Introduction
In January 2024, Spoutible, a social media platform launched as a direct rival to X (previously Twitter), suffered a major data breach that exposed the sensitive personal information of 207,000 users. The incident, discovered security researcher, was attributed to a flaw in the API configuration of Spoutible’s platform raising serious questions about the safety of users’ sensitive information on social media, especially for social media sites that deal with huge traffic of users’ sensitive information. [1]
This article provides a detailed analysis of the Spoutible incident, outlines the primary API weaknesses utilized by the attackers, and discusses best practices to improve API security in the context of the modern social media environment.

What Are APIs and Why Are They Important in Social Media?
Application Programming Interfaces (API) are used for applications to establish communication, interact, and share data with other applications. In social media, APIs help platforms communicate and exchange data between the internal space of platforms and external applications that increase functionality and user experience for social media platforms. For instance, social media APIs let you post content, view member data, and integrate third-party apps that streamline usage across multiple social media platforms. [2]
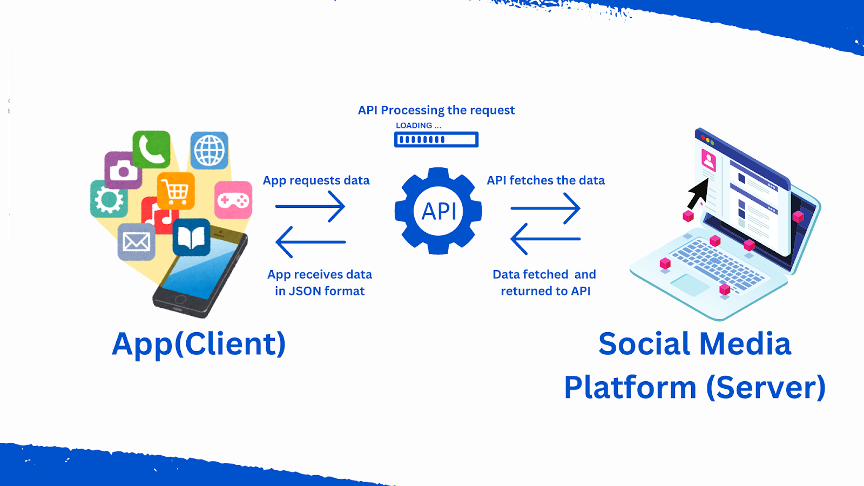
For Spoutible, the sensitive user data was exposed via the poorly configured API to anyone capable of making API calls with the username. This breach highlights two vulnerabilities in API, Broken Object-Level Authorization (BOLA) vulnerability [3] and excessive data exposure in APIs.
Technical Details of the Spoutible API Breach
Spoutible’s vulnerability came from three primary issues:
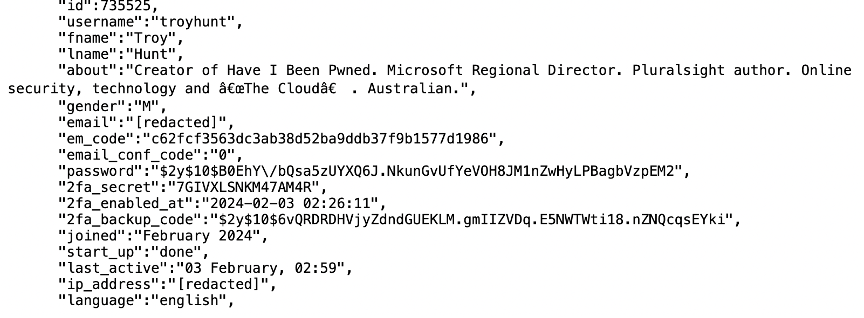
- Broken Object-Level Authorization (BOLA): An API flaw that allows attackers to access data without the appropriate authorization checks. Comparing the current state of Spoutible to its prior state, due to a lack of object-level authorization, user-specific data (email, bcrypt hashed passwords, two-factor authentication (2FA) codes) were able to be accessed by simply querying Spoutible’s API via a username [3][4]
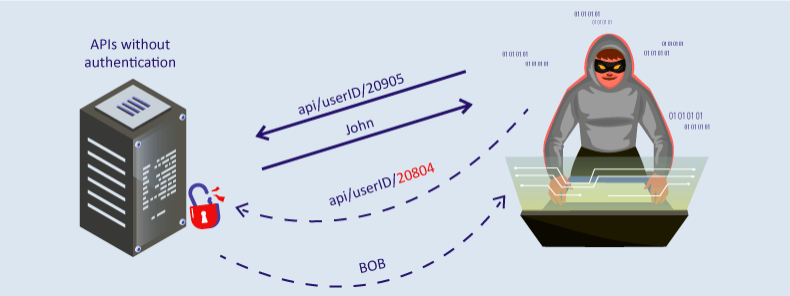
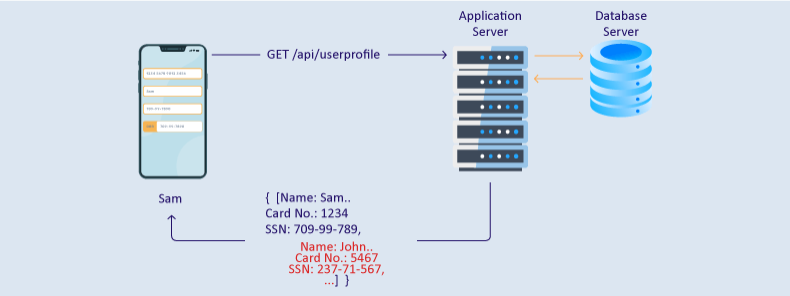
- Excessive Data Exposure: An API should only return data it needs to satisfy a request. While Spoutible’s API did expose sensitive fields such as hashed passwords and 2fa codes it did so in the responses, which significantly escalated the potential for a data breach if the API could be queried by an unauthorized party. These fields, particularly 2FA codes were the easiest for attackers to skirt past account security layers [4] [5]
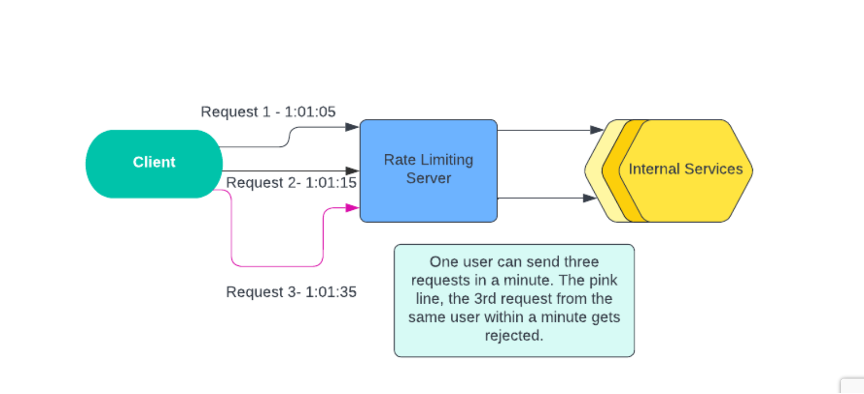
- Absence of Rate Limiting: Absence of Rate Limiting: It helps in rate limiting requests, so a user is not able to hit the API so much in a short amount of time and prevent scraping and brute force attacks from happening automatically. [7]
The Data Exposed in the Breach
The data compromised in this incident included
- Username, Email Addresses, and Phone Numbers: Useful for phishing and social engineering attacks.
- Gender
- IP Addresses: Reveal the location of the user to attackers.
- Password Hashes and 2FA Codes: While Spoutible used bcrypt hashing, these tokens could still be exploited if decrypted or brute-force. [4]
- Password Reset Tokens: Anyone can take over the account
In addition to all the above, the user did not receive any notification of the password change, and there is no option to invalidate active sessions on other devices if the password was changed.
[1] [4]
Spoutible’s Response to the Breach
- Users were notified to reset their Spoutible passwords based on strict password policies.
- Users were instructed to reset 2FA to generate a new secret if it was enabled on Spoutible.
- Users were advised to reset their password across other accounts if they used the same password.
- Users to stay vigilant for any suspicious activity on their accounts.
- A team of security experts was appointed to review Spoutible’s security architecture as well as identify the vulnerabilities and implement the best practices within the industry.
- Spoutible revised its API by removing sensitive data fields included in responses and integrating strict authentication procedures around its API endpoints.
[4]
Lessons from the Spoutible Breach: API Security Best Practices
- Deploy Authentication and Authorization: Before allowing access to sensitive information, a system should be able to verify the user’s identity.
- Use SSL/TLS Encryption: To ensure the security of all communications between clients and APIs we can use encryption protocols like TLS, to ensure the protection of data during transmission.
- Implement Rate Limiting: Rate limiting prevents malicious automated attacks by limiting the number of requests our APIs will handle per certain period.
- Use Auditing and Logging: Companies can monitor and validate API requests to ensure that data will always be secure, and no one can misuse it.
- Anomalous Activity Monitor and Alert: Prompt detection of unusual activity allows the cybersecurity teams to detect and resolve issues before they rise to become serious threats.
- API Penetration Testing: Regular penetration testing helps discover and fix API vulnerabilities before attackers can exploit them.
[9]
Conclusion
Modern social media platforms must learn from the Spoutible breach and prioritize API security. By implementing key security best practices such as strong authentication, SSL/TLS encryption, rate limiting, auditing and logging, real-time monitoring, and regular penetration testing, platforms can significantly reduce the risk of security breaches. This serves as a critical reminder for all platforms handling personal data, especially through APIs, to make API security their top priority to protect user privacy and maintain trust.
References
[1] Twingate Team. (2024, April 17). What happened in the Spoutible data breach? Twingate. Retrieved November 5, 2024, from https://www.twingate.com/blog/tips/spoutible-data-breach
[2] Here’s the APA citation for the Sprout Social article by Jacqueline Zote:Zote, J. (2022, November 15). What is an API? Sprout Social. Retrieved November 5, 2024, from https://sproutsocial.com/insights/what-is-an-api/
[3] Imperva. (n.d.). Broken object level authorization (BOLA). Imperva. Retrieved November 5, 2024, from https://www.imperva.com/learn/application-security/broken-object-level-authorization-bola/
[4] Hunt, T. (2024, February 17). How Spoutible’s leaky API spurted out a deluge of personal data. Troy Hunt. Retrieved November 6, 2024, from https://www.troyhunt.com/how-spoutibles-leaky-api-spurted-out-a-deluge-of-personal-data/
[5] FireTail. (2024, February 8). Leaky Spoutible API exposes user data: What went wrong? FireTail Blog. Retrieved November 6, 2024, from https://www.firetail.io/blog/leaky-spoutible-api-exposes-user-data-what-went-wrong
[6] Zahra, A. (2024, August 17). Social media integration: Enhancing apps with social media APIs. APILayer Blog. Retrieved November 6, 2024, from https://blog.apilayer.com/social-media-integration-enhancing-apps-with-social-media-apis/
[7] Chinnasamy, V. (2022, January 20). Critical OWASP top 10 API security threats. Indusface Blog. Retrieved November 6, 2024, from https://www.indusface.com/blog/critical-owasp-top-10-api-security-threats/
[8] Forshaw, A. (2022, July 29). Right ways of API rate limiting. The Auth API. Retrieved November 6, 2024, from https://theauthapi.com/articles/api-rate-limiting/
[9] Qualysec. (n.d.). API security testing: Significance and guidelines. Qualysec. Retrieved November 6, 2024, from https://qualysec.com/api-security-testing-significance-and-guidelines/


Very insightful blog Firas! This is about the 4th time I’ve read a blog a breaches due to the API misconfiguration or weakly secured APIs. We can all agree that APIs deserve more attention than they’re getting, predominantly, we have our focus on database and network security leaving out API security. Thank you for those useful security tips, just to add a few more, I have attached a link to a blog below for some best practices on securing an API. https://curity.io/resources/learn/api-security-best-practices/
Well written blog ! 2024 has seen an alarming number of data breaches due to insecure APIs, and this blog does a great job highlighting the critical importance of API security in protecting user data. Given how much sensitive information social media platforms handle, it’s clear that regular penetration testing and anomaly detection are essential to catch vulnerabilities early, before they result in major breaches. Hopefully, more platforms start to prioritize these practices to keep user data safe!
To find a brief about the breaches because of poor API Security in first half of 2024 here is a reference :
https://approov.io/blog/how-poor-api-security-led-to-major-breaches-in-2024
Great Post!
The Spoutible data leak highlights how important it is to be careful with social media APIs. These APIs are necessary to connect to user data, but they can also be easy targets for security issues. Spoutible’s failure to enforce proper authorization, restrict data exposure and apply rate limiting allowed attackers to take advantage of these vulnerabilities. This shows that even simple security errors can result in a lot of private information being exposed. To stay safe from threats, social media companies need to use good security practices for their APIs. Organizations must includes strong authentication, authorization and monitoring to tackle such threats.
Great post, Firas. No doubt using the best practices are crucial to ensure no vulnerability is missed. Frameworks such as the Open Source Foundation for Application Security (OWASP) should be a good starting check list that application providers to use. According to OWASP (Katie Paxton-Fear. 2019) [1], API injection is a potential threat where attacker can exfiltrate confidential data from the API calls. This method is well know on web application such as SQL injection where it can be executed via web calls similar to the API. In addition to the points highlighted in the lessons learned, it is important to shed light on using modern authentication that leverage API. Using Secret Keys have become very essential to authenticate the API caller before executing the the API functions to confirm the identity of the API caller (Called could be an approved system or website URI). In addition to using secret keys, API can use modern authentication methods such as Java Web Token (JWT) where the scope of the API can be specified. For instance, the same API website can be limited to specific functions (scope) based on the called ID. This ensures that not all API functions are exposed to all users and provides compliance to the least privilege access principle when design API web services [2].
[1] Katie Paxton-Fear. (2019). API Injection. Retrieved from: https://www.traceable.ai/owasp-api/injection
[2] IBM OS Connect (OpenAPI 2).(16 January 2014). Retrieved from https://www.ibm.com/docs/en/zos-connect/zosconnect/3.0?topic=SS4SVW_3.0.0/securing/requester_jwt.htm
Great post, honestly very baffling that sensitive data is just included in the API response. Whoever made that decision should really do some security training. I’m really surprised that they had no authorization on their API calls and that sensitive data was in part of the response. API are also hard to manage but it seems Spoutible was barely trying. Another big issue with API’s is people accidently adding the API keys or access tokens to public GitHub repositories, as once it’s published to the repo you can delete it as the API key will show in the change history.
Nice post firas, It is critical need for social media platforms to adopt robust
API security measures to prevent incidents like the Spoutible breach. Key practices such as strong authentication, encryption, rate limiting, and monitoring are essential for protecting user privacy and maintaining trust. By prioritizing these security protocols, platforms can effectively prevent sensitive personal data and enhance the overall security and integrity of their services.