
Introduction:
At present, the healthcare system has become one of the most popular targets for cybercriminals. Cyberattacks on hospitals as well as on medical centers have increased drastically in recent years. On 26 September 2024, the University Medical Centre (UMC) Health System in Lubbock, Texas, was hit by a serious ransomware attack. This attack affected the crucial medical services and raised a concern about national security and how well the healthcare sector protects its patient’s information and their systems [1] [2]. This incident serves as a critical warning for us that to safeguard the healthcare system, we require good cybersecurity practices.
Immediate effects and reactions:
University Medical Centre (UMC) Health System, which is the only level 1 trauma center in a 400-mile radius, was attacked by a ransomware attack and forced UMC to take some strong immediate action. As a result, UMC took the following steps:
- Both emergency and non-emergency patients have been diverted to other local healthcare facilities via ambulance since September 26 [3].
- UMC disconnected its systems because of “unusual activity” resulting from a ransomware attack [3].
- There has been a failure in the phone system and patient portals [3]. UMC posted this on Facebook [4].
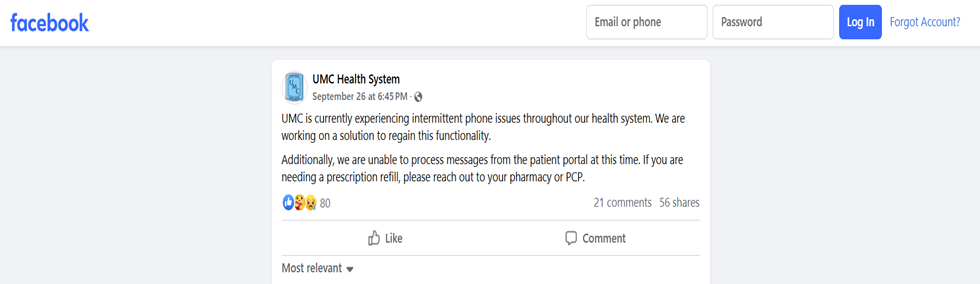
Figure 1 :Screenshot of a Facebook post by UMC Health System, UMC Health System Facebook Page, dated September 26, 2024 [4].
- A website was launched by the UMC Health Center to provide updates about the incident on 27 September [3]. The website link is as follows: https://www.umchealthsystem.com/it-outage/
- The health system brought third-party experts who have helped other hospitals with the same problems for recovery [1] [3].
- Even after the attack, the UMC Health Center managed to keep its emergency centers, urgent care clinics, and physician practices operational [1] [3].
Phases of Ransomware Attack:
John Riggi, National Advisor for Cybersecurity and Risk at the American Hospital Association, stated that there are two phases of a ransomware attack:
- Infiltration: Bad actors are gaining unauthorized access to the network, usually by working with a group that has speciality to identify the possible targets [1] [7].
- Execution: Once the attackers get unauthorized access to the system, they encrypt the sensitive information and may steal crucial information and hold it for the ransom [1] [7].
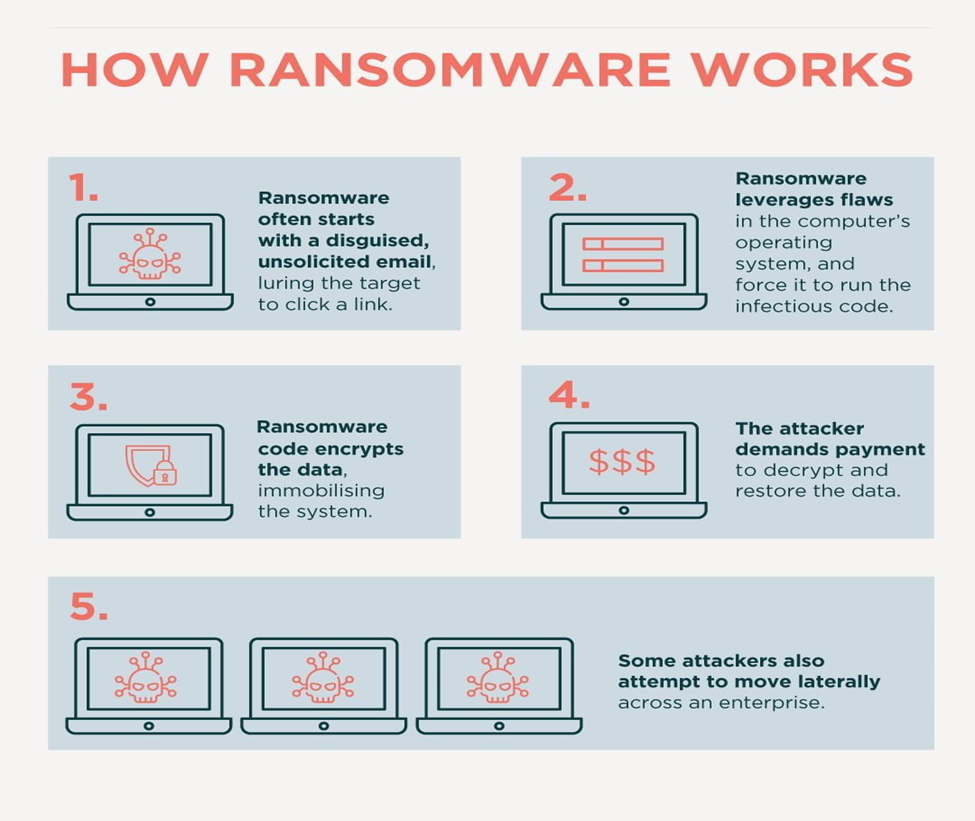
Figure 2: “How Ransomware Attack works” Image source: Trilogix Cloud. Accessed on 30 September,2024 [5]
Current situation at University Medical Center:
The UMC Health Center team is working hard to restore and recover things. The teams are working constantly, with the help of third-party experts, to check and address the issue. The investigation into this event is still ongoing. UMC Health Center will keep giving important news to their patients and community about the attack [6].
Right now, there is no specific timeline for restoration of service. After a ransomware attack, systems usually take about a month to get back to normal. UMC said, “We continue to carefully evaluate our operations with patient safety in mind.” We will only bring back services when it is safe [3].
A National Security Concern:
John Riggi, National Advisor for Cybersecurity and Risk at the American Hospital Association, classified this incident as a national security concern. He added that “when hospitals are attacked, lives are threatened.” When there is only 1 trauma center in a 400-mile radius and that is also shut down by foreign bad actors, making ambulances on diversion, you are putting people’s lives at risk, Riggi said. Riggi says that Russian crime groups, which often get protection from the Russian government, are mainly the ones behind these attacks. The FBI’s authority and power are limited when the attack is organized from the different countries. He also said that to effectively handle the increase in advanced cyber attacks, hospital systems will need help [7].
Conclusion:
The ransomware attack on University Medical Center is a warning for the entire healthcare industry. As the cybercriminals are using more powerful and smarter tools, the healthcare sector is required to focus more on protecting their systems and thereby, protecting their patient’s data.
In conclusion, UMC’s experience is a lesson for itself and other healthcare groups to improve their security against possible attacks. It’s very important for the field like healthcare to take these threats more seriously and work accordingly to protect their system against threats in the future.
References:
- https://www.betterworldtechnology.com/post/ransomware-attack-on-umc-deemed-a-national-security-issue
- https://www.hipaajournal.com/umc-health-system-responding-to-ransomware-attack/
- https://www.beckershospitalreview.com/cybersecurity/texas-health-system-confirms-ransomware-attack-6-things-to-know.html
- https://www.facebook.com/UMCHealthSystem/posts/pfbid021sT6cDyjhDxYEjj9YE6mD65twTCT14JbzkNbyLiq6oKsWZGSjcuGWVEUwbeQYkJVl?rdid=ISlgc3KcfLaZEpxF
- https://trilogix.cloud/cloud-design-goals/surviving-ransomware-attacks/
- https://www.umchealthsystem.com/it-outage/
- https://www.kcbd.com/2024/09/28/cyber-security-expert-calls-ransomware-attack-umc-national-security-issue/

Great job covering the topic !
This ransomware attack really highlights how vulnerable the healthcare sector is to cyber threats. It’s crazy to think how quickly lives can be at risk when a hospital is targeted, especially in a place like UMC, which covers such a large area.
The fact that UMC is the only Level 1 trauma center in a 400-mile radius makes this situation even scarier. Hopefully, this incident pushes the government and healthcare organizations to act faster on better protections.
Very insightful post Akshar. As indicated in the post, the ransomware attacks start with an unsolicited malicious email. Despite the ransomware campaigns conducted by security teams internally, there are always novice victims who open these malicious links. Surprisingly, the attackers now are getting more innovative in deploying these malicious links. Recently, they included these malicious links as QR codes printed images that can’t be detected by the anti-malware software. Once a victim scans the QR code the tragedy starts. In 2023, there were 5 hospitals in Ontario hit by ransomware attacks causing 3.4 million patients who needed pregnancy care and advice in Ontario (Aziz, 2023[1]).
[1] Cyberattacks on Canadian health care increasingly common. What can be done? .(2023, November 20). Retrieved from https://globalnews.ca/news/10103261/health-care-cyberattacks-canada
Thank you for your insightful comment, Tamer! In all the data breaches across all the sectors and industries, human error plays a very major role. According to the Verizon 2023 Data Breach Investigations Report, the human element is involved in 3 out of 4 data breaches and is a factor of 74% of total breaches. Even though organizations provide good training in cybersecurity to their employees and continuously work to protect their systems, cybercriminals often exploit employees through social engineering to gain unauthorized access to the organization’s systems [1]. Also, day-by-day, the bad actors are coming up with new tactics to trick people, which is also a major concern for security professionals. As you mentioned, recently, hackers included malicious links into the QR code-printed images that cannot be detected by anti-malware software, and once the QR code is scanned by someone, their system becomes compromised.
Ransomware attacks against the healthcare sector are increasing worldwide. The number of ransomware attacks against the healthcare sector in 2023 has almost doubled compared to 2022 [2]. The primary threat for the finance & insurance and healthcare industries comes from employees within the organization [3]. Trusted insiders were responsible for over 33% of the breaches in the finance & insurance and healthcare industries [3]. Now, as future security professionals, it is our responsibility to come with the latest technology and best security practices to tackle this type of attack on our critical infrastructure in the future.
1. https://www.verizon.com/about/news/2023-data-breach-investigations-report
2.https://www.dni.gov/files/CTIIC/documents/products/Ransomware_Attacks_Surge_in_2023.pdf
3. https://www.nextdlp.com/resources/blog/seven-takeaways-from-2023-verizon-data-breach-investigations-report
Thanks for the information Akshar! It was really interesting to know how these ransomware attacks work and the effects on such a crucial service such as the health sector. One point that got my attention is how the ransomware enters the system, as an email. With such a “simple” option, the whole system is vulnerable to such great harm.
These attacks in particular put lives at risk. I agree with you on making better standards and protocols to secure this important service. This will depend on each country’s regulations and health service capacity and how they perform the inspections.
There are options to protect and prevent ransomware, starting with constant personal training and awareness of phishing and social engineering and more technical options such as IDS, IPS and backups in case data is in risk of being lost. Great post. I really enjoyed it!
An important topic touched, nicely put together, great read, Akshay! Healthcare, in Canada is already strained with rising population and lack of skilled practitioners to support the system In such a situation our healthcare system is vulnerable to cyber attacks and data breaches. With lot of nurses, doctors overworked in a strained system, fatigue kicks and makes them vulnerable. Lot of the time the human issue does get overlooked, while we work on securing our systems and networks. According to Cybersecurity statistics 2024 [1]”Human error remains the leading cause of data breaches, often due to a lack of knowledge about essential safety measures” Even the most secure network can come down to its knees because of a single unintended click!
We need to make security as a habit and zero trust as a norm in our culture.
Great post Akshar!
Ransomware attacks are becoming popular across industries all over the world. Everyone has a role to play in having a more secure network and systems. Critical systems like we have in the hospitals need extra security measures to as lives are at risk and these attackers would do anything to hold networks hostage.!
The cycle of these attacks never ends, we can only secure and defend against these attacks.
Nice read Akshar!
Ransomware attacks are becoming popular across industries all over the world. Everyone has a role to play in having a more secure network and systems. Critical systems like we have in the hospitals need extra security measures to as lives are at risk and these attackers would do anything to hold networks hostage.!
The cycle of these attacks never ends, we can only secure and defend against these attacks.
Great job covering the topic !
This ransomware attack really shows how vulnerable the healthcare sector and sectors that are IT based are to cyber threats. It shows how attackers/hackers can go far to get sensitive information, and such can be used for malicious deals, especially in a place like UMC, which covers such a large area.
The government has to act fast to mitigate against future occurrence while they try to recover data from attackers, as it is more expensive recover data
Great Post, Akshay! Healthcare organizations have an extensive and often unprotected attack surface. Not only do hospitals have a wide range of connected medical devices (Internet of Medical Things, IoMT), but hospitals also consist of numerous third parties having access to sensitive patient data. For example, the increasing number of home working and virtual doctor’s visits (telehealth) prompted by COVID-19 and the rapidly rolled-out IT infrastructure have created even more opportunities for attackers to gain access to confidential medical information. Such attacks also provide attackers with capabilities to modify medical data. This could simply be disastrous. Tampering with medical results and data will lead to misdiagnosis and potentially even death of patients, in the worst-case scenario. While it is not only important to implement greater security measures, it is equally important to educate all staff working within hospitals from doctors and nurses to managers and team leads to ensure thorough understanding. Without increased awareness and proper education, all the implementation efforts are useless. Thank you for this informative post, Akshay!
Great Post, Akshay! Healthcare organizations have an extensive and often unprotected attack surface. Not only do hospitals have a wide range of connected medical devices (Internet of Medical Things, IoMT), but hospitals also consist of numerous third parties having access to sensitive patient data. For example, the increasing number of home working and virtual doctor’s visits (telehealth) prompted by COVID-19 and the rapidly rolled-out IT infrastructure have created even more opportunities for attackers to gain access to confidential medical information. Such attacks also provide attackers with capabilities to modify medical data. This could simply be disastrous. Tampering with medical results and data will lead to misdiagnosis and potentially even death of patients, in the worst-case scenario. While it is not only important to implement greater security measures, it is equally important to educate all staff working within hospitals from doctors and nurses to managers and team leads to ensure thorough understanding. Without increased awareness and proper education, all the implementation efforts are useless. Thank you for this informative post, Akshay!
Nice job Akshay, Ransomware attacks against the healthcare sector and even large industries and companies is on the increase worldwide. With this increase in vulnerabilities the human factor cant really be over looked because these hackers always have their ways of tricking the healthcare staffs in exposing their work information. So one of the great things that can be done is by giving frequent and proper training to staffs so they can be aware of the treats posed by the internet hackers into their systems.