What is Privileged Access Management (PAM)?
Privileged Access Management (PAM) is a package of cybersecurity strategies and access management tools utilized for controlling, monitoring, and safeguarding users with privileged access permissions.[3] A PAM system ensures your computers have a secured network that is able to decrease operational complexity and protects important resources such as data, user accounts, networks, devices, systems, and processes.[3] PAM manages shared accounts, super users, teams, and service accounts.[3]
How does PAM work?
In most large companies with multiple levels of positions, users will need permissions and access requests to privileged accounts in order to effectively complete their day-to-day tasks. [3] The same users will need to provide justification to the server when requesting access. This is where PAM comes in to provide a secure means of communication while maintaining a well-balanced workflow.[3] PAM simplifies the process of approving or denying user access requests and logs all decisions.[3] Once approval is granted to the user, PAM temporarily provides the user higher access without manually requesting and remembering credentials for the privileged access.[3] Single Sign-On (SSO) integration which centralizes access to multiple user accounts while not compromising the integrity of passwords and Credential Management where the timespan of a password remaining valid is condensed are two examples of PAM tools.[3]
Passwords, TLS certificates, and Accounts within a company are all typically secured with PAM solutions.[1] However, SSH key management is hardly discussed in this realm, simply due to the lack of technology available to implement it adequately.[1]
Why can’t PAMs handle SSH Keys?
SSH Keys are access credentials in the Secure Shell (SSH) Protocol that are like passwords but function differently when compared to passwords.[1] Keys tend to further outnumber passwords by a 10:1 ratio.[1] While only some passwords are privileged, almost all SSH keys open doors to something valuable.[1] One key also has the capability to open doors to multiple servers.[1] Implementing PAM to handle SSH keys would solve these problems. However, PAMs unfortunately don’t manage SSH keys very well. Since PAMs were built to vault passwords, doing the same with keys simply does not work as keys must be secured at the server’s side.[1] Otherwise, keeping keys under control becomes extremely difficult. Moreover, to manage these keys, our solution must first discover the keys which PAMs cannot do.[1]
ISSUE: Despite these concerns, PAMs are not complete without SSH key management. Even if an organization manages 100% of your passwords, the chances are that 80% of your critical credentials are still missing if SSH keys are not managed.[1]
What solution has been proposed to solve this issue?
Modern ephemeral access (MEA)! [1,2] With MEA, secrets needed to access a target are granted when needed and automatically expire once the authentication is done leaving a passwordless and keyless method to manage access. Passwords have been the weakest factor within cybersecurity and are the easiest to crack, forget, and lose making it a targettable source. [4,5] SSH says ‘the best way to manage passwords and keys is to not manage them at all’.[1,2]
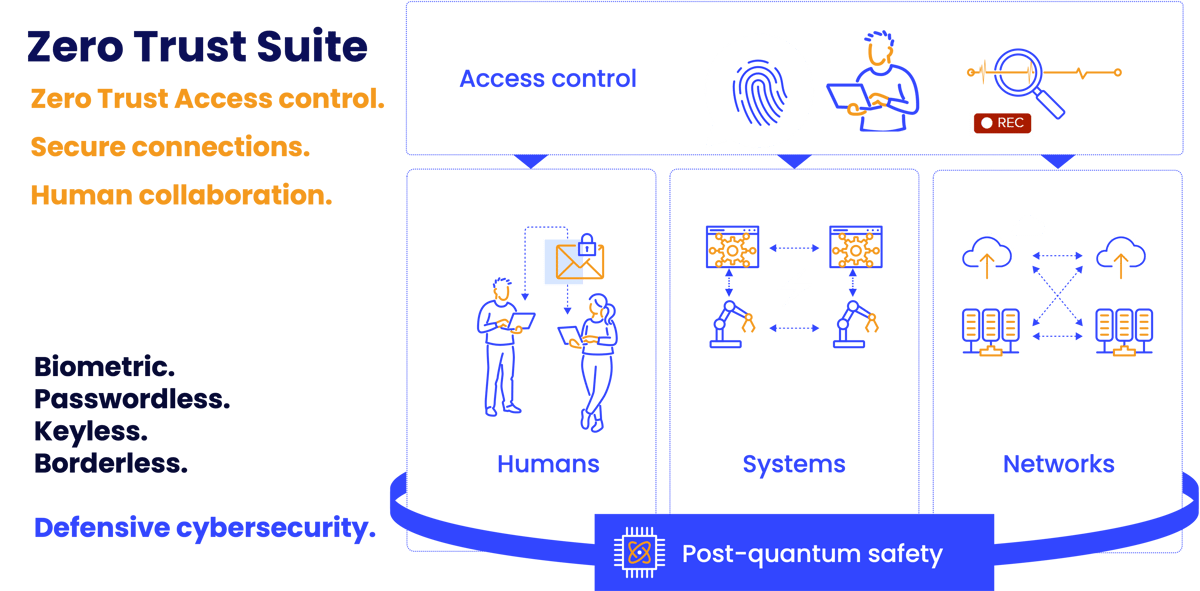
Figure 1: Zero Trust Suite Access Control system displaying the safety network mechanism. [2]
SSH Zero Trust Suite is a modular software suite that allows companies to communicate securely. [1,2] This suite secures communications up to a quantum-safe level in instances such as when:
- (1) Humans share sensitive data with each other,
- (2) Machines, systems, or data centers need to connect and
- (3) Experts need to access critical targets for updates maintenance, configuration, and production environment uploads.[1,2]
Using techniques such as rotating passwords often, hiding shared account passwords, eliminating risky keys, and providing ‘just enough access’, this Zero Trust Access method significantly increases security and reduces the potential to be attacked. [1,2]
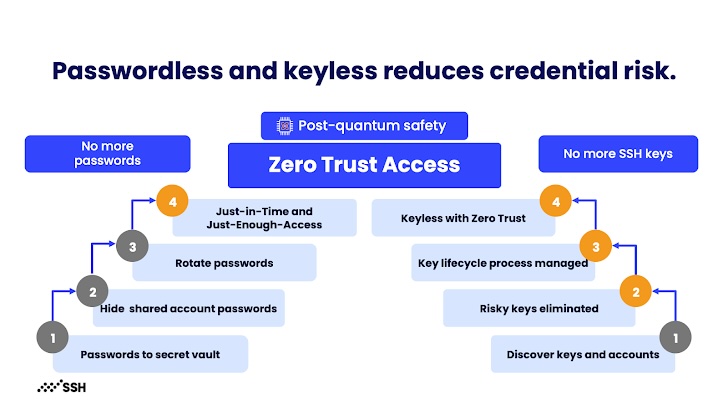
Figure 2: Ways in which Zero Trust Suite reduces credential risk upon eliminating passwords and keys. [1]
Has this already been implemented and tested by customers?
Yes! Zero Trust suite has been put to use with various companies. For example, Zero Trust Suite has provided tracking of user identities and a transport view into the sessions securing the VPN tunnel from unsanctioned use.[2] Likewise, a global semiconductor company fixed a security audit failure by using passwordless authentication for secure remote user access.[2] Initially, risk assessment and scanning were done using SSHerlock tools which reported access credential violations.[2] As such, the keys-violating global SSH policy was removed and replaced with keyless authentication instead of fixing the security failure.[2]
Conclusion
Privileged Access Management or PAM plays a crucial role in securing a company’s digital infrastructure. However, while PAM has proven effective at managing passwords and traditional credentials, SSH keys, which are far more prevalent and powerful than passwords, require a new approach for proper management.[1] Modern Ephemeral Access (MEA) offers an innovative solution to this SSH key challenge.[1] By granting temporary, on-demand access without the need for long-term credentials like passwords or keys, MEA reduces vulnerabilities and streamlines privileged access within companies.[1,2] SSH Zero Trust Suite demonstrates that passwordless and keyless methods are possible and highly effective in addressing security concerns across various environments.[2]
What are your thoughts on the implementation of passwordless and keyless systems within your work environment? What do you think are some challenges that may arise given traditional PAM solutions in handling modern access needs?
References
[1] https://thehackernews.com/2024/09/passwordless-and-keyless-future-of.html
[3] https://www.upguard.com/blog/privileged-access-management
[5] https://www.beyondtrust.com/blog/entry/zero-trust-and-passwordless-authentication


Great article Keerthana!
Passwordless authentication is of great benefits of which one is reducing password attacks by a great percentage, but I also believe it would be an expensive infrastructure to acquire especially for small businesses.
The future of passwordless authentication is here and it would be an interesting evolution!
Thank you Ukamaka! I completely agree with your thoughts. While Zero Trust Suite does provide numerous benefits in eliminating attacks, implementing this quickly and effectively depends on the companies resources and priorities. A smaller company whose just getting started may not need such advanced security measures right off the bat. This is a very good point you bring up, Thanks Ukamaka.
keerthana! the article is fascinating and i feel that Zero Trust Suite demonstrating that passwordless and keyless methods are possible and highly effective in addressing security concerns across various environments is a way forward for organization’s security across the world in the era of remote work to ensure proper security measures.
This is a great post! One of the major struggles in cybersecurity is the mismanaging of user credentials, especially passwords. A lot of users worldwide do not store their passwords securely or even worse, they use the same passwords on a variety of websites which exposes them to multiple data breaches. If one account is compromised, the attacker can try those credentials on other websites and succeed. Combining this concern with PAM, I think it is definitely awesome to have a method that doesn’t require long-term credentials. When considering high-level access in companies that involve high volumes of sensitive data, the Zero Trust Suite is definitely a better option to not only secure communication and access to data, but also only granting access to systems only when needed, with credentials expiring after. This completely eliminates the concerns with traditional password process. This is an exciting find!
Great post !
The idea of implementing a passwordless and keyless system like MEA seems like a huge step forward in reducing security risks. Traditional passwords are such an easy target for attackers, so moving to a temporary access model would definitely make systems more secure as well as remembering passwords is also a problem in itself.
Amazing article! I got an email today from LastPass, password manager I use, that they have passkeys in beta mode now. Passkeys are similar concept that relies on biometric features of the device like fingerprint or face recognition that can help in a password less future. However, I am concerned about AI being able to use deepfakes to bypass such security mechanisms.