Browser Syncjacking is an exploit that takes advantage of the google sync functionality of the chrome web browser to hijack a user’s browser. Google sync is used to sync a google account across multiple devices to ensure that what ever you do persist from one device to the next. Malicious actors have found a way to use this to takeover a target’s device.
This method was discovered on Jan 23rd, 2025 by security researchers at SquareX[1], and as they explain it, the process involves three steps; profile hijacking, browser hijacking, and finally device hijacking.
Profile Hijacking
First the attacker buys a domain and links it to a Google workspace account. The attacker can then disable any security settings such as MFA. This allows the attacker access to a list of users that are tied to his domain on the google workspace account. The next step is to create the extension (with basic read and write permission) and get people to install it on chrome. This can be done in a myriad of ways, from social engineering through emails or just a legitimate ad campaign on YouTube or other social media platforms. Note the extension may actually provide a service, like monitoring stocks or finding coupons for amazon; the malicious part can be an add on.
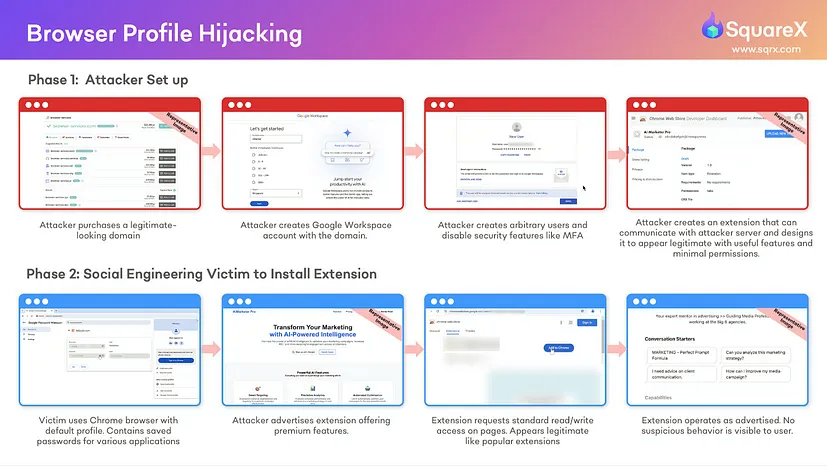
Once the extension has been installed, it will open a hidden window where it will authenticate a user profile that was created on the attacker’s Google workspace account. It will then change to that profile which will automatically bring the user to the official support.google.com page where google will ask the user to turn on chrome sync. If the user turn on google sync then all of their local data including browsing history passwords extensions and so on gets mapped to the profile that was logged in and connected to the attackers google workspace. All the attacker has to do is log into the same profile.
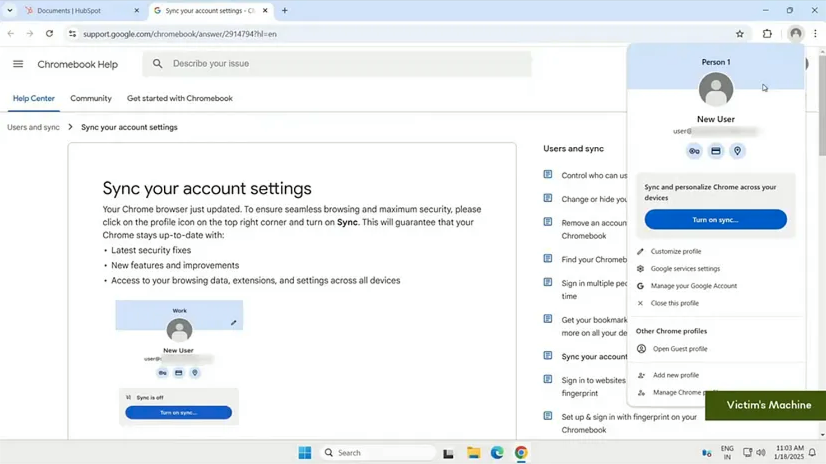
It is important to note that at this point the user is already fully compromised. The only alarm here would be the profile icon changing, but with some reconnaissance and social engineering the attacker can customize this. This is made easier when the target is enterprise related as those usually use the default icon.
by SquareX
by SquareX
Browser and Device Hijacking
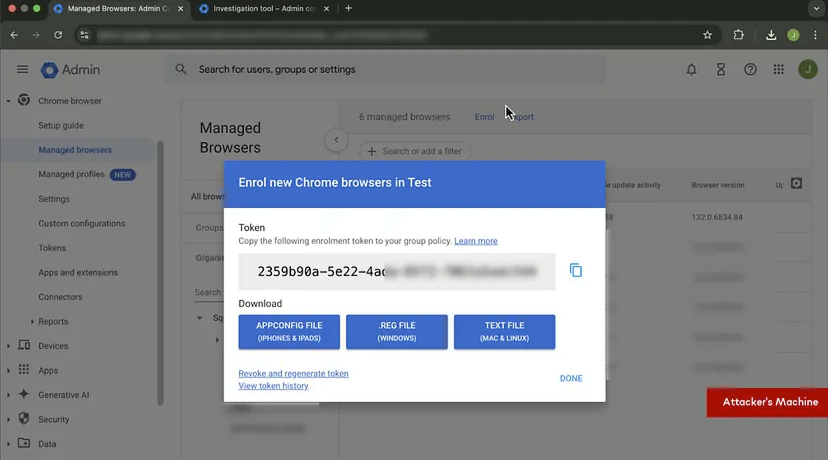
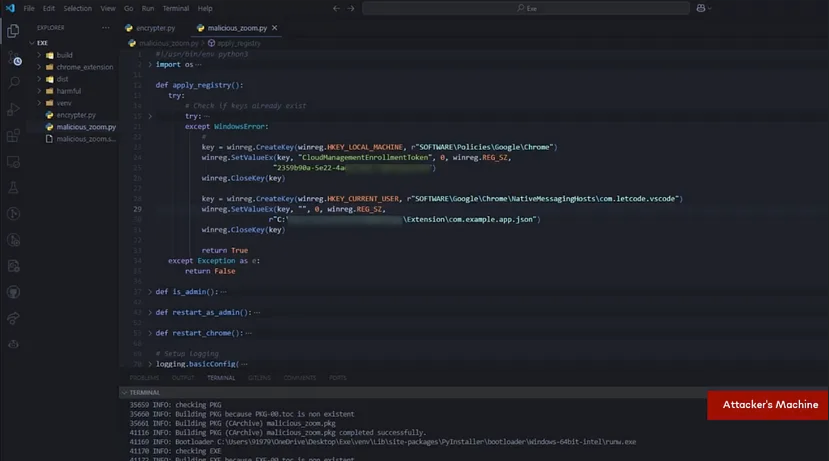
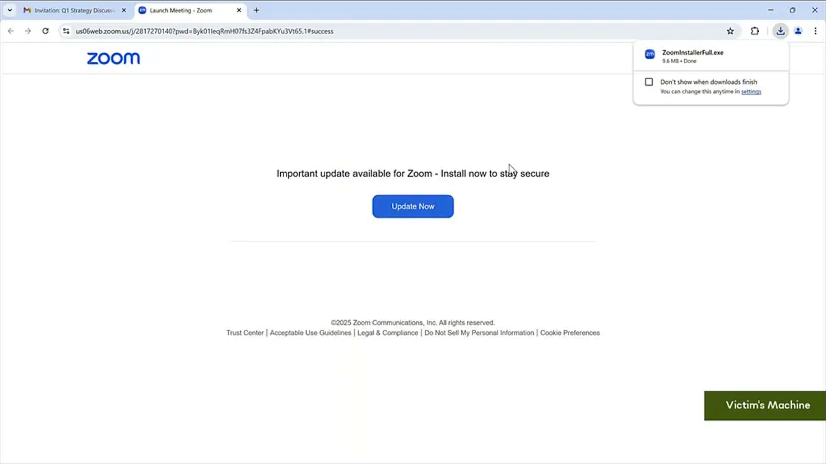
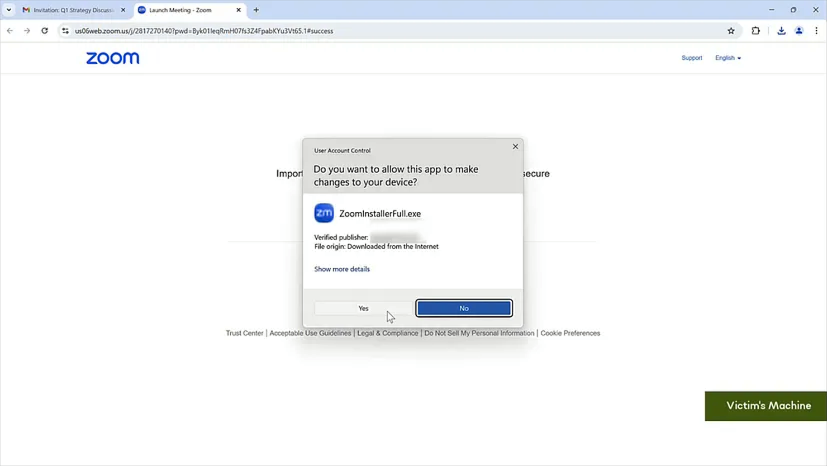
The next step is taking over the user’s entire Chrome browser and making it a “managed” browser under the attacker’s google workspace. This is done by creating enrollment tokens using the attackers google workspace account which is then packaged into and executable along with two registry entries; the first registry entry is to make the Chrome browser “managed”, and the second registry entry is to allow “Native Messaging” through a specific extension ID. In this case the executable is made to look very similar to the official Zoom installer, we can imagine that with more information this can be customized for the target and made to look like a different app that the user is more likely to “install” or “update”.
Using the zoom example, the next time the user receives a zoom link, the extension redresses the UI to make it appear that the victim’s Zoom requires an update. Again because this is on the
official Zoom page with an https connection, and no certificate error, the user is more likely to click on the update button which will download and execute this file the attacker has packaged.
by SquareX
by SquareX
when the executable runs the two registry entries one to make the browser managed and the second one to enable Native Messaging are both added to the users local machine. Now the Chrome browser restarts and when it launches it automatically picks up the enrollment token making the browser a “managed” browser with the attacker in control. The key thing here is that after this, the browser interface remains exactly the same, there are no visual changes to the user’s browser and the zoom page resets back to the original page where the user can launch the meeting as expected. This is important because as far as the user is concerned, Zoom was just updated and that is all that happened.
On the attackers end, now that they have a managed browser, they can turn of safe browsing, apply a bunch of different attributes and policies but most importantly, they can enforce additional malicious extensions that do not have to be screened by the webstore. These extension can do anything the attacker can envision. An example of this would be using a hidden window to silently authenticate a user into a third-party application that asks for full Google Drive read and write access. They can redirect websites, like instead of the official google docs website, you are redirected to a clone of it where they have access to all data that the user inputs.
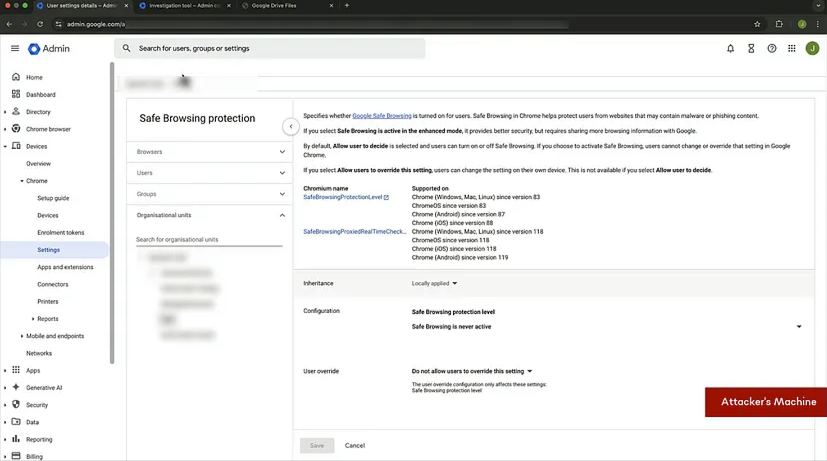
The final part is the Native Messaging registry that was enabled. This allows the attacker to to basically run any commands on the users machine through the extension while the responses are sent to the attacker over a websocket connection and the extension. This allows the attacker to directly access local directory files, edit them, modify them, add new files as well. All of this happens in an extremely stealthy manner and we can easily imagine something like this going on inside an enterprise machine for months before anyone notices.
The scariest part about Browser Syncjacking is just how little the user knows of what is happening. Every part of this has been tailored so well that it is hard to believe anyone would be able to notice. Gone are the days of the scary popups that are trying to download malware on your device.
[1] https://labs.sqrx.com/browser-syncjacking-cc602ea0cbd0
[2] https://www.bleepingcomputer.com/news/security/new-syncjacking-attack-hijacks-devices-using-chrome-extensions/


Helpful post for regular browsing , Abdul! To avoid Browser Syncjacking, we never install browser extensions from untrusted sources, even if they promise to provide some useful features. Be suspicious when Chrome asks you to enable sync out of a blue moon, especially after you have just installed an extension. Regularly go through your extensions and remove the ones you either don’t recognize or no longer use. Keep multi-factor authentication on for your Google account to avoid profile hijacking; enable and keep it strong. Keep your browser and operating system updated with the latest security patches; these reduce vulnerabilities. Finally, beware of updating/installing software from non-official sites since they may be malware in disguise. These are some important and necessary lessons we must take from this post, thanks a lot again to create such awareness.
Hi Fahim, thank you for the great suggestion. Something I want us to keep in mind is how pernicious this can be. I think the scariest part is how they can get you to click links of official sites like google and zoom that do something that we don’t expect. Something that I also forgot to mention is that all of this doesnt have to happen right away, they can program it to begin these processes after the 3rd time you open the browser. At that point it would be impossible to notice anything and diagnosing something like this could take forever.
Thank you for this enlightening blog. The fact that it all starts with something as innocent as a browser extension is alarming. I’ve always been cautious about installing random extensions, but after reading your blog, I feel like even that isn’t enough. Over the past few years, I’ve downloaded some extensions to block random ads disrupting my browsing experience, but now I think I need to revisit them and uninstall all of them funny, right?
The social engineering aspect is particularly dangerous because people tend to trust platforms like Google and Zoom. If an update prompt looks legitimate, most of us wouldn’t think twice before clicking on it. That’s exactly how the old and inexperienced me might have installed a malicious extension without even realizing it. Thank you once again Abdul!
Hi mohammed, I agree completely. Something I forgot to mention is that a lot of these extensions already exist. Take a simple extension that does text to speech for example. This would be trivial to implement and all a bad faith actor would have to is cope the name and logo of the most popular version on the play store, add a 2 behind and release it. They might even promise some new AI features. This new extension would have free marketing from the original version, and any new customers who want to try the original that see the fake version might be tempted to click the fake one. It doesn’t even have to be a high success rate, and once you download the extension and try it out, you wouldn’t even be able to tell something was wrong. These are the types of scams that I think browser hijacking would be perfect for, and I am not sure exactly how to address this.
Well done! It is particularly concerning since an attacker can take over a user’s browser and turn it into a “managed” browser. The attacker uses several entry points and a deceptive approach, which makes it difficult for users to identify or stop. This is an excellent illustration of how hackers can carry out a sneaky and significant breach by taking advantage of weak security procedures, user behavior, and the connectivity of modern gadgets. As a result, users and organizations need to be careful to check permissions, protect their accounts, and educate themselves on the dangers of installing extensions or software they are not familiar with.
Since attackers are always evolving and discovering new ways to get around established security measures, the battle against these threats is probably going to be a continuing one. As such, it is important to stay vigilant and alert in order to effectively manage these risks.
Really interesting and scary post Abdul, great job going into how each step of the attack works and what is visible by the user to see if they would be able to notice the attack happening, which in this case seems like almost nothing which is scary. I think the moral of the story is to never install, download, or allow access to programs or extensions you don’t know or trust. Anytime you download something do due diligence on it to see if it’s trusted and reputable. There are many websites that let you vet downloads and browser extensions so people should use them before downloading anything. I like your point in the blog about considering this in an enterprise situation where this could go unnoticed for months, which shows us as security professionals the importance of managing what can have access on enterprise computers and cracking down on shadow IT.
Hi Hayden, I think something we can do as IT professionals, especially in an enterprise environment is have a list of approved apps, browsers, etc. We need to make sure that what employees are using are secure. If someone wants to use a new app or download an extension we need to make sure there is a review process for that. One that includes a thorough code review for starters. Something else to consider is that employees might work from home on a personal device or ssh into a network. The issue with this is of course that we have way less control. I can imagine a scenario where someone’s browser is compromised and as part of this they had there username and password that they use to log into the company portal. In cases like this they best we can do is regular auditing. Honestly it terrifies me to think of how much harder to detect these vulnerabilities will be, especially with the advent of AI.
Nicely written Abdul! Wow, this is a real eye-opener, Abdul! It’s crazy how attackers can sneak in so smoothly without users even noticing. The fact that something as simple as installing a browser extension can lead to a full device takeover is pretty wild. I think the scariest part is how easily this could fly under the radar, especially in a work environment. It really makes you realize how important it is to double-check everything you download and stay on top of security settings. Great post—definitely makes me more cautious about my browser!
a. It’s truly alarming how seamlessly attackers can disguise their actions, making it almost impossible for users to detect the breach. This really brings home the importance of educating users about potential threats, staying vigilant, and having proactive measures. The question is though, how does the average person keep up with all of this? We stay on top of this because our profession commands it so, yet for the average person this probably doesn’t cross their minds as often – if at all. As cyber threats evolve, staying informed and vigilant is crucial in safeguarding personal and organizational data. Your blog provides a thorough eye-opening analysis and breakdown – showing just how important what we do is.
This is really informative. Thanks for sharing, Abdul!
This type of attack highlights the evolving nature of cyber threats. Rather than launching direct attacks, cybercriminals are exploiting legitimate browser functionalities to maintain access and steal sensitive information. To mitigate these risks, continuous monitoring, promoting cybersecurity best practices, and enforcing strict regulations on browser extensions are essential.
Great post, Abdul! Reading more into this Browser Synjacking method highlights a concerning example of how cybercriminals are leveraging trusted browser features for malicious purposes. I was surprised, and quite taken aback when reading that this attack method can completely compromise a user’s browser and eventually their entire device without sending any obvious warning signs, making it particularly dangerous. As you mentioned, disabling Google sync would be a good strategy to implement along with limiting the installation of browser extensions, especially from unknown developers. Such situations remind us how everyday tools can be used against us very quickly, if not cautiously.