
A recent article posted on September 19th claims to have seen evidence that German police and authorities successfully de-anonymized a Tor user which resulted in their arrest and conviction back in 2022. [3] Tor has and is still the main method for someone to anonymously access the internet and the dark web. Anonymity has made TOR the go-to browser and service for people who are persecuted or fear for their lives. However it has the same benefits and uses for cybercriminals, which is why police agencies are actively trying to break the service and learn users’ identities.
What is Tor?
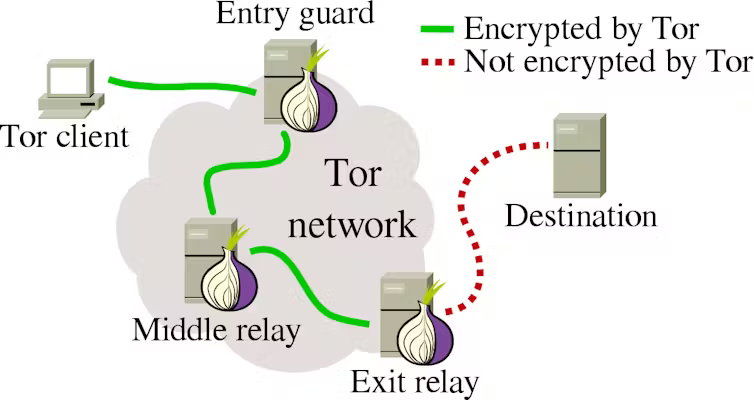
Tor is the leading way to anonymously access the internet and dark web. Initially, users connect to an entry or guard node, this is the only node or computer that knows the user’s IP address. From there the packets are randomly sent through the Tor network, which is a web of computer servers, encrypting the packets as it’s sent. After the packets are routed through a few nodes, the packets will reach an exit node which will then access the website the user is connecting to and communicate with it. The exit node will then send the response through the network back to the user. This way no one knows what a user is accessing, and the packets are not traceable. The only thing known is that the user has accessed the TOR network.
What Happened?
A recent article tells the story back in 2022, the German authorities de-anonymized a user named ‘Andres G’ who was running a website called ‘Boystown’ which hosted child pornography. [3] The report says that the German authorities were able to do this by first getting the cooperation of the carrier, Telefónica, which allowed the German authorities to get a list of people accessing Tor. From there the report says the Germans used a ‘Timing Analysis’ to identify the user.[3] While specific details about how the analysis worked was not released, it is speculated that the Germans have put rogue nodes on the Tor network and by using those to observe the size and timing of packets, and referencing when users are accessing the service, they were able to identify the user.
They caught a criminal so what?
Catching the criminal is admirable and ideal, however de-anonymizing Tor could have big consequences. This is because not only criminals use Tor but many users are also people who live in countries with authoritarian governments and to operate safely and stay alive in their country, they rely on Tor to keep their internet and communications activity anonymous. A spokesperson from a hacker group, called Chaos Computer Club (CCC), who has viewed the report and knows the method the German authorities used says that the method used by law enforcement can also be used by authoritarian regimes to de-anonymize Tor users and as such the Tor Project needs to make improvements to fix the issues. [2]
What’s Tor response?
The Tor Project responded with ‘there’s nothing to worry about and that user’s anonymity is safe’. [2] They say that ‘Andres G’ was de-anonymized from a guard discovery attack vulnerability in a messaging service called Ricochet. [2] Tor explains that the criminal, ‘Andres G’, was using an old insecure version of Ricochet and that this vulnerability has already been patched in the newer version called Ricochet-Refresh. Tor does admit that they have not seen the report or the evidence that suggests the Tor network is vulnerable so they cannot fully comment on it. The Tor Project says, “the information it has been presented with suggests that users can continue to confidently rely on the anonymity network to protect their identity.”[2] Lastly, the Tor project team message is “Don’t panic”.[3]
Conclusion
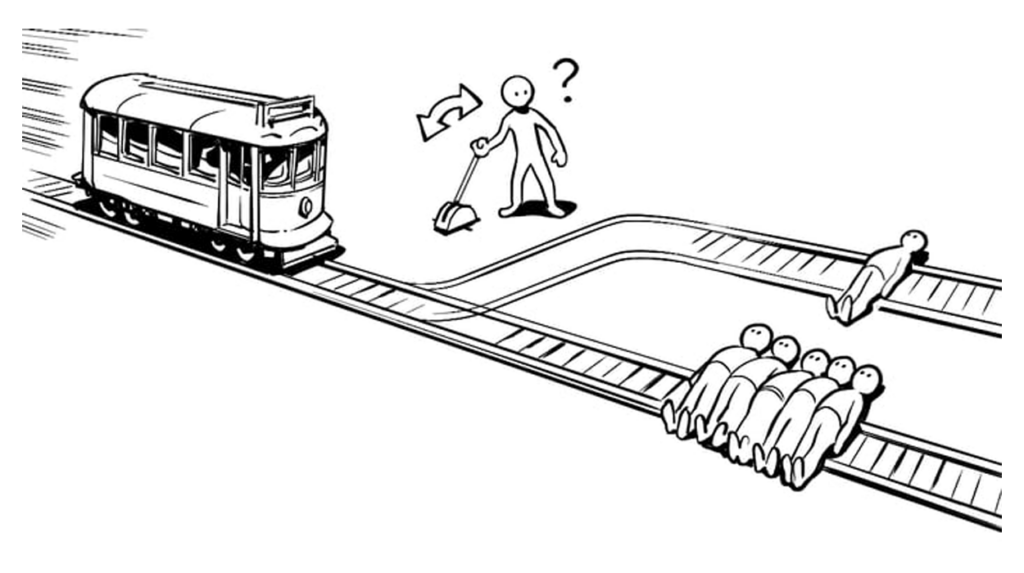
While it is positive that the German police and other police forces are actively catching cyber criminals, I’m hesitant to agree that removing anonymity from networks like TOR is the best solution as it can lead to the endangerment of people in authoritarian countries. This very much an ethical debate of how much privacy people should have, and it reminds me of the Trolley problem. Is catching criminals worth endangering innocent people in another part of the world? Do the potential victims saved from stopping the criminals equal the risk to users who need the anonymity to be safe? I value both sides of the debate which makes me feel that there isn’t a simple yes or no answer.
References
[2] https://www.securityweek.com/tor-responds-to-reports-of-german-police-deanonymizing-users
[3] https://www.theregister.com/2024/09/19/tor_police_germany
[4] https://cybernews.com/privacy/tor-exit-node-operator-raided-germany

Interesting blog, Hayden. Debates about the dark web will undoubtedly go on, due to its complexity, while some will argue that it offers safe grounds for activists to express themselves without fears of being hunted down but the scale of dangers it poses to cybersecurity is endless. This also raises a question about a long-term solution to curb the dark web’s excesses and hold these cyber criminals and bad actors accountable. The dark web needs to be constantly regulated, supervised and monitored through a multi-national collaborated approach. Another solution might be for us as cybersecurity students go into research projects to develop tools and solutions to remedy these issues around the dark web.
I agree with you Mohammed, though I feel that the nature of how privacy and anonymity works doesn’t allow for some people to be anonymous and some people not to be. I simply don’t see how there could be a solution that allows us to regulate or track cybercriminals but keep activists safe and anonymous. This goes back to the double edge sword of privacy and of by giving everyone the privacy they have a right to you also must give criminals that privacy. My only thought on how you could track the criminals and not the activists are to have a trusted organization that knows everyone’s identity but keeps activist anonymous. That though raises more concerns and questions like how do we trust this organization? How do we ensure they don’t have leaks? Who counts as an activist and who counts as a criminal? I feel theses aren’t easy questions to answer. Though like you said maybe as students we can research and find a way to track the criminals and keep the activists safe finding a better solution, maybe a more complex system will be the solution.
Thank you Hayden for this new insight! First time reading about Tor and I must say, its an interesting one.
Tor provides an amazing service, at least it helps its users facing authoritarian government still have access to the internet and carry out their legitimate business anonymously but with everything in the world now, adversaries would always find their way into everything good! I believe the government should find better ways to catch criminals and still let the people who need this service have the ability to use it freely and anonymously. I hope we can have both.
Very interesting post! Anonymous access or hiding identity always carries doubt and unclarity about the user. We all know that the dark web is actually a dark place where maximum content is harmful. For that reason, sites like “Tor” help people enter the dark web. From my opinion, the government should strictly handle this kind of site and the people who operate it. Additionally, some government activities also engaged in anonymous activity, which should not be happening. This anonymous activity always leaves a place for hiding something, and that is why this kind of anonymous activity should be stopped for all.
Hayden, your post was quite interesting. I completely agree with the conclusion of your piece. Most people require the highest level of protection and privacy to prevent critical information from being stolen and sold on the dark web. The dark web is a secret and dangerous sector of the internet that poses a huge threat to both individuals and businesses, and its anonymous and uncontrolled nature makes it a safe home for cybercriminals.
Great post!
Well, according to me, this incident raises a crucial question regarding the balance between public safety and personal privacy. It is very important to catch the criminals, but there is genuine concern for the legit users. Many people rely on Tor for safe and unrestricted access of information, especially in nations with oppressive governments. If law enforcement can bypass Tor’s protections, then authoritarian governments could do it too, putting at risk the people who rely on being anonymous to stay safe. We need transparency and regular security audits for ensuring that fighting against cybercrime or cybercriminals does not put the safety of the legit users at risk.
Very well informative post and a really good reasonable question, Hayden.
This is another war type between government authorities and privacy advocators. I am strongly in favor of having Tor and similar platforms as these are the only gates for freedom of speech and communicating publicly with a considerable free ideology. I also, agree with Mohammed’s comment earlier that regulation is needed, in the sense of disclosing identity, but in preventing crimes such as child pornography, and illegal activities. I would hope Tor and similar platforms stand up against these criminal activities with self-initiative regulation, rather than waiting for governments to impose their own agenda. Dalins, J. et al. introduced Motivation Model (TMM) enabling Tor better taxonomy and enhanced content labeling. Dalins and similar research can benefit the darknet by restricting illegal content and starting self-cleanup classification while at the same time maintaining the hidden identities of the publishers (Dalins, J. et al., 2018) [1]. This can be very helpful to eliminate malicious and illegal activities on the darknet.
[1] Dalins, J. et al. (2018). Criminal motivation on the dark web: A categorisation model for law enforcement. Digital investigation. [Online] 2462–71.
Interesting post Hayden! You make a very good point about the danger of de-anonymizing Tor for those of us in heavily censored countries. I’m uneasy thinking of how algorithms such as timing analysis could be used to expose users. Tor’s answer is comforting, but I wonder if it’s enough when cyber forensics and tracking are developing so fast. Thanks for the way you framed the two sides of the story. Tor’s usefulness for providing anonymity to the most vulnerable among us is precious, but it can also be a proxy for spies. It’s great that Tor has fixed some of these holes, but, as you said, you can never be sure it is 100% safe.
This is a really insightful post about the challenges surrounding Tor and its dual role in providing both anonymity for vulnerable users and criminal activities. The ethical dilemma you highlighted is crucial; while it is important to catch criminals like ‘Andres G’, we also have to think about the consequences for those who rely on Tor to stay safe in oppressive regimes.
The ethical dilemma you mention is significant—how do we balance the need for privacy with the goal of enhancing security? Striking a balance between privacy and security is challenging, and as technology evolves, we need to rethink our strategies for tackling these issues. It is crucial for the Tor Project to keep improving its safeguards while addressing the valid concerns of law enforcement. Your reference to the Trolley problem captures this moral complexity perfectly!
Great job, Hayden! “De-anonymize” draws attention to the fact that, no matter if the best tools are used, full anonymity is never guaranteed nor foolproof. Each tool has its vulnerabilities, technical issues, user behavior, and legal policies and pressures. With that in mind, for example, although VPNs and Tor are distinct protection mechanisms, they can still be tracked with methods such as traffic analysis. The better privacy is, the better the combination of these anonymity tools works for you. But we have to think about the ethical implications of using these technologies for law enforcement and governments and the balance between having to be safe and having privacy.
Really interesting post Hayden! Tor is such a great tool to protect our privacy over the internet. There are not many options out there so we should be aware if there is a vulnerability in these features.
Analyzing the answer from the Tor Project team, I agree that for the time being there is no need to panic. The amount of effort from the German government to locate a single user precisely was incredible, it had to coordinate the traffic analysis and reach ISPs to cooperate with the analysis process.
We have to consider that this service is not perfect and it needs to be constantly upgraded to avoid other problems. Thanks for the information! It was really useful.
Hi Hayden,
Thank you so much for the post! This is a very interesting post to read, and I truly enjoyed it. I liked that you also have a paragraph to describe about what is Tor.
This is a very important information lead to the rest of the story. I got to say after reading this most, I have mixed feeling about the de-anonymizing Tor. This is something more of a ethical discussion. It is a really impressive and great work of the German authorities could able to do this to catch a criminal. But at the same time, how to keep people’s privacy not being violated. Furthermore, this is a two way street as well, when authorities could de-anonymized, the criminals could also use the same way to get conidial documents form the authorities as well. That being said, I really like the last picture you added to the post, it vividly expresses the hard decision about the situation. Great post! After reading the post, I cannot stop thinking about this as I guess there is no perfect answer to this question, we could just go as we see where we can catch more criminals and protect people’s privacy at the same time.
Hi Hayden, great post! I really enjoyed the practical and ethical concerns that were brought up due to Tor being De-anonymized, especially those regarding users in authoritarian countries who depend on anonymity for safety. Additionally, the perspective brought forth by The Chaos Computer Club shows us the impact de-anonymization could have if users are revealed within an authoritarian regime. Their safety is compromised very severely in the case this occurs. Although preventing cybercriminals is a very promising outcome, anonymity is essential for the success of this network, which is why it is very interesting to see the balance between crime prevention and the safety of innocent users relying on anonymity.