What Happened?
Security researchers from HUMAN’s Satori Threat Intelligence team were able to discover a massive ad fraud campaign that was being distributes through over 200 mobile apps available in Google Play Store. They named the whole campaign “SlopAds”, to signify the mass-production of malicious apps and the use of generative AI throughout the campaign.
What Was So Special About This Attack?
The SlopAds campaign was executed in very clever way, that would allow it to go undetected for extended periods of time. If one were to download a malicious app directly from Google Play Store, the app would not show any anomalous activity, and would act as advertised. This ensured that, whenever an audit of the app was being performed, it would not detect any signs of malicious activity as, this is the likely way these apps would be installed by specialists.
The only way to make such an app to do something unusual was to download it from Google Play Store through one of associated ad links that were also part of the campaign. After being downloaded, an app queries a mobile marketing attribution SDK to check whether its download was a result of a user clicking on the add. In this case, an app’s internal switch would flip, indicating that it is safe to perform an attack. It would then contact the Control&Command (C2) server and download four seemingly harmless PNG images. Each of the images would contain a portion of a malicious ad module, called “FatModule”.
After all four images are downloaded, the portions of FatModule are then encrypted, reassembled and executed. After few additional checks, the real attack is ready to start.
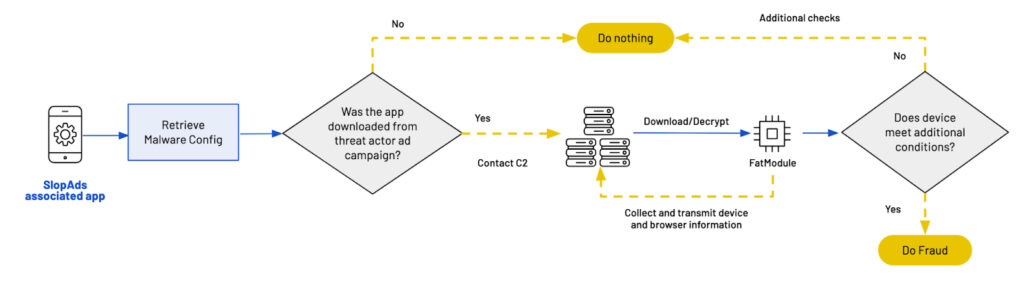
Following FatModule execution, it would send create several hidden WebViews in the background, each of which would load an associated website filled with ads. These WebViews would then generate numerous ad impressions and ad clicks for as long as they are open.
Who suffered from the campaign?
The first candidate that comes to mind is the end user. Since SlopAds required several WebViews to be active at a time, which is comparable to running several instances of a regular web browser, it put a significant strain on batteries and other device resources.
On the other hand, the real targets of the campaign were the ad providers, who had to respond to about 2.3 billion ad requests per day, and pay for the fake SlopAds ad impressions and clicks.
Outcomes
Following the HUMAN’s Satori Threat Intelligence team report, Google ended up taking down 224 apps that the scientists were able to identify. Google Play’s Play Protect automatically blocked these apps on end-user’s devices (Given that Play Protect was enabled).
Additionally, researchers were able to detect about 300 domains that were used to advertise the malicious apps. All of them linked to the original C2 server at ad2[.]cc, further confirming that all of the domains were part of the campaign. HUMAN suggested that the actors behind the SlopAds were likely preparing to expand the campaign, and it is likely they will attempt to push a new wave of fraudulent software in the near future.
As said by Gavin Reid, CISO at HUMAN, “SlopAds highlights the evolving sophistication of mobile ad fraud, including stealthy, conditional fraud execution and rapid scaling capabilities”.
References
1. Thomas C. Google removes massive ad fraud campaign from Play Store. Android Police. 2025 Sep 17 [accessed 2025 Sep 19]. https://www.androidpolice.com/224-play-store-apps-deleted-slopads-fraud-campaign/
2. Arntz P. 224 malicious apps removed from the Google Play Store after ad fraud campaign discovered. Malwarebytes. 2025 Sep 17 [accessed 2025 Sep 19]. https://www.malwarebytes.com/blog/news/2025/09/224-malicious-apps-removed-from-the-google-play-store-after-ad-fraud-campaign-discovered
3. Lakshmanan R. SLOPADS fraud ring exploits 224 Android apps to drive 2.3 billion daily ad bids. The Hacker News. 2025 Sep 16 [accessed 2025 Sep 19]. https://thehackernews.com/2025/09/slopads-fraud-ring-exploits-224-android.html


Great post! It really shows how intricate this kind of attack can be.
They are good at disguising the attack, passing the Google store audit, using steganography and defrauding the ad providers. This shows that our phones were just the tool and means of transport to achieve their objective. Nowadays our phone is the most critical asset to our privacy. I believe android apps should be more rigorous in auditing than other types of devices.
Agreed! Ideally, Google should implement the F-Droid approach to auditing the apps.
(F-Droid is an alternative app store to a Google Play with ONLY open source apps). In more detail, F-Droid’s approach lies in ACTUALLY checking what is inside the app (reading the source code), building then the app themselves, and offering that audited version.
Now, with SlopAds, Google would only identify something malicious if they followed the ad link (like HUMAN’s Satori Threat Intelligence did), or by examining the source code of the app (which, as I said earlier, is what F-Froid does, and Google Play should do, if they want to increase quality and safety of apps they provide).
Really interesting read ! The one thing that particularly caught my attention was the fact that SlopAds leveraged the conditional execution of the malicious code when the app was downloaded through an ad link. This highlights the fact that most security tests assume direct download and not ad-driven installation which is more closer to what happens in the real world. Another consequence of this vulnerability was that the malicious program affected not only end users but also the ad platforms.
Good work!! The SlopAds campaign was a groundbreaking ad fraud campaign that hid Malware in plain sight on Google Play. Applications operated normally apart from being installed via some ad links, whereby they reassembled concealed modules to produce fake ad clicks. The fraud drained device resources and cost ad providers billions of fake impressions. Google did end up removing the apps, it shocks me how sophisticated mobile ad fraud has become and how even authorized app stores are not secure.