This article highlighted how researchers explore the security vulnerability in the Nexus Android botnet’s command and control (C&C) panel. This security researcher exploited the vulnerability of C&C panel by compromising the panel to gain valuable threat intelligence. The article also highlighted the model of mobile Appinjects, which is use to gain the knowledge of overlay attacks executed on compromised Android devices to hijack user accounts and steal credentials.
The increase in the exponential rate and sophisticated threat of android botnet is something that gave the security researcher hard time to crack. Android botnets are major threat to the security and privacy of millions of users worldwide. The special characteristics of mobile devices, such constant connectivity, the comprehensive personal data they contain and the high computing power make android botnets a devastating weapon for cybercriminals. The capability to infect significant number of devices seriously increases cybercriminals’ malicious activities and poses significant challenges to cybersecurity professionals and organizations.
Mobile operating system is widely used and Android has become a prime target for cybercriminals who seek to assemble networks of compromised devices, known as botnets which is used to carry out a very large of cyber-attacks. These malicious networks can be used for various purposes, including distributed denial of service(DDoS attacks),spam, data theft, cryptocurrency mining.
This articles proves that no matter strong security systems are built around an application or operating system it is vulnerable at some point and can exploited.
The Nexus Android C&C panel was was built with sophisticated security system was exploited to gather internal details of the C&C design. After successful compromise, the researcher focus on Appinjects and on how exactly payloads are injected into legitimate applications on compromised Android devices.
The exploitation of Nexus Android was done by using an SQL injection vulnerability model on Nexus C&C panel however Successful exploitation of security vulnerabilities in malicious software plays a crucial role in understanding the design of botnets and their inherent capabilities. This further helps security researchers to generate threat intelligence to help combat similar attacks. This is why security researchers prefer to target centralized C&C panels deployed by malware operators to manage and operate compromised systems at a large scale. If the C&C panel is compromised, security researchers can dissect the complete architecture of deployed botnets in the wild. Let’s analyse a security vulnerability in the Nexus Android botnet C&C panel that has successfully been exploited to gain access to the panel.
First the security researcher look at the Nexus Android botnet C&C panel. Diagram below shows the landing page of the Android botnet.
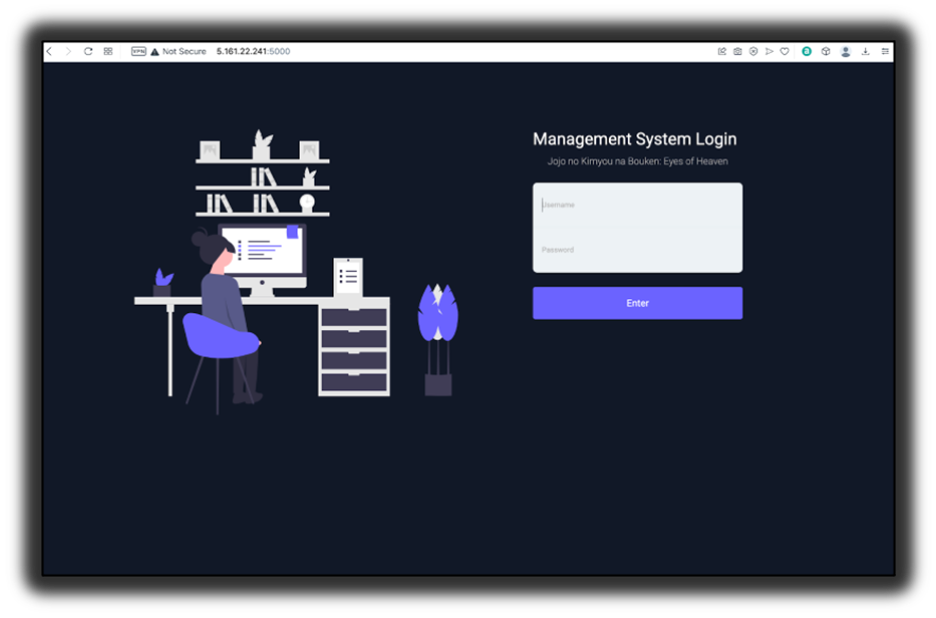
Figure 1: Landing page of the Nexus Android botnet C&C panel.
On further enumeration and resource fuzzing, it was discovered that the /api resource was available. When an HTTP GET request was initiated it resulted in “fail”, as the request did not have authentication credentials, and the API endpoint failed to validate. However, during this analysis the URL structure of the API endpoint was confirmed.
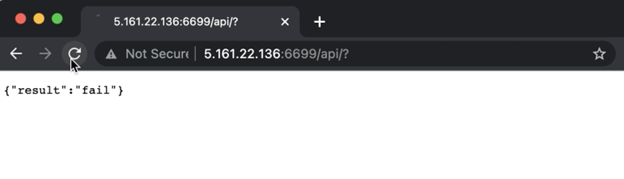
Figure 2: The HTTP GET request resulted in “fail”.
Specific versions of the Nexus Android botnet C&C panel are vulnerable to SQL injection vulnerability. The API endpoint used by the C&C panel for communication with the compromised Android devices allows remote attackers to inject payloads to directly access the backend SQL interface and extract credentials on the fly. The vulnerability exists in the “value” HTTP GET parameter. The potential vulnerable URL is presented below:
http://<nexus android c&c host>/api/?param=sms&value=1<injected payload] &botid=f991a83c2a9f25c8de68ad597e98a91b&method=bots.update&access=1
Penetration testing and security research should be considered when building a system, as it helps tidy security because if an attacker has the first knowledge of a system vulnerability, the effect on the organization or nation is costly, and that is why it is important to find security vulnerabilities in the C&C panels of botnets to obtain access and gain intelligence to help combat botnet infections. C&C panel compromise allows threat analysts and researchers to:
- Restrict the infections by jamming the communication between the infected systems and the C&C panel.
- Generate threat intelligence by analysing the inherent functionalities supported by the bot.
- Analyse the exfiltrated data from the compromised hosts to determine the potential security breaches.
- Assess the impact of the active botnet on organizations and enterprises.
- Design signatures, heuristics and ML/AI algorithms to detect and prevent infections as a proactive measure.
Figure 3 presents the SQL injection tests launched to determine the vulnerable parameter. It highlights that the “value” parameter is successfully injected with the “MySQL >= 5.0.12 AND time-based blind (query SLEEP)” payload.
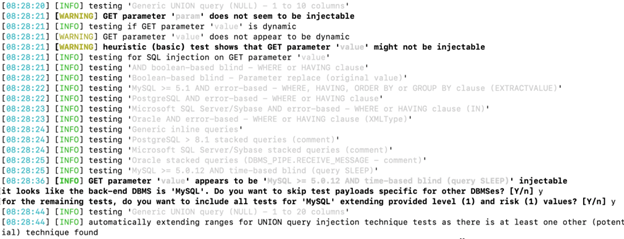
- Figure 3: Detected vulnerable and injectable parameter.
After identifying the vulnerable parameter, attacker use it to inject more malicious code. The type of SQL injection they use is called “time-based,” which is a sneaky method where the attacker can’t directly see the results of their attack. Instead, they send a command that makes the database pause for a moment if the injection works. By timing these pauses, the hacker can figure out if they are on the right track.To get the information they want, the attacker uses a clever trick. They set up a system that guesses one letter or number at a time. If the guess is right, the database pauses, and the attacker knows they have got it correct. They keep doing this, letter by letter, until they have pieced together whole strings of data from the database. It’s like a high-tech game of 20 questions, where each correct guess reveals a bit more of the hidden information.
In Figure 4, you can see that the database name is ‘nexus’ and the table name is ‘users’. The response time is adjusted to obtain the string, which is the password. The blind time-based SQL injection technique is also useful in executing payloads successfully even if the database has load or performance issues.
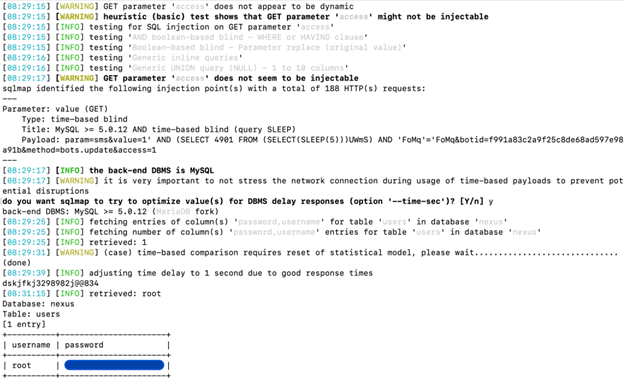
- Figure 4: Successful SQL injection results in leakage of credentials.
After obtaining the username and password, it was possible to successfully access the C&C panel, as shown in Figure 5.
Figure 5
This research underlines the importance of penetration testing and vulnerability exploitation in generating threat intelligence to combat adversaries in a proactive manner.
Mobile AppInjects: overlay attacks
The Nexus Android bot executes overlay attacks on compromised devices. Overlay attacks are carried out on compromised Android devices by abusing the User Interface (UI) and inherent APIs supported by the Android OS. Imagine a sneaky hacker creating a fake “mask” for your favorite app. This mask looks just like the real app, but it is actually a trap. When you open what you think is your banking app, for example, this fake mask slides over the top, and you can’t even tell it is there.
Now, when you type in your username and password, thinking you’re logging into your bank, you’re actually typing into the hacker’s fake screen. It is like someone put a thin, see-through sheet over your phone that copies everything you type.
This trick is not just for stealing passwords. The hacker might make a fake screen that looks like a credit card payment page or a form asking for your personal info. Whatever you enter, the hacker can see and steal.
It is a bit like if someone put a fake ATM front on a real ATM. You think you’re using the bank’s machine, but there is an extra layer tricking you and stealing your info.
This sneaky method is called an overlay attack, and it’s particularly dangerous because it is so hard to spot. You think you are using the app you trust, but you’re actually handing your sensitive information directly to the bad guys.
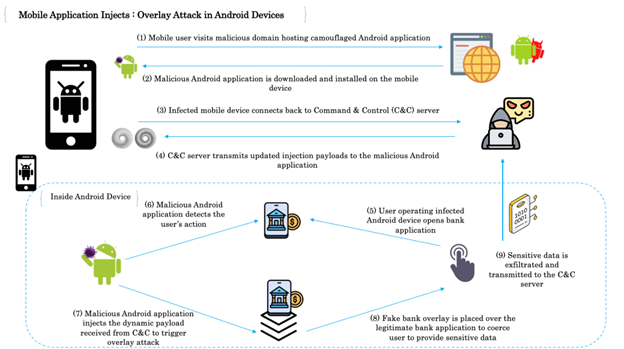
Figure 6: Overlay attack in Android devices.
Let’s discuss the overlay attack model in detail.
- Step 1: The attacker lures the mobile user into visiting a malicious domain hosting a camouflage Android application by using attacks such as drive-by downloads, phishing, etc. The attacker convinces the user to install a seemingly legitimate application from a malicious domain as the hosted applications often promise useful functionalities, such as free games, utilities, or productivity tools.
- Step 2: The camouflage application is successfully downloaded onto the Android device and, once installed, requests certain permissions, including the ‘Draw over other apps’ permission to obtain overlay functionality. This permission allows the application to draw elements on top of other running applications.
- Step 3: The camouflage application (bot) connects back to the C&C server, sending messages to confirm that the attack is successful and the device has been compromised.
- Step 4: The C&C server responds with required commands to the camouflage application to ensure the Android device has now become part of the botnet.
- Step 5: The camouflage application constantly monitors the foreground applications running on the device, waiting for specific target applications – such as banking apps, social media apps, or email clients – to launch. When the user interacts with any banking application, the camouflage application becomes active.
- Step 6: On detecting the user’s action, the camouflage application triggers the inherent logic to start the injection engine to initiate the attack.
- Step 7: When a targeted application, such as a banking application, is launched, the camouflage application swiftly displays a deceptive overlay (AppInject code) on top of the legitimate application. The overlay usually mimics the legitimate application’s login screen or other crucial sections, making it difficult for the user to notice the deception.
- Step 8: Once the AppInject code is successfully injected, the user believes they are interacting with the legitimate application and enters their login credentials or sensitive information into the deceptive overlay. The camouflage application captures this information.
- Step 9: The camouflage application transmits the harvested credentials from the compromised mobile device to the C&C server. With the harvested credentials, the attacker can gain unauthorized access to the user’s accounts, exposing them to potential financial loss, identity theft, or privacy breaches.
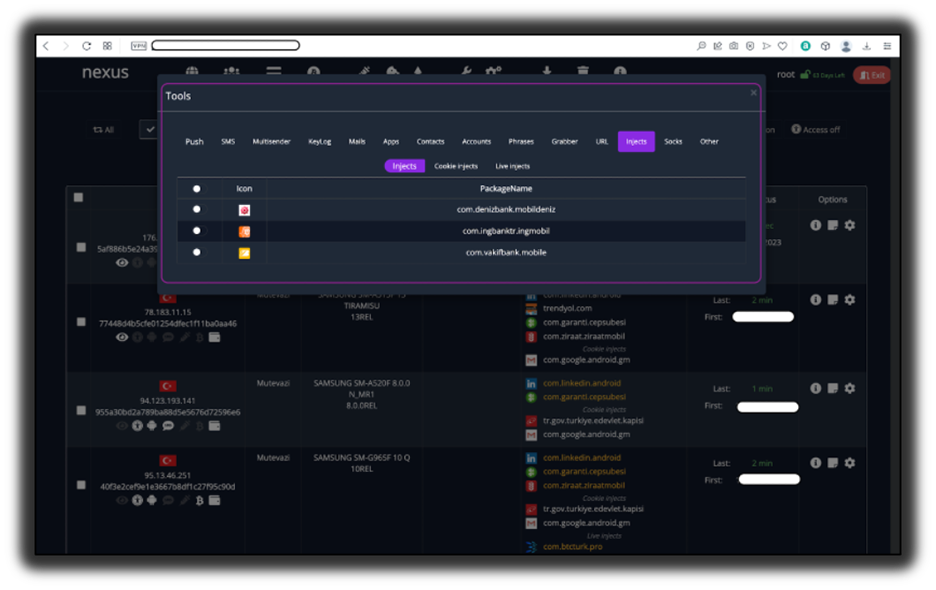
As discussed in the last section, once the Nexus C&C panel was successfully compromised, the security reseacher were able to analyse the mobile AppInjects. It was discovered that the Nexus C&C panel provides a well-structured AppInject code that can simply be added to the Nexus bot during the build process and the AppInjects were used to trigger overlay attacks. Figure 7 shows the AppInject functionality in the Nexus Android botnet C&C panel.
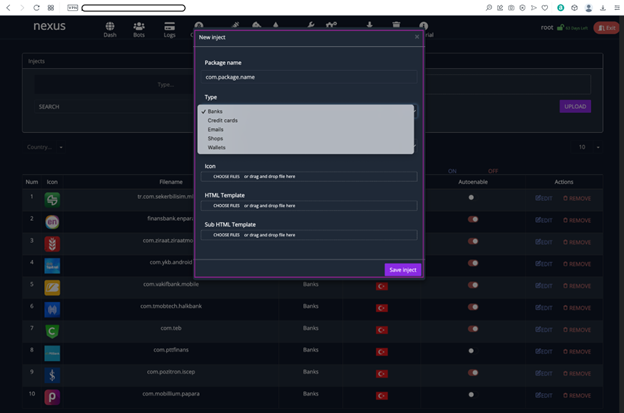
Figure 7: AppInject functionality in the C&C panel.
The C&C panel is equipped to automatically insert the AppInject code in the camouflage application during the build generation. The process is completely automated as the attacker can simply specify the options and select the AppInject payload to be added. On further analysis, we discovered that the Nexus Android C&C panel stores AppInjects for a variety of banks. Figure 8 shows the AppInject payload for Wells Fargo bank.
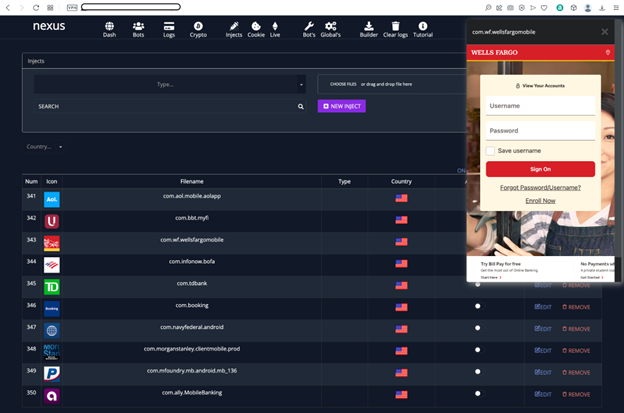
Figure 8: Wells Fargo AppInject code in the Nexus Android C&C panel.
The AppInject code for Morgan Stanley and American Express banking applications are also shown in the Appendix. This reflects that attackers opt for automation to ease the process of generating camouflage applications with AppInject code embedded directly into them.
A number of recommendations and best practices are discussed below to stay proactive against mobile attacks and fraud:
- Always download applications from official application stores like Google Play Store, where apps undergo a vetting process to minimize the risk of malicious code. Avoid installing apps from third-party sources unless you fully trust the source.
- Enable two-factor authentication whenever possible to add an extra layer of security to your accounts.
- Consider using reputable mobile security software that can detect and block overlay attacks and other threats.
- Regularly update your Android device and applications to ensure you have the latest security patches.
- Android devices have a ‘Verify Apps’ feature that scans apps for potential threats. Make sure it is enabled in the device settings.
- Pay attention to the permissions requested by an app during installation. Avoid granting unnecessary or suspicious permissions.
- Always review the permissions an application requests during installation. Be cautious of applications that request excessive permissions unrelated to their functionalities.
Conclusion
Threat intelligence plays a pivotal role in the fight against Android botnets. In this article, we have shown how penetration testing and vulnerability assessment provide vital tactics in compromising the Nexus Android botnet C&C panel to generate threat intelligence. These botnets present significant challenges to the security of Android devices, as well as posing risks to user privacy and the integrity of mobile ecosystems.
Organizations must invest in advanced threat intelligence tools, hone their incident response capabilities, and continuously educate their workforce to recognize and report potential threats effectively. Embracing an intelligence-driven approach to cybersecurity will be crucial for staying resilient against these threats.
To effectively combat the ever-evolving threat landscape posed by Android botnets, collaboration among various stakeholders is essential. Organizations, security vendors, researchers, and law enforcement agencies must work together to share threat intelligence and coordinate efforts to dismantle botnet infrastructures.
References:
[1] Cleafy. Nexus, A New Android Botnet? 21 March 2023. https://www.cleafy.com/cleafy-labs/nexus-a-new-android-botnet.
[2] Rashid, H. New Android Botnet Nexus Being Rented Out on Russian Hacker Forum. Hack Read. 23 March 2023. https://www.hackread.com/android-botnet-nexus-sold-russian-hacker-forum/.
[3] Sood. A.K.; Enbody, R.J. Crimeware-as-a-service – A survey of commoditized crimeware in the underground market. International Journal of Critical Infrastructure Protection. Volume 6, Issue 1, March 2013, Pages 28-38. https://www.sciencedirect.com/science/article/abs/pii/S1874548213000036.
[4] Owasp. Blind SQL Injection. https://owasp.org/www-community/attacks/Blind_SQL_Injection.

Great Job, George! This is a glaring vulnerability that occurs at many stages along the DevOps process as a result of developers mistakenly creating insecure code. Developers have access to a variety of beneficial automation tools, but when used improperly, these technologies might introduce significant security issues. Practicing top security practices will protect a company’s brand and ensure regulatory compliance.
Excellent reading ! The in-depth walkthrough of the SQL injection technique used to compromise the Nexus botnet’s C&C panel is remarkable. It’s apparent that even sophisticated systems can be vulnerable. The recommendations offered—especially the emphasis on two-factor authentication and using trusted app sources. These small steps can make a massive alteration in protecting user data.
Great post George! It’s fascinating how compromising a botnet’s C&C panel can reveal so much about its structure and potential attacks! It’s like getting a behind-the-scenes look at how these threats operate. Leveraging these insights to build better threat intelligence is a game changer for defending against Android botnets. Seeing SQL injection vulnerabilities exploited here is a reminder that no matter how secure a system seems, vulnerabilities can always exist.
Wow, overlay attacks sound super sneaky! It’s wild how hackers can create fake UIs that look just like real apps. Definitely makes me more cautious about what I enter on my phone.
Great post, George! It’s interesting to see a vulnerability being a good thing. Getting a chance to understand a common application that is used for launching botnet attacks is a big step forward to building operating systems and applications that are able to defend against that sort of attack. The overlay attack is also really interesting! It’s definitely important to be wary of what apps you download and the permissions you enable for those apps. This website also gave me some extra information on this type of attack: https://www.appsealing.com/overlay-attacks/