucial for maintaining secure and reliable networks. Throughout this teaching aide, you will gain insights into two primary types of routing protocols: Interior Gateway Protocols (IGP) like OSPF, which operate within a single organization, and Exterior Gateway Protocols (EGP) like BGP, which manage routing between different autonomous systems.
What You Will Learn
We will cover:
- OSPF’s Link State Routing Algorithm: This allows routers to calculate the best routes independently.
- BGP’s Path-Vector Mechanism: This manages routing across the internet.
Real-world case studies will also be highlighted, such as the notable 2010 incident where Pakistan Telecom accidentally redirected YouTube traffic, resulting in a significant outage. In our presentation we will go through the incident timeline, understanding the cause, effect & how it was resolved.
Why This Topic Matters
Routing protocols form the backbone of network operations, allowing routers to communicate with each other efficiently. However, they also present unique security challenges that malicious actors can exploit.
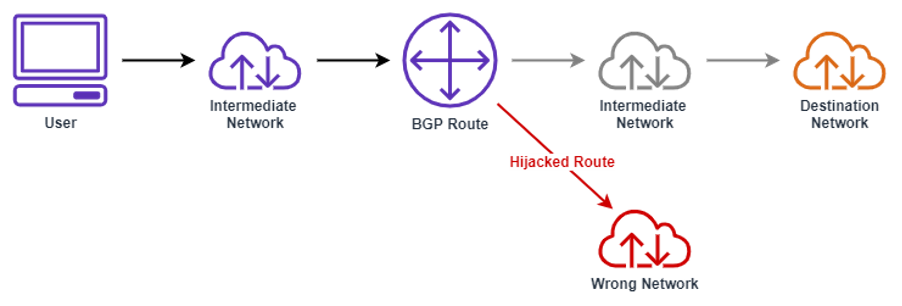
For example, BGP hijacking enables attackers to reroute traffic by falsely claiming ownership of IP addresses, leading to severe consequences such as data breaches and service disruptions. Our aide thoroughly explores these threats, & particularly explores the attacks that happened, detailing how they occur and their potential fallout, including revenue loss and reputational damage.
- Vulnerabilities are not limited to external protocols like BGP; OSPF also poses significant security challenges that require attention.
- Our focus will be on OSPF, which is primarily designed for internal network operations, highlighting its potential vulnerabilities.
- While there have been no documented cases of OSPF spoofing leading to outages, it is important to note that a critical vulnerability was discovered due to the improper implementation of OSPF in Cisco devices.
- When routing updates are compromised, attackers gain the ability to intercept sensitive data and manipulate the flow of network traffic, which can have serious implications.
- These risks underscore the necessity for secure configurations of OSPF routing settings, as well as the importance of routine monitoring to ensure data integrity and maintain reliable service availability.
Our teaching aide is designed to be interactive and engaging. It features detailed slides, real-world case studies, and activities that encourage exploration of routing protocols and security strategies.
Engagement Activity
To deepen your understanding, we have designed a hands-on activity:
Activity Title: Exploring Alternative Routing Protocols
Objective: Research and analyze an alternative routing protocol, such as RIP (Routing Information Protocol) or IS-IS (Intermediate System to Intermediate System), focusing on its security strengths and weaknesses compared to OSPF.
Conclusion
In summary, this teaching aide empowers you with valuable knowledge about routing protocols and network security. By exploring the intricacies of OSPF and BGP, understanding their vulnerabilities, and learning best practices, you will be better equipped to contribute to a secure digital environment.
Let us embark on this journey together—your insights and curiosity are key to a more secure future in networking! Thank you for joining us!
Discussion Questions:
1.What strategies can be implemented to address the issue of false advertisements in the OSPF protocol?
2.How could the BGP hijacking incident that made YouTube inaccessible have been prevented?
3.Why is there a lack of strong authentication mechanisms used in routers to prevent false advertisements?
4.How can blockchain technology be strategically implemented to address routing issues?
References:
• Wikipedia. Routing protocol. Available at: https://en.wikipedia.org/wiki/Routing_protocol
• CNET. How Pakistan knocked YouTube offline (and how to make sure it doesn’t happen again). Available at: https://www.cnet.com/culture/how-pakistan-knocked-youtube-offline-and-how-to-make-sure-it-never-happens-again/
• Cisco. IP Routing: OSPF Configuration Guide. Available at: https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/iproute_ospf/configuration/xe-16/iro-xe-16-book/iro-cfg.html
• Wikipedia. Dijkstra’s algorithm. Available at: https://en.wikipedia.org/wiki/Dijkstra%27s_algorithm#:~:text=Dijkstra%27s%20algorithm%20(%2F%CB%88da%C9%AA,and%20published%20three%20years%20later
• ACM Digital Library. Blockchain Router: A Cross-Chain Communication Protocol. Available at: https://dl.acm.org/doi/10.1145/3070617.3070634#:~:text=We%20introduces%20blockchain%20router%2C%20which,other%20same%20like%20Internet%20network

