What Happened:
It was reported on January 10th that the US Treasury department was victim of a hack that occurred a month earlier on December 8th. The US Treasury has since called it a ‘Major Incident’ and called in the Cybersecurity and Infrastructure Security Agency (CISA), FBI and other intelligence organizations for help in containing and investigating the incident. The attack is believed to be done by a Chinese sponsored hacking group called Silk Typhoon.
What Was Affected:
The hackers where able to get access to over 400 computers and over 3000 unclassified files. The hackers were targeting computers and files focused on the topics of sanctions and international affairs and intelligence [5]. This led to documents with information related to policy and travel, organizational charts, materials on sanctions and foreign investment, and ‘Law Enforcement Sensitive’ data all being accessed and leaked. The last one of ‘Law Enforcement Sensitive’ data is related to the Committee on Foreign Investment in the United States (CFIUS) which is a committee that investigates foreign investments in the United States for national security purposes like real estate purchases and other foreign investments in the states.
Of potential greater concern among the affected computers are the Secretary of the US Treasury, Janet Yellen and other high-ranking officials. Just under 50 files were accessed on the Secretary’s computer including information like usernames, passwords, and the documents related to CFIUS.
Overall, the report says no high-value information within the Treasury department was accessed and emails and classified networks were untouched[5]. In addition, no long-term reconnaissance tools were deployed within the network and no signs of malware have been detected.
How did the Hack Happen:
The hackers used two CVE’s to gain access to the US Treasury department one of critical severity and the other of medium severity.
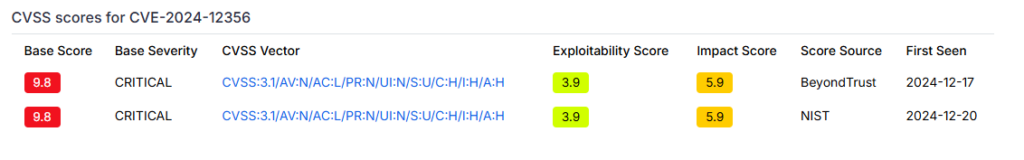
CVE-2024-12356 – A critical vulnerability has been discovered in Privileged Remote Access (PRA) and Remote Support (RS) products which can allow an unauthenticated attacker to inject commands that are run as a site user. [8]
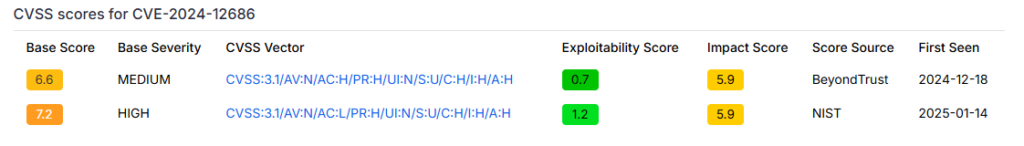
CVE-2024-12686 – A vulnerability has been discovered in Privileged Remote Access (PRA) and Remote Support (RS) which can allow an attacker with existing administrative privileges to inject commands and run as a site user. [9]
Theses vulnerabilities were present in BeyondTrust’s SaaS application which the US Treasury used for cybersecurity. When BeyondTrust noticed suspicious activity on a computer and further investigated and discovered the vulnerability and hack they notified the US Treasury. Later on December 16, these vulnerabilities where patched on their cloud instances.
CVE-2024-12356 attacks flaws in BeyondTrust SaaS applications Privileged Remote Access and Remote Support features. Attacking a vulnerable API endpoint which allowed hackers to execute code on the site as the user giving them privilege access to the user’s network. CVE-2024-12686 is then used once privilege access is gained to help keep persistence and run more commands.
Who is Silk Typhoon:
Also known as HAFNIUM (G0125), Silk Typhoon are very likely a state-sponsored cyber group in China. They have over 26 TTP accredited to them on MITRE. Given this latest hack and hacks on the Telecom industry, the US has placed sanctions on Shanghai company Sichuan Juxinhe Network Technology CO. which is believed to have ties to Silk Typhoon. The sanctions specifically target hacker Yin Kecheng, both the company and Yin have ties to the China’s Ministry of State Security. China’s Foreign Minister spokesperson spoke out saying these claims that the attack was state sponsored are “unwarranted and groundless”.
What this means for us:
For future security professional like us, this means we need to be aware that not all hacks and attacks on our systems are going to be from random hacking groups but can and likely will be from state sponsored groups sometimes. Though just because these hackers might be state-sponsored doesn’t mean we can’t do anything to prevent things like this from happening.
There are two things that the US Treasury could have done to help prevent this hack:
The first and main one is performing External Attack Surface Management (EASM). This is where the company looks at all outward facing endpoints and entry points into the company’s network (mapping their attack surface) and catalogues it to understand what’s viewable to the public. From there, the company needs to figure out which of these endpoints should be visible and why each endpoint is needed. If it’s not needed they need to get rid of it. After confirming the essential endpoints that are needed, known vulnerabilities should be scanned for and if any are found they should be patched. Having a EASM team and processes at a company helps the security team understand how they can be attacked and helps prevent future easily preventable attacks from happening.

The second thing the US Treasury could have done is better patch management and communicating to their service provider BeyondTrust the importance of this. Making sure that patches are rolled out regularly and quickly ensures known vulnerabilities get addressed as quickly as possible.
References:
[1] https://www.csoonline.com/article/3632744/chinesische-hacker-attackieren-us-finanzministerium.html
[5] https://www.yahoo.com/news/treasury-hackers-focused-sanctions-intelligence-015705689.html
[8] https://www.cvedetails.com/cve/CVE-2024-12356/
[9] https://www.cvedetails.com/cve/CVE-2024-12686/
[10] https://attack.mitre.org/groups/G0125/


Great work! Hayden
This blog provides a comprehensive and insightful analysis of the recent cyberattack on the U.S. Treasury Department, attributed to the Chinese state-sponsored hacking group known as Silk Typhoon. The detailed breakdown of the vulnerabilities exploited, specifically in BeyondTrust’s SaaS application, and the emphasis on proactive cybersecurity measures, such as External Attack Surface Management (EASM) and effective patch management, offer valuable lessons for professionals aiming to strengthen their organization’s defenses. It’s a timely reminder of the evolving threats in cybersecurity and the importance of staying vigilant.
Great post Hayden! I agree that it is very important to know that adversaries are not always script kiddies, but professional hackers sponsored and motivated by governments. More and more governments are using this option as espionage and as a political weapon. I found it interesting how the vulnerabilities were in applications meant to be used as cybersecurity features. We must be sure of internal and external applications that the organization uses, no matter if they are in the cloud. Applying EASM and regular patching are good ways to avoid problems with applications and are good options to avoid this problem.
Great post! It’s ironic that the hack came through a cybersecurity tool meant to protect the organization. This highlights how critical vendor security is in the bigger picture.
Your point about External Attack Surface Management (EASM) really stood out to me; it’s such a proactive and essential strategy that many organizations unfortunately overlook. Mapping and addressing external vulnerabilities before they can be exploited is a lesson every security team should take away from incidents like this.
Hi Hayden, something like this is very distressing to hear. I feel like the perception is that government agencies, especially one like the US treasury would be more secure than private companies. It looks like the CVEs where first seen that same month, so they were brand new. These vulnerabilities will keep popping up, and if the government is having trouble then there isn’t much hope for others. I like your suggestion of performing EASM, I think if we accept that things like this can happen, then the best solution would be to limit what they can access through theses outward facing endpoints. Great post.
I thoroughly enjoyed reading your work, Hayden. Great job! I was astonished to learn the sheer magnitude of the attack. Over 400 computers and 3,000 unclassified files were compromised, and the breached information ranged from sanctions, international affairs, and intelligence. What I found most interesting was the exploitation method for the vulnerable software. An attack of this magnitude requires large amounts of capabilities, in this case, the hacker leveraged the Privileged Remote Access and Remote Support tools, enabling unauthorized access and privilege escalation. After these vulnerabilities became present and the necessary defences were established to prevent this from occurring again, we as security professionals must understand the lessons that have been learned. Firstly, by mapping and monitoring outward-facing endpoints, we eliminate exposure and vulnerabilities proactively. Additionally, the rapid deployment allows for a reduction of exposure, specifically on zero day vulnerabilities.
Insightful post, Hayden. It seems that remote desktop/support software is in a state of perpetual abuse, whether that be the notorious Windows RDP, or as of late OpenSSH. On top of your excellent suggestions of trying to reduce attack surface through EASM and regular updating, a more stringent firewall policy—particularly limiting the subnet or IP able to access such a sensitive service—would help in a defense-in-depth approach; even a broad IP ban such that only those from within the States could access the port would help tremendously in denying state sponsored hackers the ability to even probe services for potential vulnerabilities.
It is fascinating but terrifying how these hackers used two CVEs in sequence like that. One to get in, another to stay in. Really underlines the importance of updating software immediately when patches are available.
Great insights, Hayden! Your point about the importance of External Attack Surface Management (EASM) is crucial. Many organizations fail to map their digital attack surface, leaving unnecessary endpoints exposed to attackers. Given that the US Treasury was using BeyondTrust’s SaaS application, do you think more rigorous third-party security audits could have helped identify these vulnerabilities before they were exploited? With supply chain attacks becoming more common, it seems like organizations should focus not just on their own defenses but also on those of their vendors.
Great post Hayden. The recent cyberattack on the U.S. Treasury by Silk Typhoon, a Chinese state-sponsored hacking group, which exploited weaknesses in BeyondTrust’s SaaS application. It’s a stark reminder that even government agencies aren’t immune to these highly sophisticated attacks. What’s concerning is how the attackers targeted security tools, showing that we must secure both our internal and external systems, including cloud-based apps. Steps like External Attack Surface Management (EASM) and regular patching are key to reducing risks, especially with the constant emergence of new vulnerabilities. Ultimately, it’s a call to action for all of us to stay vigilant by monitoring access points and responding quickly to minimize threats.
Great post! This just shows how relentless these bad actors are and how they are constantly evolving and do not rest. State-sponsored attacks are specifically a major security risk and there is a need for organizations to be prepared to defend themselves against these state actors by rolling this into the organization-wide enterprise risk.