Cybercriminals, including those of Portuguese origin operating out of Brazil, Asia-based threat actors using advertiser accounts from Hong Kong, and a threat actor group of Eastern Europeans, are using Google search advertisements to promote phishing sites that steal advertisers’ credentials for the Google Ads platform and utilize it to push out malvertising campaigns. 1
How are they using Google ads to steal accounts?
Attackers continuously run ads on Google Search impersonating Google Ads and put up sponsored results that redirect potential victims to fake login pages hosted on Google Sites that look identical to the official Google Ads homepage through which they are asked to log into their accounts.1 The scheme consists of attackers stealing as many advertisers’ accounts via impersonating Google Ads and redirecting victims to fake login pages.1,2
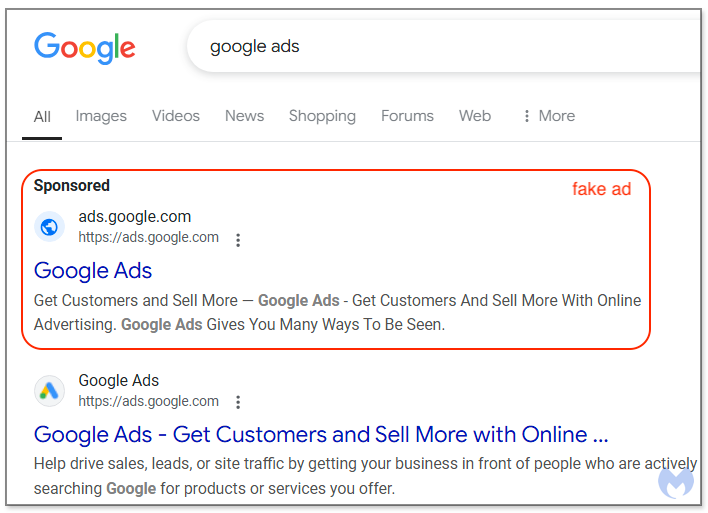
Image 1 – A malicious ad masquerading as Google Ads itself [4]
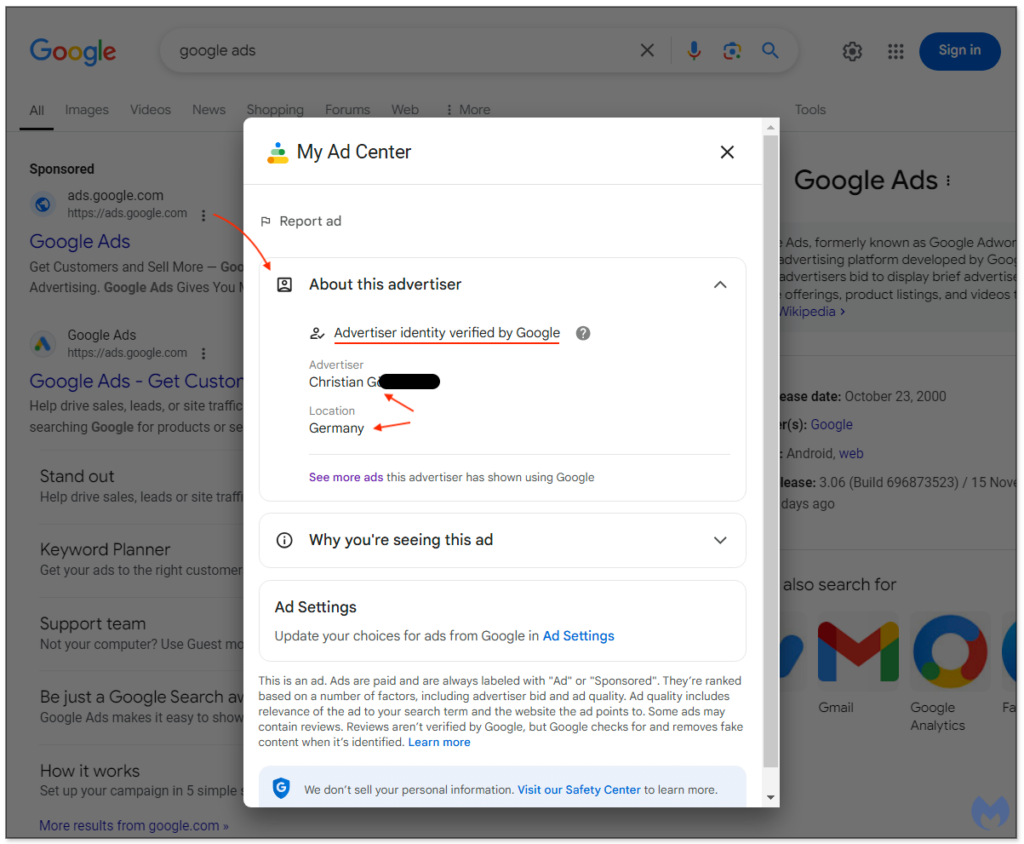
Image 2 – Fake advertiser not affiliated with Google [4]
Based on reports, these stolen credentials will be reused to perpetuate the campaigns further, while simultaneously selling this information to other criminal actors on underground forums.1 By leveraging stealer malware to steal data, similar to Facebook advertising and business accounts, attackers can hijack them and use these same accounts for push-out malvertising campaigns that further propagate the malware by redirecting users to fraudulent sites hosted on Google Sites that already have hundreds of legitimate ads running.1,2 Using strategic social engineering techniques, these sites then serve as a landing page to lead the visitors to external phishing sites designed to capture their credentials and two-factor authentication codes via a WebSocket. This information is then exfiltrated to a remote server under the attacker’s control. This threat has been active since mid-November of 2024. 1,2
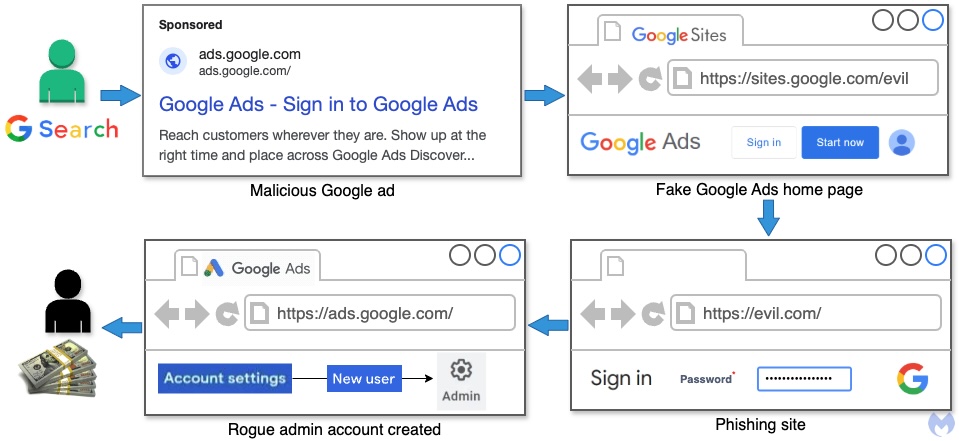
Image 3 – Attack flow illustrating the high-level mechanism by which advertisers get attacked (Malwarebytes Labs) [1]
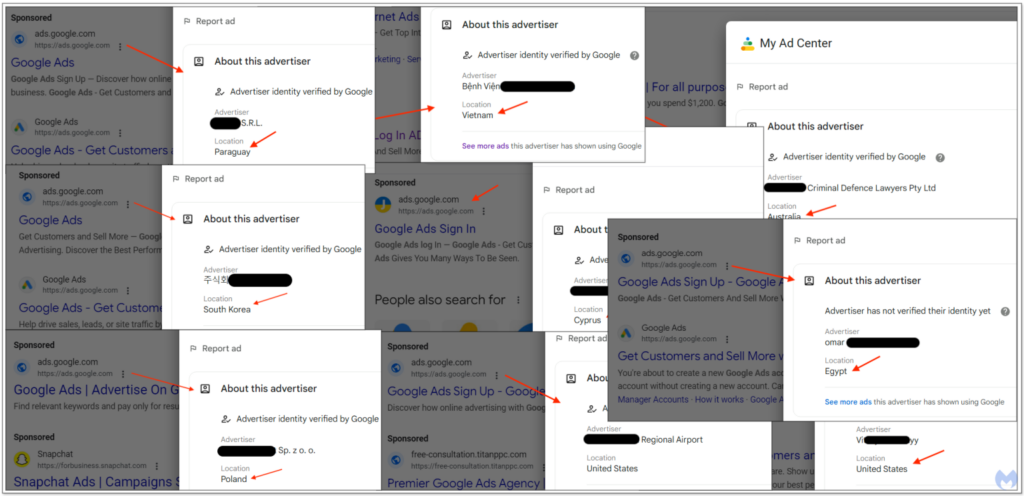
Image 4 – Accounts on Fake Google Ads [1]
Attackers further took advantage of the fact that Google Ads does not require the final URL to be identical to the display URL as long as the domains are matched.1,4 This allowed the threat actors to host their intermediate landing pages on sites.google[.]com while keeping the display URLs as ads.google[.]com. 4
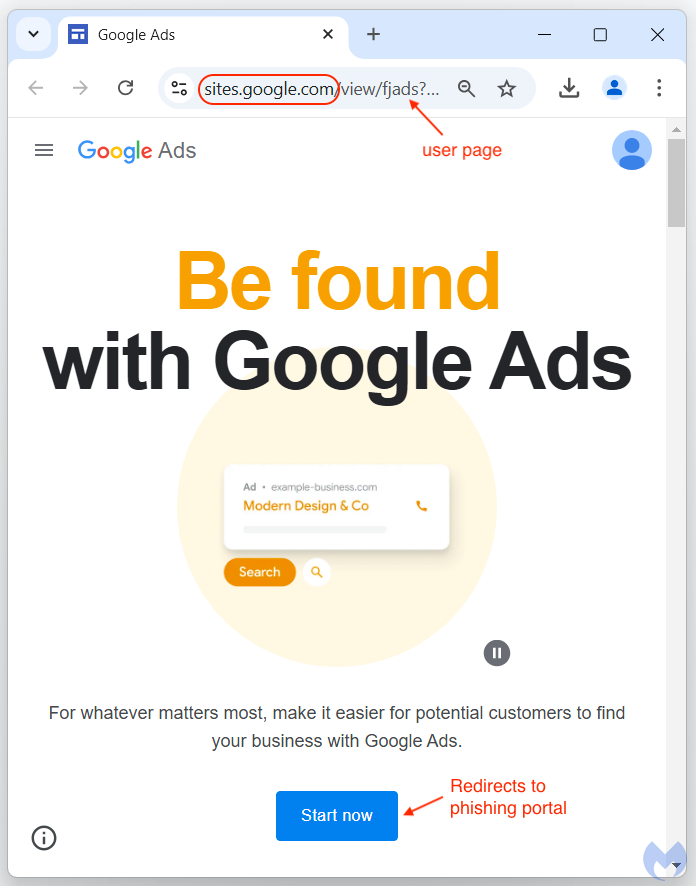
Image 5 – Gateway pages hosted by Google Sites via complete impersonation [4]
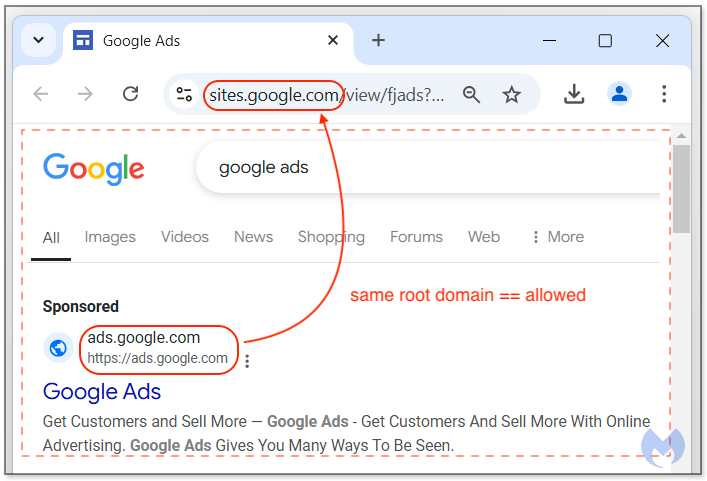
Image 6 – The same root domain used to mask malicious websites [4]
Once the victims click the ‘Start now’, users are directed to a different site containing the phishing kit. Through this process, JavaScript code fingerprints users to ensure all important information is collected. 4
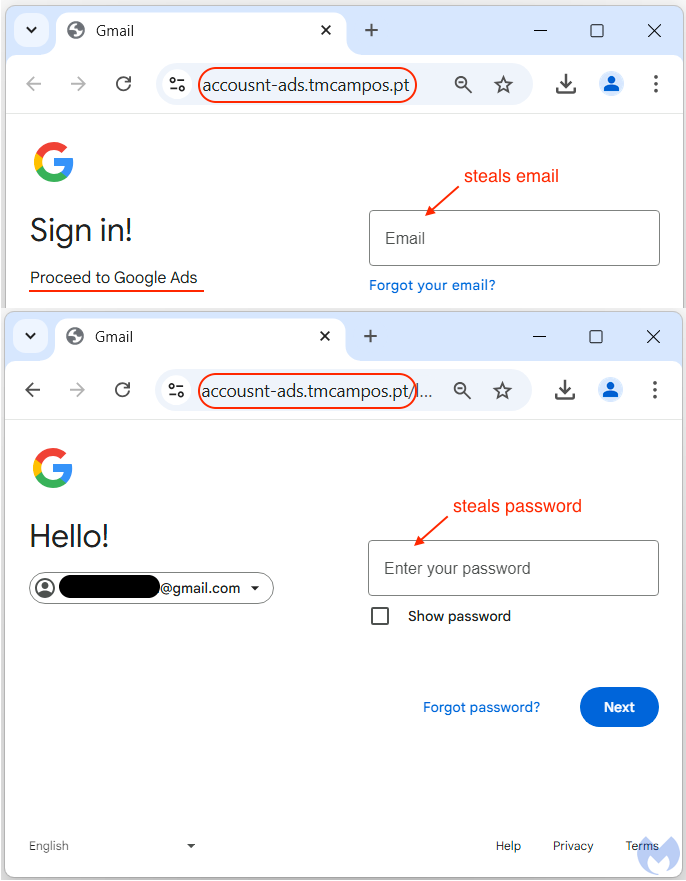
Image 7 – Phishing procedures [4]
All the information gathered is then sent to the remote server via a POST request where the attackers receive all information including the victim’s geolocation, city, and internet service provider. 4
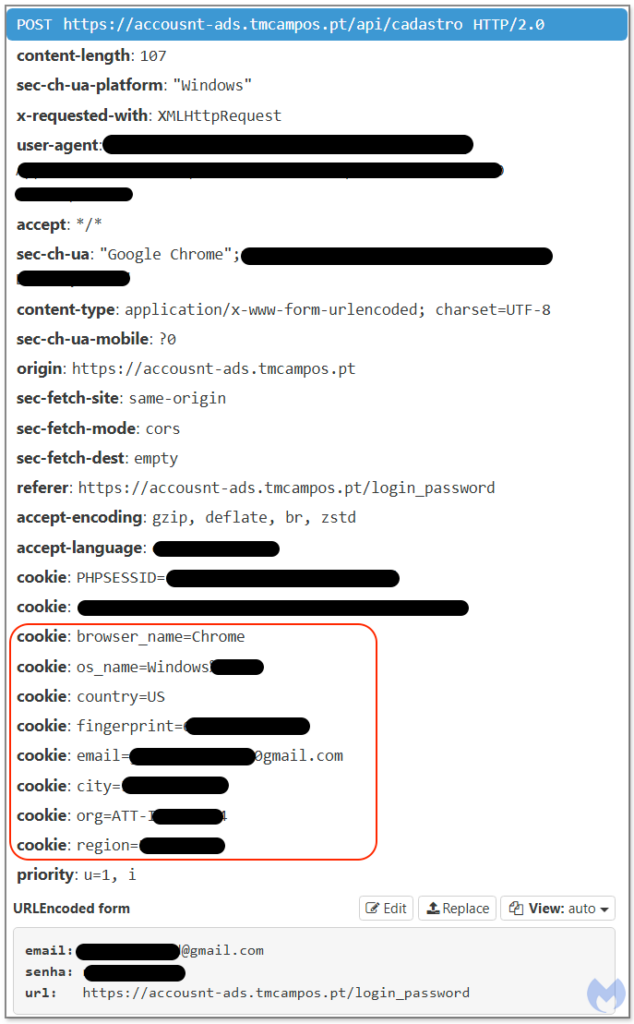
Image 8 – POST Web request with all gathered details of the victim [4]
In addition to this, techniques including fingerprinting, anti-bot traffic detection, and even a CAPTCHA-inspired lure were integrated to conceal the phishing infrastructures embedded within. 1,2
in 2023, Google blocked or removed 206.5 million advertisements for violating its Misrepresentation Policy along with over 3.4 billion ads, restricted over 5.7 billion, and suspended over 5.6 million advertiser accounts.1 In an interview conducted, a Google spokesperson says “We expressly prohibit ads that aim to deceive people to steal their information or scam their team. Our teams are actively investigating this issue and working quickly to address it.” 1,2
This marks a new extreme where such tactics lead to coned pages designed to steal login credentials and bypass 2FA codes in the process. 1,2 Various online reports of people who identified these fake ads shared their experiences: 4
- Help with removing a dangerous scam in Google Ads (Google Ads Help forum)
- Google Ads Phishing Scam (Reddit)
- It’s just me or Google just sponsored a link to a phising site for Google ads? (Reddit)
- Be aware of fake google page, clicked by accident (Reddit)
- Warning! First sponsorized google answer for “Google ads” is a phishing attempt ! (BlueSky)
Whether the money is spent towards legitimate ads or malicious ones, Google still earns the revenue leaving the victims at a loss of both money and personal information. 4 Despite Google’s policies stating “If we find violations of this policy, we will suspend your Google Ads accounts upon detection and without prior warning, and you will not be allowed to advertise with us again”, Google has yet to demonstrate taking corrective actions to freeze accounts until their security is restored. 4,6 Recently, an advertiser who had been reported over 30 times remains to be active. See this article for more information on this case – https://www.malwarebytes.com/blog/scams/2024/12/repeat-offenders-drive-bulk-of-tech-support-scams-via-google-ads. 4
How do threat actors bypass 2FA?
Of the various ways through which attackers gain access to 2FA codes, three prominent methods that hackers could use within Google Ads are explained below and include:
(1) Social engineering and phishing: Social engineering tactics may occur via email, text phishing, or even voice phishing where the threat actor may pose as a trustworthy or authoritative figure asking for a code sent to your device. This method of phishing can be used to easily gain access to 2FA codes.3
(2) Reset Password Tactics: This common tactic occurs when a threat actor simply asks for a reset password for their target. Given that many websites do not have a second layer of protection or verification for their 2FA password resets, threat actors can directly access the accounts.3
(3) SIM Swap: SIM jacking is one of the popular methods for threat actors to get their hands on 2FA codes where the actor hijacks a SIM card and poses as the owner associated with the SIM Card. 3
What preventative measures can be taken to strengthen MFA?
- Avoid the use of short OTPs and instead opt for longer alphanumeric combinations that are much harder to crack 5
- Use biometric authentication as at least one factor of authentication 5
- Avoid SMS-based authentication factors where possible 5
- Restrict the use of unsanctioned applications, this is where threat actors plant malware to hijack your devices 5
- Monitor your attack surface as cybercriminals can exploit external vulnerabilities such as poor network security 5
Bibliography
[1] https://thehackernews.com/2025/01/google-ads-users-targeted-in.html
[3] https://www.mitnicksecurity.com/blog/bypass-2fa


Great post Keerthana!
This campaign serves as a powerful reminder to remain cautious when using online platforms, even those we trust. It also highlights the ongoing responsibility of major tech companies to enhance their security measures to safeguard users from increasingly sophisticated cyberattacks.
Cyberattacks often exploit users’ lack of awareness, which means people are vulnerable until the tactics behind these attacks are exposed. It’s crucial to stay curious, ask critical questions, and exercise vigilance with every action taken online. Cyber threats lurk everywhere, manifesting in many different forms!
Great post Keerthana!
This campaign serves as a powerful reminder to remain cautious when using online platforms, even those we trust. It also highlights the ongoing responsibility of major tech companies to enhance their security measures to safeguard users from increasingly sophisticated cyberattacks.
Cyberattacks often exploit users’ lack of awareness, which means people are vulnerable until the tactics behind these attacks are exposed. It’s crucial to stay curious, ask critical questions, and exercise vigilance with every action taken online. Cyber threats lurk everywhere, manifesting in many different forms!
Great insight! I used to think that if scammers use Google Ads to advertise and scam people, their accounts should simply be taken down. However, I now understand that those accounts might be legitimate but could have been hijacked.
Great post Keerthana. The fact that attackers exploit gaps in Google’s ad policies, such as mismatched display and final URLs, reveals an urgent need for stricter oversight and more proactive measures by Google. While Google’s removal and suspension of billions of ads is commendable, it’s clear from this post that there are still significant loopholes being exploited, with some malicious advertisers reportedly remaining active even after being flagged multiple times.
Super interesting Keerthana, it’s interesting to see how google is struggling and being exploited letting these scams and malware spread through google ads. While I was working at a job, we had a couple of incidents that we eventually traced back to the user clicking on the first thing in a google search which was a fake google ad sending them to a phishing or fake website of the one they were looking for. It seems that it has now evolved to phishing the google ads itself. I really like your recommendation for strengthening of MFA by avoiding SMS-based authentication. With reading other blogs and doing my own research about SMS when RCS came out on Apple, I come to know that SMS is really insecure and should never be used especially for MFA codes.
Thanks for this insightful post Keerthana. Privacy concerns with the Google platform have always been a significant issue, and this example does well in highlighting some of the challenges involved. I personally avoid clicking on sponsored links to reduce the risk of falling victim to these scams. While we know that Google has controls in place, it is clear that these threats will always remain difficult to fully or completely contain. I completely agree that users must take responsibility for doing their own dilligence in protecting themselves and also being vigilant enough to avoid falling for one of these scams.
Great post, Keerthana!!! This post really opens my eyes to how sneaky cybercriminals can get! I always thought Google Ads were safe, but it seems even they can be a playground for hackers. It’s scary to think that clicking an ad could lead to losing your account. Thanks for the heads-up; this definitely makes me rethink how I interact with search ads. I hope Google steps up their game to keep us safer
Keerthana, this is a well-documented analysis of how malicious actors exploit Google Ads for phishing and malvertising. The breakdown of the methods used, particularly the exploitation of Google Ads policies like mismatched display and final URLs, is enlightening. Through your post, I learned about the extent to which Google Ads is exploited to conduct malvertising campaigns and how attackers use advanced techniques like WebSockets to bypass 2FA.
Thank you for shedding light on these critical vulnerabilities and the innovative strategies attackers are employing today.
Great article Keerthana! Thanks for the detailed breakdown of how these scams work and how attackers are getting around 2FA. The screenshots are super helpful too because they show exactly what to watch out for. The way cybercriminals are exploiting Google Ads to deceive people into revealing their login credentials are really concerning, and it’s frustrating that Google hasn’t done enough to prevent it. I hope they’ll step up their efforts soon to better protect users from these scams.
Really insightful post, Keerthana! This campaign really drives home how important it is to be cautious online, even on platforms we trust. Cyberattacks often take advantage of our lack of awareness, and the fact that attackers are exploiting loopholes in Google’s ad policies, like mismatched URLs, shows just how much more needs to be done to strengthen security. Google’s efforts to remove billions of malicious ads are great, but it’s clear some bad actors are still getting through. I agree with you that we all need to take responsibility for our own online safety by staying alert and avoiding sketchy links. Even with Google’s controls, these threats keep evolving, so both users and tech companies need to keep stepping up their game to outsmart cybercriminals. Thanks for the breakdown of how these scams work and for the helpful screenshots—they really show exactly what to watch out for.