
Ransomware attacks in the Healthcare sector has been on the rise in the past few years, and this may be as a result of what is at stake such as life, legacy system, patient record e.t.c
McLaren Health care hospitals has experienced two ransomware attacks in the space of one year.
The first rasnsomware attack was last November, the health care network informed at least 2.2 million people that their data had been breached between July and August 2023. The BlackCat Ransomware gang claimed responsibility for the attack. [1]
Ransomware group ALPHV/BlackCat took responsibility for the attack at McLaren, claiming they stole data from 2.5 million patients and continue to operate a “backdoor” on the nonprofit health system’s network, according to Security Affairs.
The health system launched an investigation to “identify what, if any, data exposure occurred” and retained cybersecurity experts to assist, according to a McLaren spokesperson. Based on their current analysis, the spokesperson told Healthcare Dive that they see no evidence to support the backdoor claim.[2]
In less than a year of the BlackCat ransomware attack, another ransomware attack hit McLaren Health care hospitals. Before the disclosure of the attack by McLaren, its employees at McLaren Bay Region Hospital in Bay City have shared a ransom note warning that the hospital’s systems have been encrypted and stolen data will be published on INC RANSOM ransomware gang’s leak site if a ransom is not paid.[4]
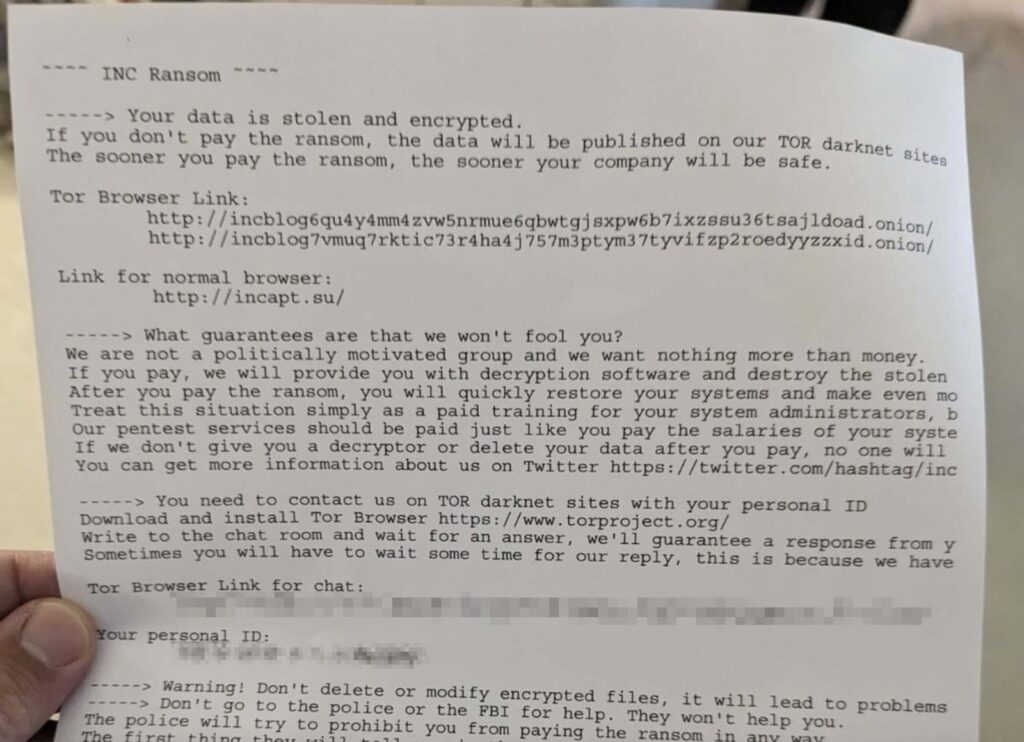
Fig 1. McLaren-ransom-note (Thomas Barz)[4]
Later that week in August of 2024, Mclaren put out a statement on their website “The attack is impacting its information technology systems across the organization’s 13 hospitals, Karmanos cancer centers, surgery centers, and clinics,” the health system said in a statement. “The disruption is expected to continue through the end of August, while cyber forensic investigations are ongoing. The incident is contained, but access to certain McLaren systems remains limited.”[3]
IMPACT OF THE ATTACK
The impact of any cyber attack is usually outrageous, and when lives are involved is unimaginable.
The August 2024 ransomware attack at McLaren Healthcare Hospital had the following impacts:
- Lost Databases: As per several sources, McLaren lost its patient databases. It advised patients to carry their detailed health information to appointments including medical history and existing medication they are on. The loss of comprehensive information on patients’ medical history, the drugs they may be on and past treatments, is affecting the treatments they are able to safely receive now.
- Rescheduled Appointments: Several patients reported that their appointments had been rescheduled as result of the cyber attack at McLaren, including those for Cancer treatments.
82-year-old Reginald Tidball, a patient at McLaren Karmanos Cancer Center undergoing chemo and radiation for lung cancer said he’s survived cancer multiple times. However, he was disappointed this week as his appointment kept getting rescheduled. Several other similar stories have been coming to light since last week.
Cardiac tests have been postponed and radiation therapy appointments have supposedly been cancelled as a fallout of the ransomware attack. Many have apparently been told that without comprehensive documentation the doctors cannot deliver therapies, especially radiation therapies, safely. - Employee Woes: The attack is also apparently affecting employees’ paycheck. Once the disruptions were identified as a cybersecurity incident, employees were asked to shut off their systems. Staff were given the option to use their Paid Time Off to cover for the days without work or go on unpaid leave. Many said they feel like they’re being punished for something that’s not their fault.[1]
CONCLUSION:
The growing ransomware attacks on the Health care sector needs to be addressed with a robust Cyber incident response plan and continuous security awareness training and tabletop exercises as the Health sector is an easy target for cybercriminal as it has a lot at stake especially lives and would want to do anything to protect and save lives of their patients such paying the ransom to regain access to their system.
Standards on how data is stored and accessed on health care systems should be reviewed and better secure ways should be implemented to ensure that the impact and recovery from a cyber attack does not disrupt operational activity especially ones that are critical to patients lives
References.
- https://www.cm-alliance.com/cybersecurity-blog/mclaren-health-care-ransomware-attack-top-updates
- https://www.healthcaredive.com/news/mclaren-health-care-ransomware-attack/695646/
- https://www.lansingstatejournal.com/story/news/local/2024/08/17/ransomware-attack-mclaren-health-care-patients-services-appointments/74840781007/
- https://www.bleepingcomputer.com/news/security/mclaren-hospitals-disruption-linked-to-inc-ransomware-attack

Hospitals are prime targets due to the critical nature of patient care, sometimes leaving them with no choice but to pay ransoms to regain access. And I agree that one way to reduce this risk is by implementing robust incident response plans, regular security training, and stricter data protection measures. Great post, Ukamaka!
I completely agree that healthcare sectors must prioritize improving its security measures to defend against ransomware attacks. Given their critical role in saving lives, healthcare organizations are often vulnerable due to outdated systems and limited cybersecurity resources. Strengthening data protection and implementing more secure protocols will help minimize the impact of cyberattacks, ensuring that vital operations—especially those essential to patient care—remain uninterrupted. It’s a sad reality that health sector has become a frequent target for these attacks. The pressure to quickly restore operations can lead to paying ransoms, putting both patient care and sensitive data at serious risk. It’s deeply troubling that cybercriminals exploit these vulnerabilities, fully aware that they are endangering people’s health in the process.
Ukamaka, this is an insightful and well-researched post on the growing threat of ransomware in the healthcare sector. The McLaren Health Care attacks highlight how cybercriminals exploit vulnerabilities in critical industries, with devastating consequences for both patients and staff. I found it particularly alarming that cancer treatments and cardiac tests were delayed due to the attacks, showing how cybersecurity failures can directly impact lives. Your point about the need for robust incident response plans and continuous security awareness training is crucial. More hospitals should prioritize cyber hygiene practices to prevent such incidents. Thanks for shedding light on this urgent issue!
Totally agree, hospitals are prime targets for ransomware because of outdated systems and weak cybersecurity, putting patient care and data at risk. The McLaren Health Care attacks highlight the severe impact, with delayed treatments underscoring the need for stronger security. Implementing robust incident response, data protection, and staff training is crucial. It’s alarming that cybercriminals exploit these vulnerabilities, endangering lives. Thanks for shedding light on this urgent issue.
Well done Ukamaka! I’ve always wondered what really happens to the retrieved data after a ransom is paid? While stolen appointment details and medication records are concerning, what terrifies me the most is the vulnerability of patients with implanted medical devices like pacemakers or insulin pumps. Hospitals store critical data, including device IDs and access credentials, which could potentially be exploited for external manipulation.
This isn’t just theoretical, back in 2017, the FDA recalled 465,000 pacemakers due to vulnerabilities that could allow hackers to remotely alter device settings, potentially endangering patients (https://www.theguardian.com/technology/2017/aug/31/hacking-risk-recall-pacemakers-patient-death-fears-fda-firmware-update).
Even if the hospital regains access to its systems, how can they trust the integrity of the data after it has been in the hands of hackers? Any tampering or undetected alterations could have life threatening consequences. This raises a critical question: Should hospitals even consider recovering and reusing compromised data, or is a complete system rebuild the only safe option?
Great post, Ukamaka. It is really a great concern having such ransomware incident in critical services like healthcare that impacts people’s lives. Recalling from November 2023, similar healthcare incidents happened for five hospitals in Ontario where patients’ data were stolen and published online. It has become crucial requirement for healthcare systems to use more stringent controls sustaining patient data privacy. Using data privacy techniques such as the differential privacy, adding noise to the raw data and rate control may help mitigate data privacy breaches if a data leak happens. Additionally, Oblivious Transfer and homomorphic ciphers increase the secrecy of data privacy when exchange. In healthcare, Fast Healthcare Interoperability Resources (FHIR) become very usable in the healthcare system as it foster patient information pseudonymization, and raw data is not identifiable (Raso, Emanuele, 2024)[1].
[1] Raso, Emanuele, et al. “Anonymization and Pseudonymization of FHIR Resources for Secondary Use of Healthcare Data.” IEEE Access, vol. 12, 2024, pp. 44929–39, https://doi.org/10.1109/ACCESS.2024.3381034.
This blog highlights the terrifying reality of ransomware attacks in the healthcare sector. It’s one thing when a cyberattack steals data or locks out systems, but when it directly affects patient care like delaying cancer treatments and cardiac tests it becomes a life-or-death issue.
Hospitals and healthcare organizations should receive the highest level of attention when it comes to cybersecurity, given the vast amount of sensitive data they manage and the severe consequences patients face in the aftermath of a breach.
In a blog I wrote about the ransomware attack on Change Healthcare, I shared a “wishful thought” thus, the need for a dedicated cybersecurity task force with nationwide authority to randomly pentest the defences of critical organizations. This task force could identify vulnerabilities, provide actionable recommendations with an implementation deadline, and ensure healthcare institutions aren’t caught off guard because, too often, that’s exactly what happens. Good job Ukamaka!
Great Job Ukamaka! In recent years, hospitals have become prime targets for ransomware attacks. Two key factors contribute to this trend: the urgency of medical services, which pressures institutions to pay ransoms quickly to restore critical operations, and the lack of robust cybersecurity measures in many healthcare systems. As of 2024, 386 cyber-attacks on healthcare institutions have been reported, with data theft and ransomware incidents continuing at a rate comparable to 2023—previously the worst year on record for healthcare breaches. However, as per reports the scale and impact of this year’s attacks are more severe. This brings a lots of cybersecurity challenges for the Health Care Facilities.
Here is a link for the post on Challenges faces by Health Care : https://www.aha.org/news/aha-cyber-intel/2024-10-07-look-2024s-health-care-cybersecurity-challenges
Hi Ukamaka, thank you so your post! I agree that this is very concerning as ransomware attacks are targeting the health care sector. I heard ransomeware in the past but this is the first time I read article on health care sector. I do agree that healthcare is a prime target as it has a lot of critical impact on people but we need to stop this. By reading the post, I am trully scared that the impact if I am in the hospital and there is a ransomeware happen. The appointments record are gone, and in this stage of world, we relay on technology so much, we all know that thousands of Delta flights were cancelled due to the software issue. Imagine patients where waiting for surgeries, or cancer patients waiting for chemotherapy, all these are vert critical cannot be delay. So we need to find a way to practe the data, also this is not fair for the employees as they need to either take a unpaid leave or use their PTO.