The days of smart living is now! Its not in the past nor in the future, we are living smart! I can conveniently connect with devices with a sound of my voice, a tap of my finger or phone, a wave of my hand and so many interesting and easy ways! Isn’t that smooth?!… sure, it is!
IoT or Internet of things as defined by AWS, refers to the collective network of connected devices and the technology that facilitates communication between devices and the cloud, as well as between the devices themselves.
These IoT devices ranges from household items, tools to items found in offices and everywhere. Organizations make use of these IoT devices to efficiently and effectively carry out their day-to-day operations, deliver excellent service and improve the overall business. IoT devices has lots of benefits and has significantly improved lives and businesses.
The big question is, has IoT improved security in our day to day living and businesses or has it increased the attack surface?? Well, I think we all know the answer.
According to IoT Analytics, there were 16.6 billion connected IoT devices by the end of 2023 (a growth of 15% over 2022) and IoT is expected to grow 13% to 18.8 billion by the end of 2024. With these figures in mind and knowing that most IoT devices were built without security in mind but for convenience and efficiency, I think its time for a change.
There is a growing threat of cyber attacks against the rising number of IoT devices, standards need to be put in place to at least some extent mitigate these threats and help protect business and individuals from cyber attacks. Som examples of these IoT attacks include:
Cold in Finland:
In November 2016, cybercriminals turned off the heating in two buildings in the Finnish city of Lappeenranta. After that, another DDoS assault was launched, forcing the heating controllers to reboot the system repeatedly, preventing the heating from ever turning on. This was a severe attack since Finland experiences severely low temperatures at that time of year.
The Jeep Hack:
In July 2015, a group of researchers tested the security of the Jeep SUV. They managed to take control of the vehicle via the Sprint cellular network by taking advantage of a firmware update vulnerability. They could then control the vehicle’s speed and even steer it off the road.
IoT not only faces cyber attacks but also privacy issues from vendors. How is the data collected from billions of IoT devices stored and used? All these and more need to be addressed in setting a standard for IoT development and use.
According to Fortinet,
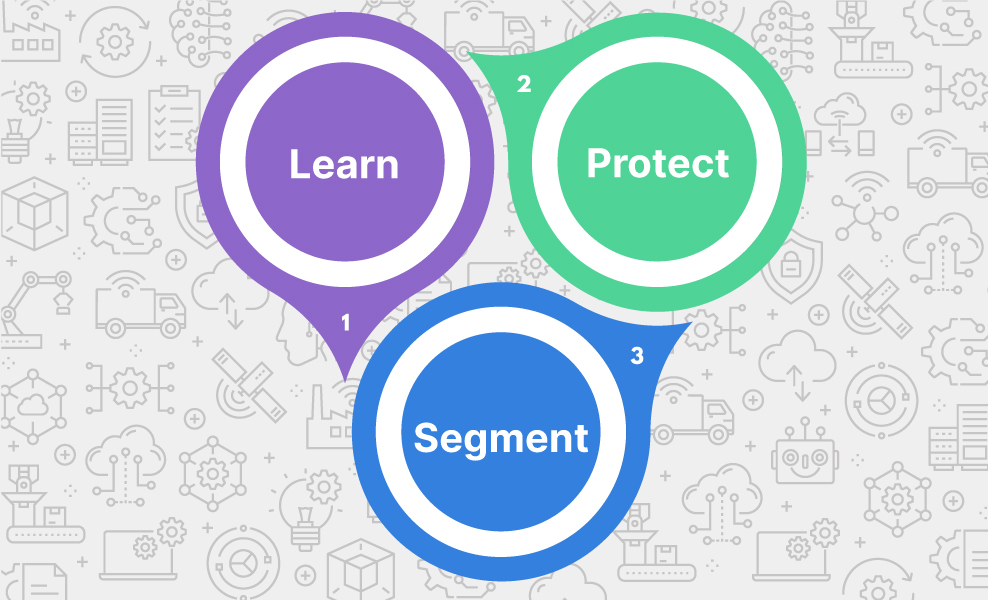
IoT and security requirements can only be accomplished with an integrated solution that delivers visibility, segmentation, and protection throughout the entire network infrastructure, such as a holistic security fabric approach.
Your IoT security must contain the following key abilities:
- Learn: With complete network visibility, security solutions can authenticate and classify IoT devices to build a risk profile and assign them to IoT device groups.
- Segment: Once the enterprise understands its IoT attack surface, IoT devices can be segmented into policy-driven groups based on their risk profiles.
- Protect: The policy-driven IoT groups and internal network segmentation enable monitoring, inspection, and policy enforcement based on the activity at various points within the infrastructure.
To get more information on securing IoT you can read this article here by Fortinet.
References:
https://www.techtarget.com/iotagenda/definition/Internet-of-Things-IoT

Nice post, Ukamaka. One unique nature of IoT is the constrained resources on these devices. The manufacturers of these devices capitalize on the functions of these devices to meet customers’ satisfaction, neglecting data privacy and security. Limited computational power on these devices hinders their ability to use strong encryptions. Although the emerging Lightweight Cryptography helps secure these IoT devices, adopting efficient cryptography in IoT is uncommon. I had a recent experience where I was able to trace all the network traffic inside my house looking for the smart IoT devices I deployed, and the finding is astonishing. Most of my IoT devices send data and instruction calls in clear plain text. Not only my cheap $7 camera but also my Samsung and Sony TVs, smart light pulps, and smart oven. The most furious fact is, that all my IoT devices are accessible without a single firewall rule on my router.. This makes me think, what if an attacker turns my oven and causes me insurance grief?
Thank you Tamer! Yes! most IoT device manufacturers focus on efficiency and give little thoughts to data privacy and security. Hopefully with the emerging lightweight Cryptography, data privacy and security in IoT devices would be a lot better. Your experience is both informative and scary! hopefully those IoT devices would be updated with better security measures.
Nice job Ukamaka! It was a really interesting topic. IoT is definitely a reality and we use these devices in our daily activities. It is interesting how important systems such as heating controls or car firmwares are vulnerable to attacks.
I think that sometimes these devices are not considered properly as a vulnerability for systems. It is important to recognize that they have an IP address and are connected to the network. Attackers are looking for any possible “gap” in the system’s security to enter and perform the attack. So it is important to consider all assets, even IoT devices such as cameras or sensors.
It is good to know that there are best practices to protect this kind of device. Following the learn, segment and protect practices will be a point to consider in every security analysis. Thanks for the information!
Thank you Oscar! I absolutely agree with you on considering all assets including the IoT devices when developing security measures and implementing a zero-trust policy on all devices connected to the network both internally and externally would also be a great idea!
Excellent work, Ukamaka! IoT devices have become an essential element of our lives. However, the rapid spread of these devices has presented serious security challenges.
The attack on heating control and firmware could also be attributed to delays in implementing security upgrades, making them vulnerable to compromising the device’s security. Moving forward, I believe that businesses and individuals should prioritize regular firmware testing and updates to keep their devices secure, as well as follow industry standards and regulations to ensure that IoT devices meet established security benchmarks.
By addressing potential security flaws and implementing effective mitigation techniques, businesses and individuals can create a strong security posture that protects their IoT ecosystems, data, and privacy. Many thanks!
Nice Job, i agree that IoT devices have made life easier, but the risk attached to using them is very high because of the security concern However, based on your write-up, it is good to know that it is possible to use the devices with the security from Fortinet if all the stated concerns are taken into consideration.
Great post Ukamaka!
It’s amazing how far IoT has come. The convenience of IoT is undeniable, but security needs to catch up fast. The idea of segmenting IoT devices based on risk profiles is a smart approach. With billions of devices connecting, a holistic security framework seems like the right solution to tackle these emerging threats. I hadn’t heard about the Finland and Jeep incidents before, those are serious reminders of the vulnerabilities in connected devices. Thanks for shedding light on such a vital issue!
I agree with the term “we are living smart!” That’s so true, and IoT is one of the main contributors to this revolution. We cannot think of a day without any IoT-implemented device. For example, my house has a smart door lock that unlocks with an auto-generative key each time. If this IoT device comes under vulnerability, then my whole house can be compromised. However, as we are depending on them day-by-day, we should be more careful while making it. As you mentioned, three key abilities should be implemented on them, which are learn, segment, and protect. Besides that, multiple layers of security can be implemented on those kinds of devices so that if one layer compromises, the other one holds. Additionally, an alert system and an auto-lock system should be implemented on every remote device. No matter how the security system must be implemented on them, as we cannot live without IoT devices in this era.
Excellent work, Ukamaka! IoT devices have become an essential element of our lives. However, the rapid spread of these devices has presented serious security challenges.
The attack on heating control and firmware could also be attributed to delays in implementing security upgrades, making them vulnerable to compromising the device’s security. Moving forward, I believe that businesses and individuals should prioritize regular firmware testing and updates to keep their devices secure, as well as follow industry standards and regulations to ensure that IoT devices meet established security benchmarks.
By addressing potential security flaws and implementing effective mitigation techniques, businesses and individuals can create a strong security posture that protects their IoT ecosystems, data, and privacy. Many thanks!
Great post Ukamaka. It’s amazing how IoT has transformed the way we live and work, making everything so convenient. However, the flip side is definitely concerning. Right now, it’s all about convenience and manufacturers keep making devices to make life easier. With so many devices connected, security often feels like an afterthought for many manufacturers. It’s clear that while IoT makes life very convenient, there is a pressing need for better standards and more robust security measures.
Great post, Ukamaka! Having so many devices capable of connecting to the internet does make our lives easier by being able to control things wirelessly and sometimes even remotely, but it does increase the attack surface for those networks. As we saw in class as well, attackers will go after the weakest link, and many people don’t think too much about the security of their TVs or cameras. I know a lot of people in tech who avoid such devices because of these security risks, as well as privacy concerns around the type of data they are tracking and sending to the companies who manufacture them. You talked about some great examples but another one you might find interesting is a case where a casino was hacked through an aquarium that was connected to the network: https://www.forbes.com/sites/leemathews/2017/07/27/criminals-hacked-a-fish-tank-to-steal-data-from-a-casino/
Amazing and informative post-Ukamaka! Upon further research on the statistics of such cases, it seems that the highest number of vulnerabilities was found on smart TVs, smart plugs, and digital video
recorders. Additionally, reports say there are an average of 21 connected devices in every home — some built into buildings and houses, others brought in by residents. This is a crazy number of connected devices through which a hacker can attempt to gain access to your personal information. While ‘living smart’ is convenient for many in day-to-day lives, that’s a lot of information compromised if a hacker even gets access to one connected device within our homes. As we continue forward, there is no doubt that the use of such devices will only increase in aims to improve efficiency, but as we do so, it is equally if not more critical to implement effective safety measures and standards to prevent security breaches. Thank you for this great post!
Excellent Job! Well, talking about IoT devices’ security is an endless topic. Due to the wide range of uses and the nature of implementation. The development and standardization of security best practices at different layers of those IoT devices are being implemented and enforced to balance between the effectiveness of use and the desired security level. But still, the cost of security and end-user awareness heavily impacted IoT implementations and made them easy doors to attack. Those devices faced multiple security challenges ranging from cheap hardware use, weak security standards, and algorithms, to a lack of proper end-user documentation or guidance about security specifications being implemented or setup best practices recommendations.
https://www.balbix.com/insights/addressing-iot-security-challenges/
Excellent Job! Well, talking about IoT devices’ security is an endless topic. Due to the wide range of uses and the nature of implementation. The development and standardization of security best practices at different layers of those IoT devices are being implemented and enforced to balance between the effectiveness of use and the desired security level. But still, the cost of security and end-user awareness heavily impacted IoT implementations and made them easy doors to attack. Those devices faced multiple security challenges ranging from cheap hardware use, weak security standards, and algorithms, to a lack of proper end-user documentation or guidance about security specifications being implemented or setup best practices recommendations.
https://www.balbix.com/insights/addressing-iot-security-challenges/
Great post Ukamaka, this got me thinking about whether the problem of security on these devices would ever be solved. It seems like the entire category is filled with devices that people don’t really care about. At this point we have devices ranging from Toasters to light bulbs, all connected to the internet. The way these things were designed, they are meant to be easy to setup so all they do is connect to the Wi-Fi network. My worry is that on one hand hackers can easily collect data from these devices to use for other more potent attacks; but for developers, is it really worth it for them to add security for a toaster? Lets say they do, will they really want to maintain it incase of a cipher being broken or a new attack being launched? It just seems that by the very nature of these IoT devices we are trading convenience for security and most people don’t care.