In June 2024, a ransomware attack broke into the National Data Centre in Indonesia and interrupted major services across the nation. The attackers who appear to be part of a ransomware attack group ‘LockBit’ demanded a ransom of US$ 8 million [1]. The Brain Cypher ransomware was shrouded in several forms and deployed in the national data centre. As a result, Indonesia was temporarily brought to a standstill. Immigration services were affected as most services were temporarily jammed even in airports where all document management systems fell leading to the loss of vital data [2]
Who/What is Brain Cipher
Brain Cipher is a relatively new ransomware operation that made headlines after their malware breached the National Data Centre of Indonesia. They probably created their virus through the leaked LockBit 3.0 builder, as the ransomware they used is almost an exact clone of the builder[4].
Brain Cipher didn’t include the ransom amount or wallet address in the ransom note, only a link to a Tor-hosted communication page with those details. Brain Cipher also has its own site on which it lists leaks, but it appears it’s only being used for live victims in order to pressure them into paying the ransom demanded.
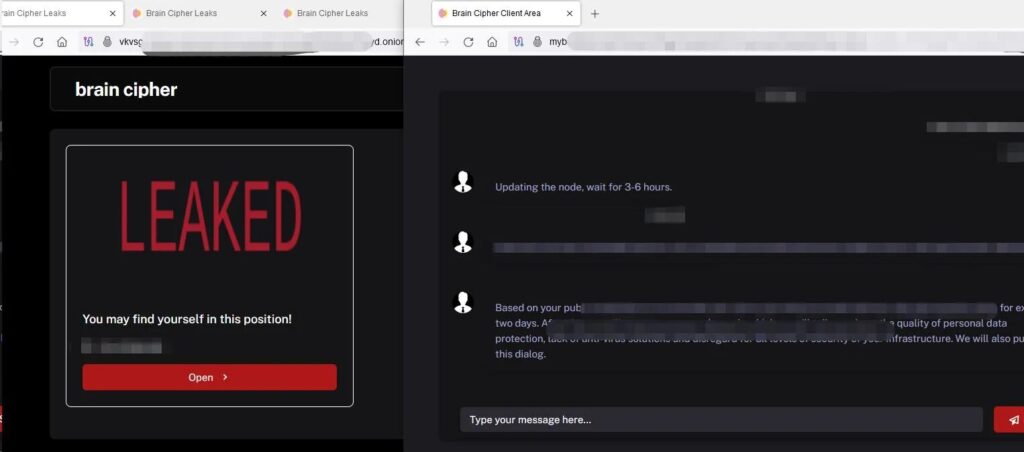
Figure 2: Brain Cipher’s Incomplete Leak Site and Communication Page [3]
LockBit Ransomware: What Is It?
The vicious LockBit ransomware locks the victim’s computer files and demands payment to unlock them, after seizing and encrypting the files. The LockBit ransomware first appeared in 2019 and operates as a ransomware-as-a-service (RaaS) business where affiliates receive the ransomware, create vulnerabilities in a target, then encrypt files and split ransom rewards with LockBit operators. Industries that have, and will continue to be, targeted by LockBit include healthcare, industrial and financial services. LockBit is noted for how quickly they can encrypt files and maintain stealth [3].
Immediate Repercussions
The strike was felt against the wide-ranging array of government departments that provide digital services for passports, visas, immigration, and residency permits. The retaliation to the attack was widespread and fast. Immigration services in Indonesia were slowed down and disrupted for travellers at the nation’s main airport. Foreign nationals and citizens had problems getting through border security, getting issued a visa, and other essential immigration services, resulting in huge queues forming at the airport [2].
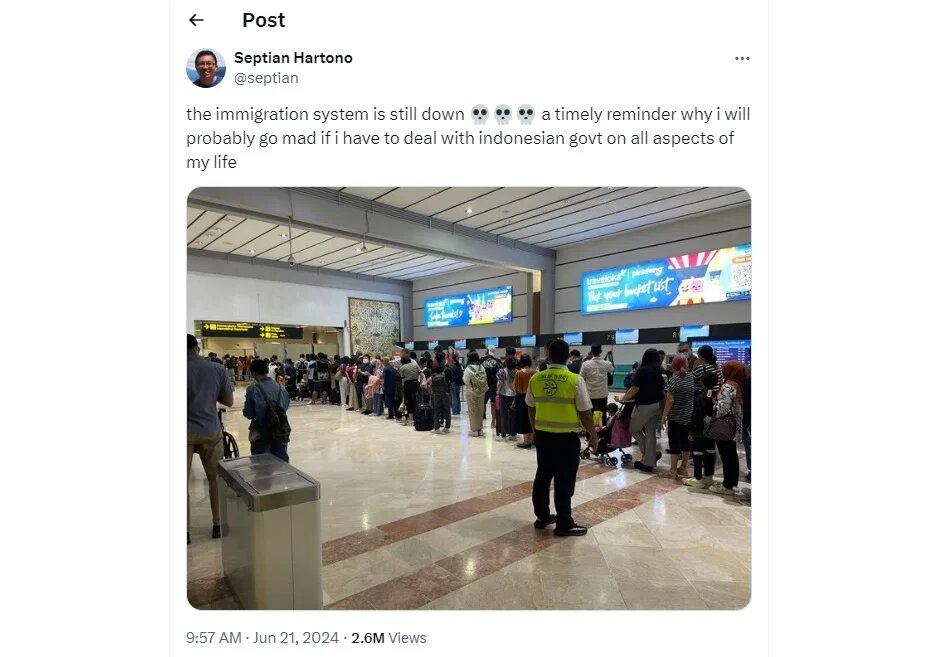
Source from X [7]
What was done to stop the attack?
They had to back up critical data to Amazon Web Services to get the whole unit functioning again and to do more diagnostics.
In the wake of the hack, the Indonesian government immediately launched a nationwide audit to evaluate the security of data held in all of Indonesia’s national data centres, to identify any possible weak points that could have enabled an attack like this one, and to try to ensure so that this doesn’t happen again. Some key areas of attention include:
- Making sure good backup and recovery plans are in place to ensure that they’ll never have another episode like this and lose data.
- Regulating and putting in place proper access control policies and effective encryption principles.
- Establish mechanisms of monitoring their systems in expedited conditions to enablethem to easily and efficiently spot possible threats.
For Indonesia, the tragedy peaks with deep relevance since it has compelled the government to rethink its strategy in the domain of cybersecurity and consider it as the utmost objective in protecting the core of the digital infrastructure [2].
Breach’s Effects
Following the ransomware assault which led to atrocities in Indonesia’s airport, many travellers were made to wait in long queues just to have their passports checked manually. In some Indonesian airports, when travellers are in transit, they are required to go through customs and immigration where computerized kiosks are often utilized to check passports, however, these services stopped working as well. Making it difficult for them to use these systems [6].
Also, Ferries had to endure hours of queuing as there were glitches with the booking systems and staff had to handwrite details of passengers and transactions instead of using digital means [5].
It triggered public anger due to how they were adversely affected by the attack and the public vented their frustration over the social outlets.
What can we learn?
The lessons that can be taken from the cyberattack on the National Data Center of Indonesia are:
- Importance of Backup and Recovery Plans: Indonesia lacked quite effective backup plans, a vulnerability that they could have avoided during the attack. They could have induced a lesser extent of damage by ensuring that they had adequate backup policies.
- Critical Infrastructure Should Be Prioritized: this attack raised the issue of governments giving priority to protecting data infrastructure as it is part of national security. They must ensure that systems that support critical activities such as healthcare, and immigration remain secure.
- Cyber Defence Must be Pre-emptive: even though ransomware attacks have been and will continue to be a common occurrence, dependence on reactive responses will not suffice. To effectively mitigate attacks once they’ve begun, both corporate and government entities must incorporate pre-disaster planning such as active threat detection, regular treatment of threats, and incident rehearsal exercises[5].
Even if the Indonesian government may not have taken the necessary tips to protect any data, it had so turned out that the operation of the cyber crimes globally is very organized and rather complex that no single authority is capable of averting it fully. Organizations need to ensure that they are prepared for such a situation and have backups that will support critical operations.
Looking Forward
The Indonesian National Data Center ransomware attack in 2024 demonstrates another case of a rapidly evolving trend that every future cyber threat perception must reckon with. As there is no accurate answer regarding which of these stalks is likely to come, it is good for people to be on the lookout and brace themselves for any oncoming waves of focused cyber intrusion.
References
- CSIS Programs: Significant Cyber Incidents. June, 2024. https://www.csis.org/programs/strategictechnologies-program/significant-cyber-incidents
- Sangfor Technologies: Ransomware Breach Disrupted Indonesia Immigration and Other Government Services, Jul 2024. https://www.sangfor.com/blog/cybersecurity/ransomwarebreach-disrupted-indonesia-immigration-and-other-government-services
- Sangfor Technologies: LockBit Ransomware: Insights from 4 Years of Tracking, Dec 2023.
https://www.sangfor.com/farsight-labs-threat-intelligence/cybersecurity/lockbit-ransomwareinsights-from-4-years-of-tracking - Sangfor Technologies: What is Brain Cipher? The Ransomware that Took Down the Indonesian National Data Center, Jul 2024. https://www.sangfor.com/farsight-labs-threatintelligence/cybersecurity/what-is-brain-cipher-ransomware-took-down-indonesian-nationaldata-center
- Reuters: Cyber attack compromised Indonesia data centre, ransom sought, June 24, 2024.
https://www.reuters.com/technology/cybersecurity/cyber-attack-compromised-indonesiadata-centre-ransom-sought-reports-antara-2024-06-24/ - Scott Ikeda: Indonesian National Data Center Hit by Cyber Attack, Disrupting Government Services, Jun 2024. https://www.cpomagazine.com/cyber-security/indonesian-national-datacenter-hit-by-cyber-attack-disrupting-government-services/
- https://x.com/septian/status/1803970425569054749


Great piece Michael, regardless of how confident you might be when it comes to securing your systems, it’s super imperative to always have a data recovery plan in place. Cyberattacks will never stop, and neither will human errors. As cybersecurity students and future professionals, we must rigorously hone and enhance our security measures and protocols. We ensure that nothing could jeopardize our security standards, and the only way we can achieve this is by putting in place reliable and safe security measures. In such a situation, they wouldn’t have needed to expend as much time and money on recovery if they had reliable and trustworthy data recovery plans, as recommended by NIST in the link below. In conclusion, I would like to highlight the grave importance of having a good data recovery strategy for an individual or an organization.
https://www.nccoe.nist.gov/data-integrity-recovering-ransomware-and-other-destructive-events
Thanks Mohammed, Mohammed! I totally agree with you. Indeed a very useful data recovery plan is necessary in preventing such kinds of losses in cyber-attacks. We have to accept that one, the threat landscape will only grow over time as newer threats are developed. We need to focus on an area that is quite typically overlooked which is regular backups, and update of recovery strategy testing. These guidelines are quite important in such situations where time and focus are of the essence in bringing the affected parties back to a normal state. This should be a lesson to governments and even organizations to understand that their staff as well as their systems ought to be tested and proven to be effective in safeguarding data.
Awesome post, lucky that the Indonesian government was able to restore from back up instead of paying the ransom. I find it interesting that the malware instead of specifying the amount for the ransom and how to pay it that it directed to a website to do those things. I would think that making the website would make the attack harder for the hackers and expose more risk to them. Law enforcement can now investigate this website in addition to the malware to try and catch the hackers. I feel this might be one of the cases where cyber security takes a side role within planning and budget as it doesn’t show result but rather it’s the lack of a security event. This goes on until a cyber attack happens and now the Indonesian government is doing a deep dive to improve, they cyber security abilities so an attack like this doesn’t happen again.
Thanks Hayden! I am glad that Indonesia has been able to manage to restore their operations without paying the ransom. he use of a separate website for ransom details does seem risky for the attackers, as it could provide law enforcement with additional avenues for investigation. Still, this could also mean that the attackers were over confident in covering their traces. As you mentioned, planning and budgeting for cybersecurity is always the last thing people think about until trouble comes which is absolutely true. Let us hope that this particular incident makes other governments and organizations take a proactive stance to enhance their cybersecurity efforts before crisis occur.
Excellent work!. The Indonesian government’s efforts to halt the attack are commendable, but it is a never-ending race between those defending the program and those attempting to exploit system vulnerabilities. One must be vigilant and aggressive in securing diverse IT assets and personally identifiable information by investing heavily in cyber security to secure anything from personally identifiable information to sensitive corporate assets to government and military secrets.
I appreciate your thoughts John. I concur; the fight against cyberattacks is far from over, and in order to safeguard confidential information, defenders must always come up with new strategies. Although the Indonesian government’s response was praiseworthy, this incident emphasizes the necessity of constant attention to detail and funding for cybersecurity infrastructure. We have to continue being vigilant in seeing any dangers and making sure that data and systems are safe at all scales, from private to public.
Interesting post Michael!.
Its so surprising that with all the breaches in the news everyday, most organizations still do not prioritize securing their data against all possible attacks…or could it be they believe they have some superpowers to remain invincible to adversaries!. Hopefully, the Indonesian government and the rest of the world have learnt that Cybersecurity should never be underestimated as its impact ranges from large financial losses, reputational losses, operational losses and so many losses that we may not be able to account for.
Being proactive with security measures should never be undermined. I hope we all learn from this and know that not being victims today does not mean we are safe.
Interesting post Michael!.
Its so surprising that with all the breaches in the news everyday, most organizations still do not prioritize securing their data against all possible attacks…or it could be that they believe they have some superpowers to remain invincible to adversaries?!. Hopefully, the Indonesian government and the rest of the world have learnt that Cybersecurity should never be underestimated as its impact leads to financial, reputational, operational and so many other losses we may not be able to account for.
Being proactive with security measures should never be undermined. I hope we all learn from this and know that not being victims today does not mean we cant be victims of cyberattacks tomorrow.
Thank you for your comment! I agree, it’s surprising that many organizations still overlook the importance of cybersecurity despite frequent breaches. The Indonesian ransomware attack highlights that no system is invincible, and a proactive approach is essential. Cyberattacks can have lasting financial, reputational, and operational impacts. Hopefully, this incident reminds organizations globally to prioritize and constantly improve their cybersecurity defenses to prevent future vulnerabilities.
This was a very thorough analysis of the ransomware attack! The amount of disruption that a single assault can create, particularly on a national scale, is shocking. Travelers must have thought the consequences on immigration and airport procedures were unimaginable. The idea that a single ransomware assault may stop all national services in a country is unsettling. It is quite eye-opening to see how Brain Cipher uses the LockBit clone. I agree with the important points you provided, especially about the necessity for improved backup and recovery procedures.
Informative post Michael! The ransomware attacks caused serious disruption to the critical services like immigration. This highlights that the evolving tactics by cybercriminals. Organization must put some effort in upgrading their security position as the cyberattacks are becoming more sophisticated day by day. This can include regular security audits, training employees, and the implementation of various threat detection systems.
Looks like there’s always something stronger and more sophisticated than before attacks are formulating in the cyber world. It calls for an increase in demand for the expertise to combat the threats out there.
Thanks for the share.
Thank you for sharing. It is always interesting to learn about governments being targeted by cyber-attacks. I think it highlights the importance of investment and strategic planning required by the government in cybersecurity research and development.