“Imagine walking into a dealership and seeing a sales team scramble with paper forms—it’s a surreal reminder of how much we rely on technology to keep the wheels turning.”
A Cybersecurity Crisis!
Car dealerships in North America experienced a devastating ransomware attack in June 2024, affecting the digital infrastructure they heavily rely on. The result? Dealerships were forced to return to pen-and-paper methods—something that hasn’t been seen in years. This incident highlights the growing need for stronger cybersecurity practices in the automotive industry as the reliance on technology continues to grow and the threat of cyberattacks becomes more prevalent.
What Happened? A Closer Look at the Attack on CDK Global
Cybercriminals targeted CDK Global in June 2024, the company providing essential software for automotive sales, finance, and repairs across North America. This was a ransomware attack, where the hackers encrypted CDK’s files, rendering them inaccessible until a ransom was paid. Dealerships across the nation were forced to juggle without access to their digital tools. I couldn’t help but visualize the chaos.
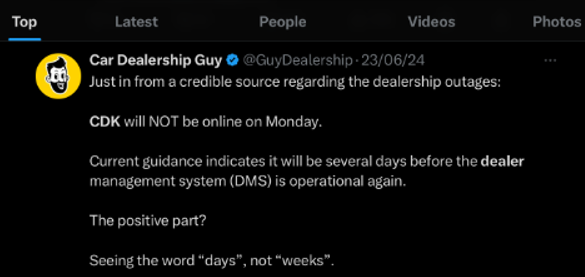
Who was behind the attack? The BlackSuit ransomware gang is responsible for the massive IT outage at CDK Global. Following the attack, CDK was forced to shut down its IT systems to contain the incident, resulting in widespread disruptions for dealerships that rely on their platform for essential operations, including sales and financing.
Picking Up the Pieces: How Dealerships Are Navigating Recovery
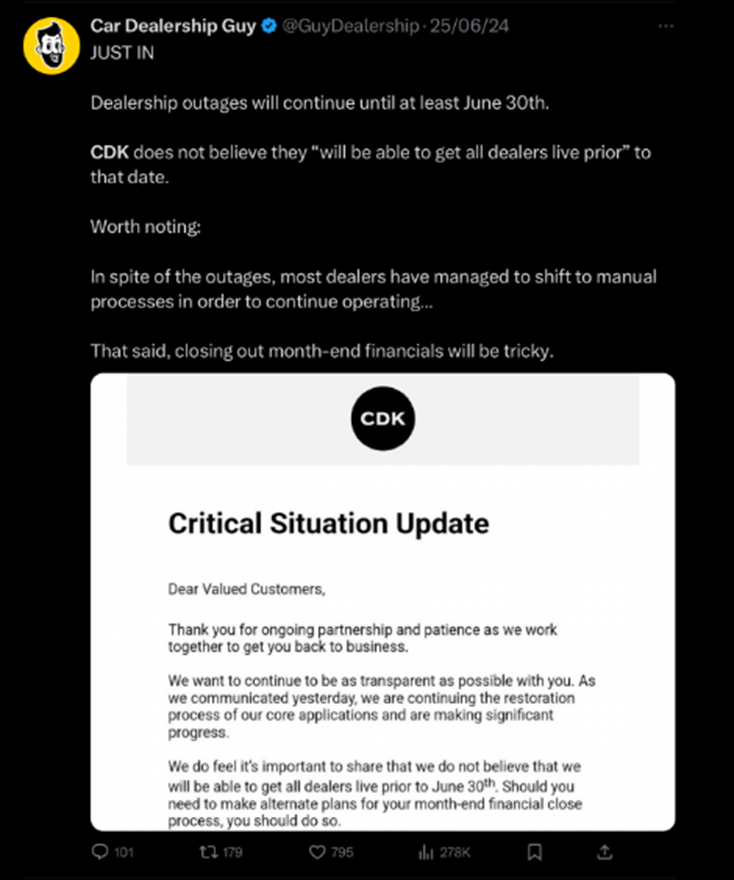
Although CDK Global did work to restore its systems, it took some time to fully recover. Dealerships had to reenter all the data that was manually processed during the outage digitally, resulting in a formidable backlog of work. Further delays and possible data conflicts could result from this. I can only imagine the frustration this caused for both staff and customers.
While many dealerships, including Stellantis, kept a careful eye on the situation, others, like Plaza Ford in Baltimore, were forced to close completely until things returned to normal. Customers experienced lengthier wait periods, postponed car delivery, and difficulties obtaining financing or servicing their demands as a result.
Improving Cybersecurity Posture
To better protect against future cyberattacks, dealerships should focus on implementing several key cybersecurity strategies. These include encrypting data to secure customer information, using intrusion detection systems to monitor unusual activity, and deploying endpoint protection to safeguard devices like computers and mobile systems. Having a well-tested incident response plan can help minimize damage when an attack occurs and adopting a Zero Trust model—where no one is trusted by default within the network—can further strengthen security. These measures collectively ensure a stronger defense against growing digital threats.
Next Steps: How We Can Do Better Together
This attack is a clear wake-up call about how fragile our digital systems can be. The main lesson to be learned from this is that cybersecurity cannot be neglected any longer. It needs to be a top concern in all sectors, including the automobile one. Dealerships and their clients will need to reconsider how they handle digital security as a whole because of this incident.
Here are some key takeaways to consider:
- For Dealerships: Conduct regular cybersecurity audits, invest in employee training, and develop a comprehensive incident response plan.
- For Consumers: Monitor personal data closely, use strong passwords, and report suspicious activity to protect yourselves against potential threats.
This attack raises bigger questions: If a single cyberattack can bring an industry to its knees, how prepared are other sectors? What steps can consumers take to protect their personal data during such events? Feel free to share your insights in the comments below—let’s keep the conversation going!
References
- Abrams, L. (2024, June 22). CDK Global outage caused by BlackSuit ransomware attack. Bleeping Computer. Retrieved from https://www.bleepingcomputer.com/news/security/cdk-global-outage-caused-by-blacksuit-ransomware-attack
- AutoSpies. (2024, June). Cyberattack: Digital heist hits auto industry car dealerships nationwide, left spinning their wheels. AutoSpies. Retrieved from https://www.autospies.com/news/CYBERATTACK-Digital-Heist-Hits-Auto-Industry-Car-Dealerships-Nationwide-Left-Spinning-Their-Wheels-121779
- CNN, KCCI, & Stringr. (2024, June 19). Car dealerships across U.S. and Canada under threat from cyberattack. News Center 1. Retrieved from https://www.newscenter1.tv/news/cyberattack-shuts-down-15000-car-dealership-computer-systems/article_c3eac8f8-2e7f-11ef-b49b-efa461df9da4.html
- Associated Press. (2024, June 24). Car dealerships in North America revert to pens and paper after cyberattacks on software provider. U.S. News & World Report. Retrieved from https://www.usnews.com/news/business/articles/2024-06-24/car-dealerships-in-north-america-revert-to-pens-and-paper-after-cyberattacks-on-software-provider



Eloquently written, Ankita! It’s interesting that CDK was able to restore their systems such that the only data that was missing was that that was collected manually during the downtime. That makes me think that CDK either: paid the ransom to gain access to their data, or had proactive, frequent backups such that they were able to rapidly rollback to a prior state. From what cursory reading I’ve done, it seems that while CDK hasn’t definitely said one way or the other, sources lean more on the former, which is disappointing, but nonetheless highlights the critical importance of not only having backups of important data, but making them regularly enough to avoid lost data, stored securely to ensure they are not affected by the attack, and are tested to ensure that the system can seamlessly roll back to a prior state without affecting end users.
Thank you for your insights, Kyle! You raise an excellent point about the importance of regular backups. The fact that CDK was able to restore most of their data suggests they had some contingency plans in place, but the speculation around paying the ransom is indeed concerning.
I completely agree with Kyle. Regular backups are essential, and storing them in a separate system helps prevent lateral movement during an attack. Testing backup systems is crucial to ensure a seamless rollback without impacting users. This incident highlights the importance of strong data protection strategies.
When all else fails, going back to basics is the answer! Sometimes, when you think about how they did during the old days, pen and paper can feel more secure in some situations because they aren’t susceptible to hacking or digital breaches. There’s no risk of ransomware or malware with physical records, and they can’t be accessed remotely. It’s also true that with the new technologies, when implemented with strong security practices, can be much more secure overall. With the right measures—like encryption, regular updates, and robust access controls—digital systems can protect sensitive information effectively. However, they require ongoing vigilance and resources to protect against cyber threats, especially from sophisticated groups that use advanced technologies to cause harm.
Thanks for your thoughtful comment, Maria! You’re right—going back to basics can sometimes feel like a safer option. While physical records eliminate the risk of digital breaches, the goal should be to enhance our digital systems with strong security practices.
Impressive work Ankita!! Your research offers a thorough and insightful examination of the ransomware attack against CDK Global and its significant ramifications for the automobile sector. I appreciate how you did a good job of highlighting the weaknesses in digital systems that are connected as well as the ripple effects that could occur from a cyberattack on a key service provider.
I appreciate your kind words, David! I’m glad you found the examination of the attack insightful. It’s crucial to recognize the vulnerabilities within interconnected digital systems. As we continue to rely on key service providers, understanding these ripple effects can help us advocate for better cybersecurity practices across the industry.
ChatGPT
Cyberstorm has hit the automotive sector once again with ransomware! Despite advancements in mitigation strategies like core isolation and XDR rules to detect and block unusual extensions, it’s puzzling how ransomware can still cripple organizations. While it’s great that they were prepared with backups and managed to recover data, the downtime still caused system unavailability, highlighting that even with safeguards in place, we need to continuously strengthen our defenses.
aaa
Great post, Ankita! Your insights on recovery strategies emphasize the importance of key metrics like RTO, RPO, and MTD. Manual data collection can introduce challenges like compatibility and redundancy. RTO should be shorter than MTD for effective recovery. A robust backup strategy, like the 3-2-1 rule, is crucial for mitigating attacks and ensuring business continuity. This rule involves keeping three copies of data (two locally, one off-site) for easy recovery from minor issues or major disasters.
Well written Ankita! I did some further reading to see if any personal data was compromised. It turns out that CDK Global disclosed that this cyberattack indeed compromised personal information from a vendor list. They took the important step of notifying the Maine Attorney General’s office, which shows their dedication to transparency (https://www.maine.gov/agviewer/content/ag/985235c7-cb95-4be2-8792-a1252b4f8318/ca6cd1a4-d5d7-4cde-8c02-673e38f3d8d3.html). Also, as Fahim mentioned, manual data collection can introduce challenges. So organizations should have a carefully prepared fallback plan to execute in such worst case scenarios.
Thanks for this. This is disheartening considering the level of sensitive data processed by these dealerships as well as the impact that would have on their customers. Additionally, the incident causing major disruptions and setbacks in providing the minimum service required to at least keep the business going indicates a weak or an absence of a proper business continuity management program. I definitely agree with the recommendation to enhance security awareness training programs because this situation most likely resulted from a successful phishing attempt or some other thing that required user interaction.