
Vulnerabilities in E2EE Cloud Storage

During ACM CCS 2024, held October 14-18, 2024, researchers from ETH Zurich, Jonas Hofmann and Kien Tuong Truong, indicated severe security flaws in the end-to-end encryption (E2EE) systems of several cloud storage service providers. These flaws can pose a significant threat to user information and undermine the promised security standards of those providers.
The research studied five cloud storage service providers: Sync, pCloud, Icedrive, Seafile, and Tresorit, with over 22 million users. The academics investigated these cloud service companies and found them vulnerable to various types of attacks, including unauthorized access to key material, protocol downgrades, and data tampering. However, some of the companies have acknowledged the issue and are considering addressing it, while others, such as Icedrive, have publicly stated their intention not to fix the vulnerabilities. This raises concerns for E2EE cloud storage users regarding the use of cloud storage services with proper data privacy and security.
End-to-end encryption (E2EE)
In E2EE only the sender and receiver can read or modify the content as they have the only relevant keys, and it uses private communication using Public key encryption based on two keys instead of one: a public key and a private key. E2EE is a type of messaging that keeps messages private from everyone, including the messaging service (cloud service provider). When E2EE is used the message only exists in decrypted form for the sender and receiver. It’s like a letter goes over the mail in a sealed envelope.
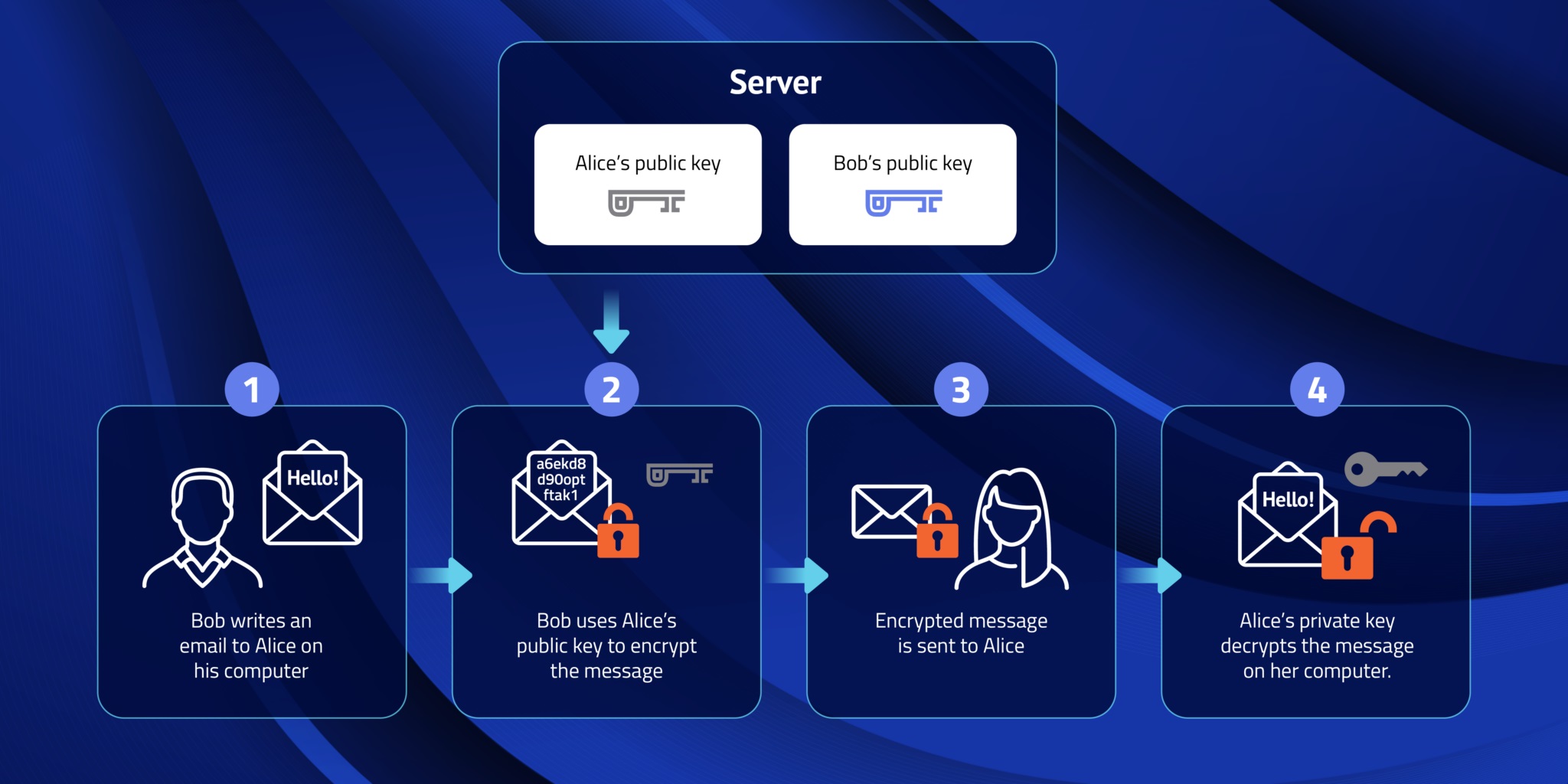
Image: E2EE Scenario showing encrypted movement between sender and receiver
Description of the protocol and key hierarchy used by those five providers
Considering protocols due to the dependence on a user-chosen password ρ (generally dissimilar from the one used to validate for the server) -derived key material, the security of the systems researcher’s analysis is highly dependent on the strength of the user’s password. A malicious provider can always attempt an offline brute-force attack or a dictionary attack to recover a password, which is a fundamental limitation of password-based encryption. Good password policies along with multifactor authentication and the usage of a memory-hard password hashing function help to mitigate this risk.
The Key hierarchies for those providers are summarized in the following figure:
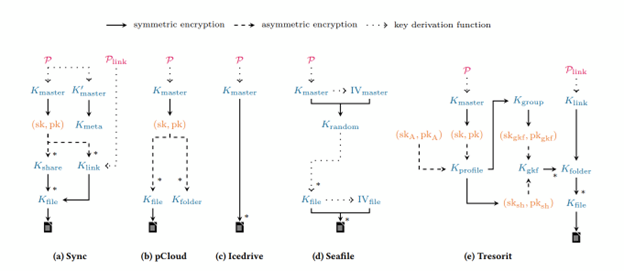
Figure 1: Key hierarchies of all providers researched. Symbols shown ∗ indicate a one-to-many relationship. All the key material that is not obtained from something else is indirectly generated using relevant suitable key generation functions.
Combination of attacks to test Confidentiality, Integrity and Availability (CIA)
The researchers tested 10 possible attacks against E2EE cloud storage services; all these activities would require the attacker to have already gained control of a server with the ability to read, modify and inject data. The researchers mentioned that they study this to be a convincing threat model for E2EE services, as these service industries are meant to protect files even if such a compromise has happened.
These attacks were categorized into ten broad categories, which can compromise confidentiality, damage file data and metadata, and enable the injection of unauthorized files and directory manipulation.
The researchers identified the following vulnerabilities:
- Unauthenticated key material (Sync and pCloud)
- Unauthenticated public keys (Sync and Tresorit)
- Protocol downgrade (Seafile),
- Link-sharing leakage (Sync)
- Use of unauthenticated encryption (Icedrive and Seafile)
- Unauthenticated chunking of contents (Icedrive , Seafile and pCloud)
- Tampering with content and details of files (Sync, pCloud, Seafile, and Icedrive)
- Tampering with file metadata (all five providers)
- Injection of folders (Sync, pCloud and Seafile)
- Injection of malicious files into a user’s storage (pCloud)
In the following table the research findings are given:
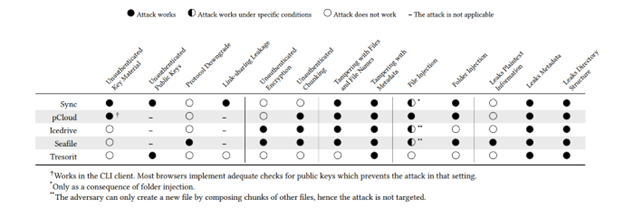
Table 1: Summary of the providers examined with the attacks and leakages that affect them.
Conclusion
This analysis could lead to the development of stronger and more secure key hierarchy models and protocols. It also highlights the need for a more comprehensive threat model specifically designed for E2EE cloud storage systems. The researchers highlighted that the identified flaws are not isolated incidents but rather indicative of a widespread problem within the E2EE cloud storage market. They asked for further analysis of deployed E2EE cloud storage systems to better understand and address existing challenges. Additionally, they promoted the development of a standardized protocol for secure E2EE cloud storage.
The study revealed that these vulnerabilities originate from common cryptographic design flaws, affecting multiple providers in similar ways. This underscores the broader systemic issues within the development of E2EE cloud storage solutions.
“However, our research demonstrates that the practical reality is quite different, and that the ecosystem is fundamentally flawed. Our findings strongly suggest that, in its current state, the ecosystem of E2EE cloud storage is largely broken and requires significant reevaluation of its foundations. ” Hofmann and Tuong Truong advised.
References
[1] https://brokencloudstorage.info/paper.pdf
[2] https://brokencloudstorage.info/
[4] https://www.cyberkendra.com/2024/10/flaws-in-e2ee-cloud-storage-system.html#google_vignette
Image Link https://www.preveil.com/wp-content/uploads/2024/08/EndToEndEncryp_Aug24-2048×1024.png
Figure 1, Link: https://brokencloudstorage.info/paper.pdf
Table 1, Link: https://brokencloudstorage.info/paper.pdf

Hi Fahim, I found your discussion post incredibly engaging and thoroughly enjoyed reading it from start to finish. By showcasing the findings conducted by Zurich ETH researchers, I could understand just how severe the vulnerabilities within E2EE systems were. Additionally, by mentioning the security flaws that the researchers found, I was able to understand what level of protection standards for data privacy were challenged within the E2EE systems. Furthermore, the post drew light on the existence of industry-wide cryptographic issues. Due to systematic flaws in some established crypto designs of multiple providers, protocols must be revamped so that cloud storage services have a critical hierarchy model rather than previous weaker iterations. Lastly, the varying responses from cloud providers force a need for evaluation as some issues require immediate solutions that, even though they are acknowledged, are not fixed. The post indicates a necessity for provider accountability so that users can trust their data is secure.
Good insight!
The cloud providers’ response is remarkable, given the urgent need to address vulnerabilities to safeguard data privacy and security. As cybersecurity threats continue to grow, organizations must adopt a proactive approach to identify risks and promptly defend data, however, the cloud providers must ensure accountability to maintain users’ confidence in the security of their data. End-to-end encryption is just one layer of security. To enhance security, it is recommended to use best practices like two-factor authentication, regular software updates, and a strong password.
Woww! Thank you Fahim! I just love the insights provided in your post.
No application or product has really figured a lifelong security solution. Thanks to experts and researchers that keep reminding us of the work we need to do to continually improve ALL security related products and services .
And to think that icedrive has no intention of fixing their vulnerabilities….what could be the motive behind that decision ?
Great insight !
It is surprising to see that even well-known cloud storage providers have such critical vulnerabilities in their E2EE systems. I always thought E2EE meant my data was very secure, but this research highlights how important it is to examine the underlying protocols. The fact that some companies are not willing to address these security flaws is quite worrying. If Icedrive isn’t fixing their unauthenticated encryption issue, how can users trust that their data is secure?
That’s an excellent post, Fahim! This study strongly reminds us that while E2EE promises high security, real-world implementations can sometimes fall short. It’s concerning that a fundamental concept like E2EE still leaves room for potential attacks on confidentiality and integrity. Knowing that providers could face dictionary or brute-force attacks due to weak password policies makes it clear that user education on secure passwords is more important than ever.
Nice work Fahim! for bringing this up, this is interesting considering many of these cloud storage providers boast of impeccable security and hold millions of terabytes of personal user data for money. I am more shocked to find that “Protocol downgrade (Seafile), Link-sharing leakage (Sync)” as you stated are vulnerabilities found, which is pretty much the sole purpose of using such cloud storage services. Users now need to be aware of such findings and need to be up to date aware of such issues before they start using such services.