
DNS Tunnel Attack (Detection and Measures)
We are happy to introduce our group project: DNS Tunnel Attack (Detection and Measures)
This project has been completed by A S M Nazimuddoullah and FAHIM UDDIN
In this project, we studied DNS functionalities, DNS tunneling attacks with their features, and different methods to detect DNS tunneling attacks. At the same time, we explored different aspects to bolster networking approaches to defend against and effectively tackle such tunneling attacks.
DNS tunneling can be used by attackers to exfiltrate data or establish hidden communication channels. Understanding this technique helps develop better security measures and detection methods. From incident responders in security operation centers to network administrators in back-office teams, everyone needs to understand this tunneling mechanism to respond to such attacks.
If a company considers protecting its data from exfiltration or leakage, IT professionals typically focus on robust firewalls, IDS, IPS, or other network security measures. However, monitoring and analyzing DNS traffic for potential tunnels often receives less attention, which attackers can exploit for data exfiltration. For example, in 2018, the DarkHydrus group targeted a Middle Eastern government agency. They used malicious Excel Web Query (.iqy) files to exploit Excel’s ability to download remote content. This led to the installation of a PowerShell backdoor, potentially a custom-built tool or a combination of open-source components. The backdoor granted DarkHydrus unauthorized access to the system, highlighting the dangers of exploiting lesser-known file formats. [9]
Payload Analysis
Unit 42 of Palo Alto Networks[9] examined the credential.iqy an .iqy file (SHA256: cc1966eff7bed11c1faada0bb0ed0c8715404abd936cfa816cef61863a0c1dd6) which contains only the text “hxxp://micrrosoft[.]net/releasenotes.txt”
Outcomes of the analysis
Microsoft Excel automatically opens .iqy files and there will be the following pop-up
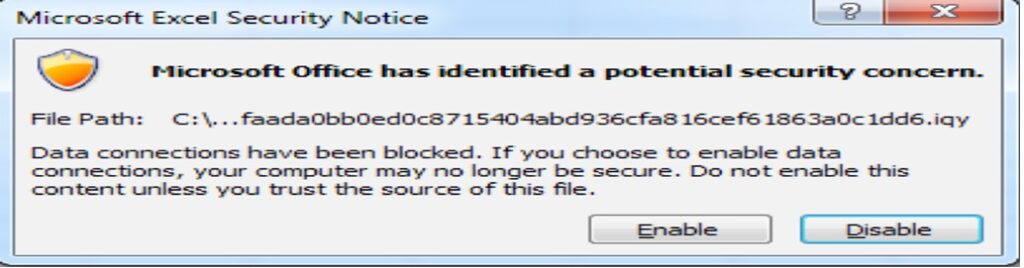
Source: Unit 42 of Palo Alto Networks
By enabling the pop-up and confirming the SHA256 hash (bf925f340920111b385078f3785f486fff1096fd0847b993892ff1ee3580fa9d) provided in the releasenotes.txt file, the user allows Excel to save the following formula to cell A0 of the worksheet:

Source: Unit 42 of Palo Alto Networks
Then the above formula will run PowerShell script hosted at the URL hxxp://micrrosoft[.]net/winupdate.ps1. and the following pop-up for user consent will be to access remote data.
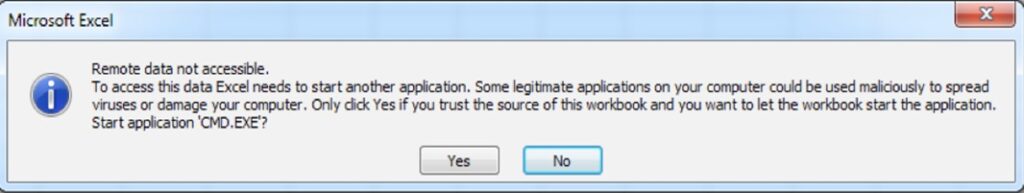
Source: Unit 42 of Palo Alto Networks
The winupdate.ps1 script (SHA256: 36862f654c3356d2177b5d35a410c78ff9803d1d7d20da0b82e3d69d640e856e) is the main payload of this attack that is known as RogueRobin.
The payload is then installed on the target system. It communicates with its configured Command & Control servers using a custom DNS tunneling protocol, leveraging various DNS queries and records. This results in a DNS tunneling attack.
Our teaching aid provides insights into identifying and mitigating DNS tunneling threats for your enterprise or network. Designed as a PowerPoint presentation, the teaching aid guides you through the information and offers references for further exploration. In summary, understanding DNS tunneling is crucial for enhancing cybersecurity posture and safeguarding our network.
DNS Tunneling Attack
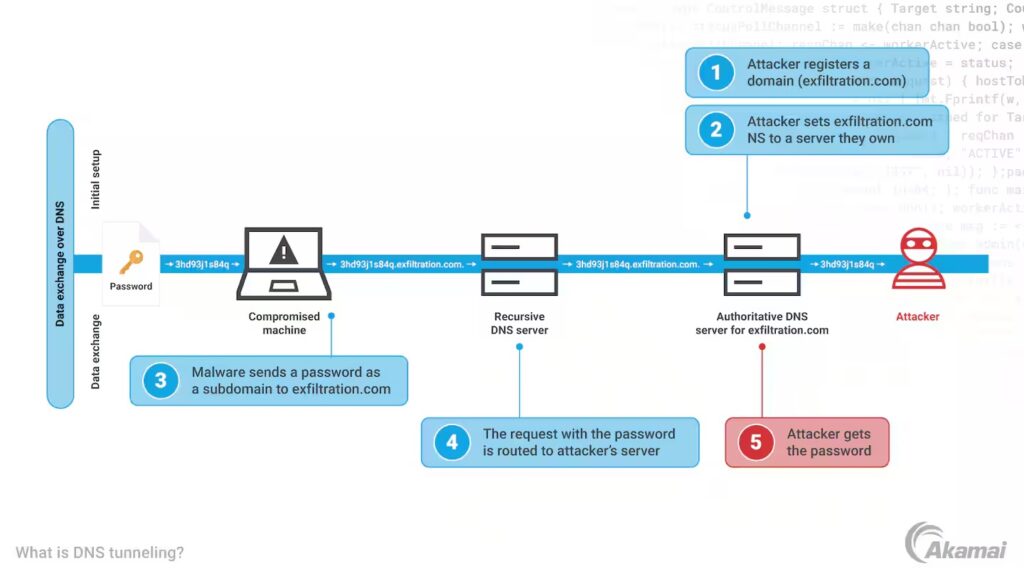
Source: https://www.akamai.com/site/en/images/article/2023/what-is-dns-tunneling.png
An attacker sets a trap: they register a fake domain (exfiltration.com) and configure its server with tunneling malware. Once a target is infected with their malware, it makes normal-looking DNS requests. The attacker’s server intercepts these requests and injects hidden commands masked as legitimate responses. This establishes a secret tunnel between the victim and attacker, allowing for both command and data transfer hidden within DNS traffic.
Detection of DNS Tunneling
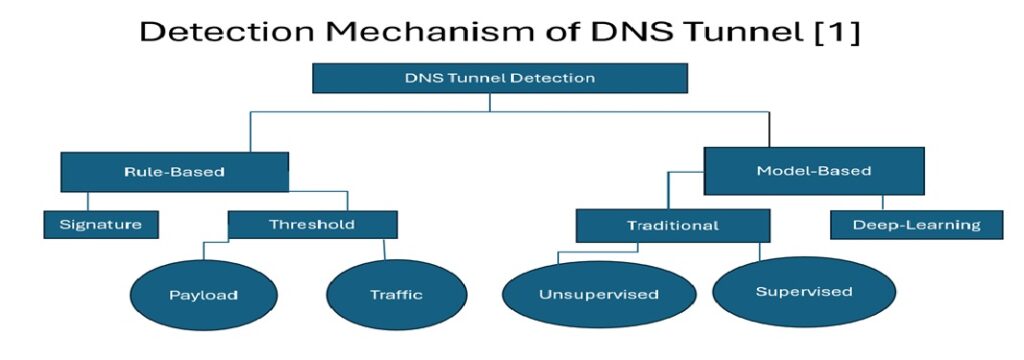
Generally, rule-based methods are simpler to implement, but they are less effective against advanced techniques mentioned in model-based methods. Machine learning and deep learning methods offer more knowledgeable detection capabilities but require considerable computational resources and skilled personnel. A combination of these techniques can provide robust defenses against DNS tunneling attacks.
Conclusion
In this project, we studied the functions of DNS, the features of DNS tunneling, and the threats posed by DNS tunneling attacks. We also demonstrated how attackers exploit the DNS process to create secret channels for stealing data.
To combat this, we explored various detection methods for these attacks and proactive security measures such as monitoring, implementing strong firewalls, and blocking suspicious activities. By understanding DNS tunneling and implementing these defenses, organizations can significantly improve their cybersecurity.
Enjoy the learning
Please have a look at our teaching aide and discussion questions in below.
Teaching Aide
Discussion Questions:
Q1. What is DNS tunnel and what are the common use cases for DNS tunneling?
Q2. How can you detect and mitigate DNS tunneling?
Q3. What are the differences between DNS tunnel and SSH tunnel?
References
1. A comprehensive survey on DNS tunnel detection
https://www.sciencedirect.com/science/article/pii/S1389128621003248
2. Malicious DNS Tunneling Detection in Real-Traffic DNS Data
https://ieeexplore.ieee.org/abstract/document/9378418/authors#authors
3. https://www.paloaltonetworks.com/cyberpedia/what-is-dns-tunneling
4. https://datatracker.ietf.org/doc/html/rfc1034
5. https://datatracker.ietf.org/doc/html/rfc1035
6. https://www.checkpoint.com/cyber-hub/network-security/what-is-dns-tunneling/
7. https://www.cloudflare.com/learning/dns/what-is-dns/
8. https://www.akamai.com/glossary/what-is-dns-tunneling
10. Cover Image: https://www.secion.de/assets/images/8/DNS_Tunneling_1-5de2babc.jpeg
