A total $31.5 million penalty has been issued against a famous telecom brand, “T-Mobile” to settle an investigation by the Federal Communications Commission (FCC) for a past series of data breaches that leaked millions of personal data. This company has reached an agreement with the US Federal Communications Commission (FCC) to give $15.75 million as a penalty against a sequence of cyber security breaches from previous years, and the rest will function as collateral for their data security development. The FCC inspection finds a serious gap in the company’s cyber threat protection, which led to a series of cyberattacks taken place in 2020,2021 and 2023 respectively.
What is T-Mobile and how it operates?

T-Mobile US Inc. or “T-Mobile”, is a US based wireless network operator that mainly provides services like voice, text, video calling, and data communications to postpaid, prepaid, and wholesale customers under T-Mobile brands. This company also engaged in the distribution of smartphones, routers, and other mobile communication devices. T-Mobile also operates in Canada with unlimited talk, text, and setup or roaming charges exempt.
Analysis of Each Cyber Attacks
T-Mobile’s Data Breach’ 2020
T-Mobile faced a cyberattack in 2020 where lots of personal data got stolen. Though the company denied that no customer data was leaked during the cyberattack, nevertheless, hackers from the dark web forum affirmed that, they accessed a total of 100 million customers personal information like names, phone numbers, home addresses and IMEI numbers. Additionally, they disclosed that they have reached the server through hosting phishing attacks over mail-SMS text messages, and scam calls to the end user. Hackers also used the SIM card swapping technique where bad actors can take control of the end user’s phone number, which led them to effectively access their account and prevent the end user from entering the account.
Furthermore, cyber attackers exploited this process by interrupting text messages intended for authorization, which also allowed them to obtain access to other accounts linked to the individual end user’s phone number.
T-Mobile’s Data Breach’ 2021
In 2021, personal information of over 50 million customers of T-mobile, including SSN (Social Security Number) got leaked. During the data breach, previous, present, future potential customer and postpaid customers got affected. However, one good thing about this event is that bank details of each customer were safe during the hacking. The American hacker, John Brinns, who took the responsibility of this hacking, mentioned that the routers and IP addresses of T-Mobile company were very weak, which allowed him to grab data from more than 100 servers. In this type of attack, hackers observe the system’s public isolated network components and try to find a weak window in the network architecture that acts as digital home addresses for other devices connected to the network. Binns didn’t mention about any settlement with T-Mobile; nonetheless, he does mention trading the data into dark web that will be used for identity theft or future possible cyber-attacks.
T-Mobile’s Data Breach’ 2023
After facing several data breaches, yet flaws remain in T-Mobile’s servers, and they faced another huge cyberattack in 2023. In this recent attack, over 37 million customer’s data, like birthday and contact information got leaked. The company ensured that, no sensitive information like bank details or Social Security Number was stolen during the cyberattacks. The data breach actually happened on November 25th, 2022, and the company declared the news after 8 weeks, on January 19th, 2023. In this cyberattack, hackers used APIs to enter the system.
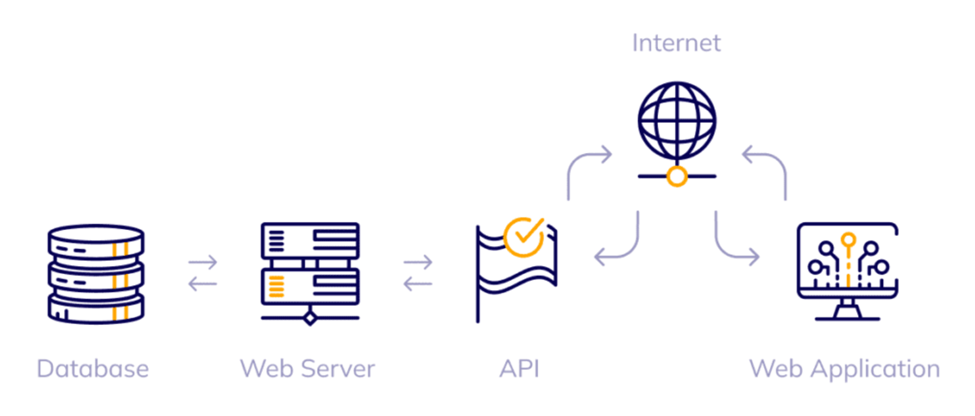
API, or Application Programming Interface is a type of software interface that works as a connection channel between computers or their programs. In this type of attack, hackers attempt to manipulate APIs by locating the system, security details like how the API is constructed and applied. After that, hackers try to find the weaknesses of the system like insufficient encryption and poor authentication which led them into cyber-attacks like DDOS (Distributed Denial of Service), MITM (Man-In-The-middle), API injection attack.
After facing many frequent cyberattacks, it is obvious that there was insufficiency in the company’s data security protection. Telecom companies should take proper security measurements against cyber attacks as they engage with consumers sensitive data. Hackers are more advanced these days, and they look for every tiny loophole in the system. As a consequence, every company that is occupied with people’s sensitive data should increase their data privacy threshold up to the mark. At the end, penalty cannot retrieve the stolen data.
Reference:
- Coker, J. (2024, October 1). T-Mobile to pay $15.75m penalty for multiple data breaches. Infosecurity Magazine. https://www.infosecurity-magazine.com/news/t-mobile-penalty-data-breaches/
- Plc, G. (n.d.). Tmobileus Inc company Profile – Tmobileus Inc Overview. https://www.globaldata.com/company-profile/tmobileus-inc/#:~:text=T%2DMobile%20US%20Inc%20(T,%2C%20prepaid%2C%20and%20wholesale%20customers.
- Lukic David Lukić is an information privacy, D. (2020, August 17). T-Mobile Data Breach: The infamous cyber attack. IDStrong. https://www.idstrong.com/sentinel/the-saga-of-t-mobile-data-breach/
- IP address hacking: Risks and tips for Secure Networks. Trend Micro Help Center. (2024, October 31). https://helpcenter.trendmicro.com/en-us/article/tmka-12368#iphack
- Routing attack meaning. Ledger. (2024, March 13). https://www.ledger.com/academy/glossary/routing-attack#:~:text=A%20routing%20attack%20is%20a,it%20into%20multiple%20isolated%20components.

Great post shuvo!!! this is a reminder that hackers do research whenever they want to exploit any system, and it is also a wake-up call to organizations to hire credible security professionals to help mitigate the harmful attack from hackers. in the post, T-Mobile tried to do damage control, which worked because the better control over the information from their system, and T-Mobile have to pay the price of not having good security professionals.
Good job, Saidul! As an end-user on a telco network, you can do little to protect yourself from the endpoint. 70-80% of the weight of security rests on the shoulders of your service provider. Same T-Mobile suffered a breach in 2015 that leaked 15 million information on customers applying for credit(https://www.t-mobile.com/news/blog/experian-data-breach).
For this reason, I will say T-Mobile has failed the general public in this regard. They can do better. Thinking as a user, I will switch to another service provider, having a reliable provider is super important. T-Mobile should invest more in training their employees and rolling out standard industry practices for cybersecurity.
Wow! Getting breached 3 times in the space of 5 years is a big NO!
T-Mobile can do better and should do better in prioritizing the security of its assets which customer data is top on the list. Implementing in depth security measures would help bring down breaches and better safeguard their networks and systems.
Great analysis, Saidul! The recurring data breaches at T-Mobile highlight significant gaps in their cybersecurity framework. It’s particularly concerning that despite previous incidents, the company continues to face major breaches, including the exploitation of APIs in 2023. This indicates poor ‘housekeeping’ practices and strategies coupled with low strategy infrastructure funding.
The staggering fines as shocking as they are serve more as a pointer to what neglecting cybersecurity can cost a firm in reputation and money. Sadly, these penalties won’t recover lost data or mitigate the long-term effects of identity theft. Organizations ought to take the initiative to adopt measures such as API protection, conduct frequent checks, and install sophisticated detection systems for their in-house data and their customers’ data.
Great work Shuvo, the fact that T-MOBILE allows their customers to go through all of the pains of loosing their information to hackers in a more frequent times is really a bad thing of them to have done because customers are only end users and can only do little to protect them selves. The constant data breaches highlight significant weak protection in their cybersecurity framework. Organizations should start taking the initiative to provide a more proactive measures such as API protection.
Great post, Shuvo! T-Mobile breaches show how badly the absence of reliable security teams, robust systems, and controls can cause a significant loss to businesses. Also, highlighted how unsecured APIs can be big vulnerabilities. APIs are great for system interoperability, but if provided to the public, these become an entry point for attackers to exploit weak authentication, no encryption, or insufficient access controls. Securing APIs requires strict authentication protocols, data encryptions, repeated security testing, and strict monitoring, which will help companies to protect sensitive data, and minimize the risk of cyber threats.
Great post Shuvo! T-Mobile gets several breaches within the span of a few years are terrifying. Each attack has seemed to have revealed some weakness, be it Phishing, unsound network architecture, or API bug. Perhaps this FCC fine and improvement agenda will push T-Mobile to build better defenses. The telecom companies must safeguard their customers’ data as it’s the sensitive data they deal with. Such patch after patch must be the most unsettling for T-Mobile’s customers. That you’ve seen a person’s personal information, such as their contact number or Social Security number, be viewed multiple times destroys confidence. I would like to think if we had better regulatory regulation or more industry standards to get telecom companies to be even more concerned with security.
Great post Shuvo! T-Mobile gets several breaches within the span of a few years are terrifying. Each attack has seemed to have revealed some weakness, be it Phishing, unsound network architecture, or API bug. Perhaps this FCC fine and improvement agenda will push T-Mobile to build better defenses. The telecom companies must safeguard their customers’ data as it’s the sensitive data they deal with. Such patch after patch must be the most unsettling for T-Mobile’s customers. That you’ve seen a person’s personal information, such as their contact number or Social Security number, be viewed multiple times destroys confidence. I would like to think if we had better regulatory regulation or more industry standards to get telecom companies to be even more concerned with security.