Recently, a team of researchers from Germany released a paper outlining the vulnerabilities of Resource Public Key Infrastructure (RPKI), the primary framework used to provide security for the Border Gateway Protocol (BGP) [2]. BGP is used for routing, and it is an alternative to Open Shortest Path First (OSPF). OSPF is generally used for routing within a smaller network controlled by one entity, or autonomous system (AS), while BGP is used for routing between these autonomous systems [1]. According to the researchers, 50% of the Internet’s resources use RPKI for securing BGP [4].
The researchers identified a number of vulnerabilities with the framework, ranging from misconfigurations by those that employ the framework to malicious actors finding ways to get around the security it is supposed to provide. This announcement coincides with the US government’s recent plan, announced in September 2024, to implement RPKI on all US ISPs and networks [2]. Before we get into the specifics, though, let’s take a closer look at what BGP and RPKI are, to help us better understand these vulnerabilities.
What is BGP?
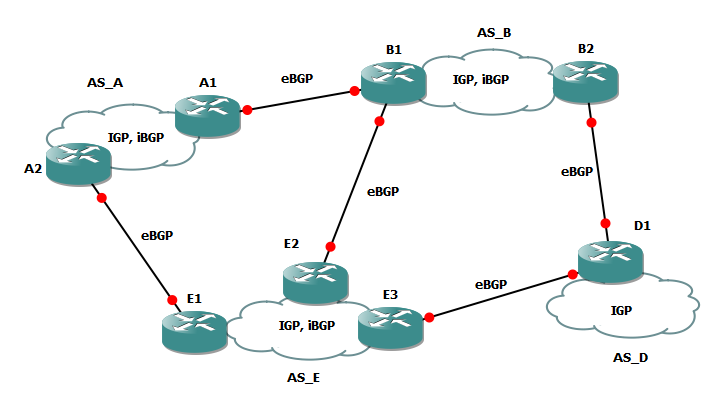
Source: https://upload.wikimedia.org/wikipedia/commons/5/5c/AS-BGP.png
As mentioned earlier, BGP is used for routing information across the internet between different autonomous systems. These can be Internet Service Providers (ISPs), universities, companies, or other organizations [6]. Since it is primarily used for routing between autonomous systems, it is classified as an External Gateway Protocol (EGP). However, it can also be used for routing within an autonomous system, so it is a very flexible protocol. Compared to purely intra-domain routing systems, though, BGP is more complex to configure but it allows for more control over routing. It’s also very scalable, as it can be used at the worldwide Internet level [1].
In order for an autonomous system to make use of BGP routing, network administrators will set up one of the routers to be a boundary router, or BGP peer. This router will send and receive routing information with its BGP peers through a TCP connection [6]. They exchange information on path attributes, such as hop count, monetary cost of routing, latency, and network congestion [5,6]. The boundary router will store this information in routing tables, building up a graph of all the autonomous systems around it. Even after the initial exchange of information, the BGP peers will continue to send information, including 19-byte keep-alive messages every 30 seconds [5]. The BGP router will update the routing table frequently with any new information it receives. Using this information, and the rules configured by the network administrator that give different weights to each path attribute, the BGP router will determine the best path [1,5].
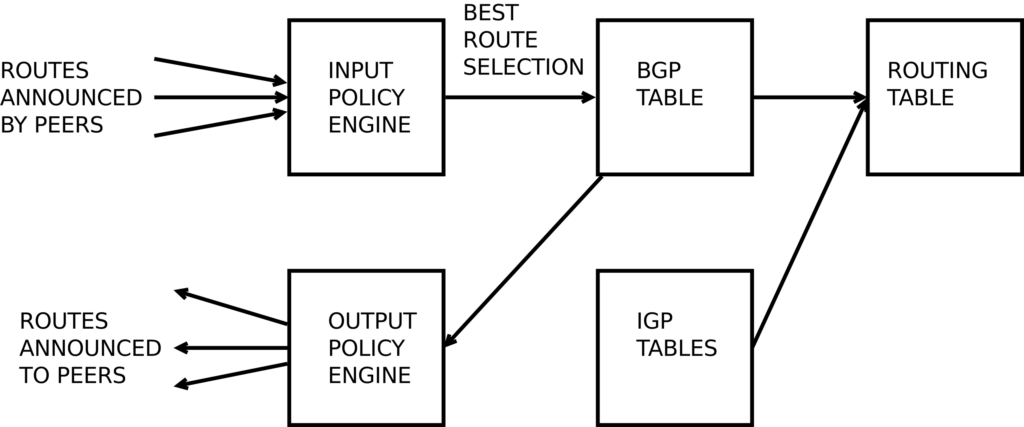
Source: https://upload.wikimedia.org/wikipedia/commons/thumb/3/39/BGP_process.svg/2560px-BGP_process.svg.png
BGP Vulnerabilities
Like with many aspects of the Internet, the original protocol was not designed with security in mind. It was initially assumed that all BGP peers were trustworthy and that they would not provide incorrect information [3].
The primary vulnerability BGP is susceptible to is BGP hijacking [6]. This involves an AS sending false routing information to its peers, either accidentally or with malicious intentions. This information is then propagated beyond the initial group of peers to the wider Internet, causing a variety of problems. Malicious parties can use BGP hijacking to redirect users to their fake sites, stealing credentials or money. In 2018, a malicious group stole $100000 in cryptocurrency from unsuspecting individuals after they were able to reroute traffic intended for Amazon’s DNS service [6]. Even accidental BGP hijacking can lead to a denial-of-service attack, such as in 2008 when a Pakistani ISP altered BGP routes to keep citizens from accessing YouTube. As with the malicious example, the false routes propagated beyond that Pakistani ISP AS, and it led to users around the world being denied access to YouTube [6]. Attackers can also alter routing to eavesdrop on communications or modify data in packets by putting themselves on-path [4,6].
Solution: Resource Public Key Infrastructure
The main solution for BGP hijacking is authentication. RPKI provides authentication through public key cryptography and certificates. The organization will sign Route Origin Authorization certificate or ROA with their private key, and this will be used certify that a particular organization has the authority to communicate routing information for the IP addresses within its AS [2,6]. Other BGP routers will access the ROAs from a RPKI repository, either directly or through intermediate software called a Relying Party, and they will use Route Origin Validation (ROV) to verify that any routing information is coming from the authorized organization [4]. This makes it much more difficult for malicious parties to hijack BGP routing [3,6].
Problems with RPKI
The biggest issue with RPKI is that it has to operate with lower security settings as it’s not currently adopted by all autonomous systems. As mentioned, 50% of internet resources use RPKI, but that still means a very large percentage of ISPs and other organizations don’t. RPKI was initially proposed in 2008, but it took many years before the importance of the framework was widely acknowledged and before viable solutions for organizations were available [4]. It took until 2021 for Google and Amazon to use ROV [4]. In general, the researchers identified that many organizations were reluctant to adopt this framework as they were uninformed on the benefits of it and leadership being reluctant to prioritize it over other initiatives [2,4].
So, to allow for the slow rollout of RPKI and to prevent any disruptions in routing Internet traffic, organizations configure RPKI to use fail-open mode. In this mode, routing information is still accepted from sources who either don’t have ROAs or whose ROAs failed validation [4]. However, these routes are given lower priority than routes that passed ROV. This means, even organizations that have adopted RPKI are still vulnerable to hijacking attacks.
As well, there a 40 RFCs for RPKI, which provide technical specifications and general guidelines for implementation [4]. Though these different specifications are meant to build on each other, they can still lead to confusion and inconsistency between how organizations implement RPKI.
Conclusion
Though RPKI does have some flaws, as the researchers point out, it’s the best framework available for securing BGP. It’s definitely an improvement on using BGP as is, which is vulnerable to phishing and denial-of-service attacks as it lacks any reliable authentication. Enforcing strict validation of ROAs is not fully possible right now, however, as RPKI is still not fully supported. The routing of traffic over the Internet should not be completely disrupted because of inconsistencies of RPKI adoption. There is hope that identifying some of the current issues with RPKI will encourage better regulations and guidelines for setting up RPKI going forward [2], and adding on other security solutions, such as alerts when unknown parties are broadcasting routing information about your organization, can help further secure routing [6].
References
[1] “BGP vs OSPF: Differences & Tutorials.” Accessed: Oct. 18, 2024. [Online]. Available: https://www.catchpoint.com/dynamic-routing-protocols/bgp-vs-ospf
[2] “Fix for BGP routing insecurity ‘plagued by software vulnerabilities’ of its own, researchers find | Network World.” Accessed: Oct. 18, 2024. [Online]. Available: https://www.networkworld.com/article/3544447/fix-for-bgp-routing-insecurity-plagued-by-software-vulnerabilities-of-its-own-researchers-find.html
[3] RIPE NCC, How Does RPKI Help with Routing Security?, (Oct. 19, 2023). Accessed: Oct. 18, 2024. [Online Video]. Available: https://www.youtube.com/watch?v=RI6GUwquB74
[4] H. Schulmann, N. Vogel, and M. Waidner, “RPKI: Not Perfect But Good Enough,” Sep. 22, 2024, arXiv: arXiv:2409.14518. Accessed: Oct. 18, 2024. [Online]. Available: http://arxiv.org/abs/2409.14518
[5] “What is BGP? – BGP Routing Explained – AWS,” Amazon Web Services, Inc. Accessed: Oct. 18, 2024. [Online]. Available: https://aws.amazon.com/what-is/border-gateway-protocol/
[6] “What is BGP? | BGP routing explained.” Accessed: Oct. 18, 2024. [Online]. Available: https://www.cloudflare.com/learning/security/glossary/what-is-bgp/
Images:

Great post, Nicole! The slow adoption of RPKI sounds eerily similar to the languishing support of DNSSEC, as both these security measures employ digital signatures to thwart spoofing, whether that be BGP hijacking or DNS spoofing. With the latter case, clients have the ability to force-enable DNSSEC, such as within their web browsers; do end-users, or even ISPs, have any ability to mandate the use of RPKI across the entire connection, or is the state of adoption such that fail-open mode is still necessary for routing across the Internet?
The study reveals key vulnerabilities in RPKI, including partial adoption and potential hijacking risks. While it improves BGP security, gaps in implementation still expose networks to threats.
Nicely articulated, Nicole.
BGP is a widely used protocol in the internet world based on a trust model that lures attackers to redirect traffic towards them or launch a DoS attack. I was amazed to learn that Google and Amazon took such a long time for route origin validation. I recently found a similar incident from Malaysia, where Cloudflare DNS was the victim and the attack was unintentional.
https://pulse.internetsociety.org/blog/dns-hijacking-in-malaysia-a-step-back-for-internet-freedom
Insightful post, Nicole! It raises a crucial point of the challenge of implementing complex protocols like BGP securely. BGP’s many configuration options make it vulnerable to mistakes that attackers can utilize. Additionally, large, complex systems may experience slow convergence with BGP. While RPKI, a security extension, holds promise, its limited adoption might create initial validation hurdles. This real-world case highlights the possibility of RPKI to address BGP’s security concerns. With proper guidelines and standards, RPKI can become a more widely used security layer for BGP, ultimately enhancing internet security.
It highlights serious vulnerabilities in RPKI, which secures BGP, crucial for internet routing. With 50% of resources relying on RPKI, misconfigurations and attacks like BGP hijacking remain significant concerns. Although RPKI improves authentication, its limited adoption and fail-open mode leave many organizations exposed. As the U.S. government advocates for broader RPKI implementation, addressing these challenges is vital for a more secure internet.
Hi Nicole, great post. I learnt a lot about the RPKI and BGP. The part that interests me the most is when you talked about BGP hijacking. This is yet another case of how infrastructure being built without security in mind. The idea that all BGP peers would be trustworthy is the opposite of a Zero trust approach. A lot of our infrastructure works this way and it feels like we just keep discovering this. The biggest issue is that it would take a lot of resources to rebuild all of this and no one want to do it. The solutions we keep using is adding security on top. I just feel like this doesn’t address the core issue and there might be more vulnerabilities discovered in the future.