On September 8, 2025, the JavaScript ecosystem faced one of its most significant supply chain attacks. A phishing campaign compromised the npm account of maintainer Josh Junon (~qix), allowing attackers to push malicious updates to 18 widely used packages including chalk, debug, and ansi-styles with over 2.6 billion weekly downloads full list available here (Palo Alto Networks, 2025).
This breach shows how one hacked account can put millions of developers at risk, but it also proves that fast action can stop a bad situation from turning into a disaster. It’s a wake-up call about the growing dangers of supply chain attacks in today’s software world, and why taking a prevention-first approach is no longer optional.
For anyone writing JavaScript, this wasn’t just news on a screen, it was a reminder of how easily our own projects could be affected.
This post will cover what went wrong, the impact, and lessons learned.
Timeline of the Breach
According to a report by Palo Alto Networks (2025), the phishing email disguised as a support request from npmjs.help, tricked Junon into disclosing credentials. Once inside, attackers updated multiple packages he maintained, some with over 1 billion monthly downloads.
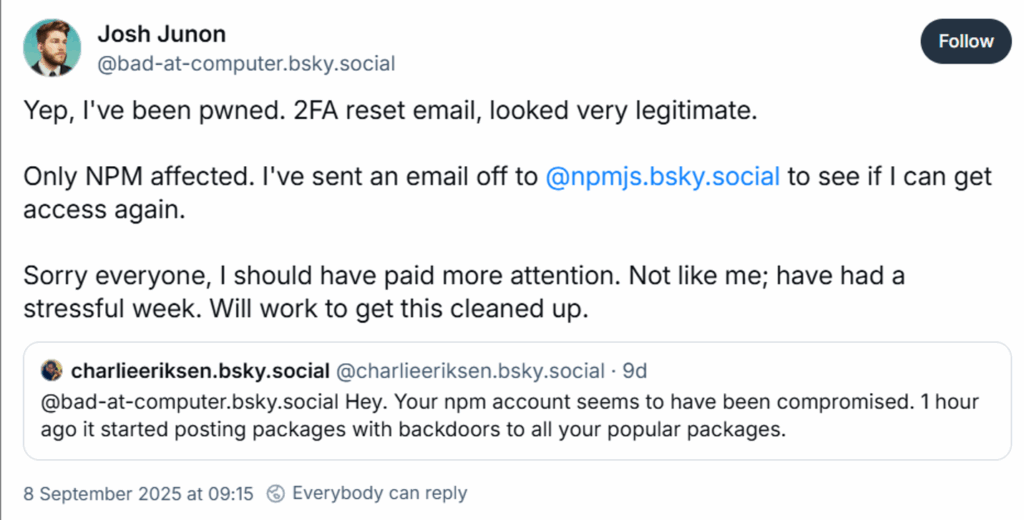
Fortunately, detection was swift. Aikido Security (2025) reports:
- Minutes: Aikido’s monitoring flagged malicious code.
- 5 minutes: Junon was alerted.
- Hours: Compromised packages were removed.
- Ongoing: Security audits across the ecosystem.

The speed of response underscored both the effectiveness of monitoring tools and the narrow window for preventing disaster. This chain of events shows how quickly one stolen account can spiral into a system-wide threat, and it’s a reminder that spotting the problem early often makes the difference between a close call and a disaster.
Technical Details: How the Breach Happened
The root cause was phishing. Attackers registered npmjs.help days earlier and used it to harvest credentials. They injected obfuscated JavaScript designed to:
- Hook key functions (fetch, wallet APIs).
- Scan for wallet addresses and transaction data.
- Rewrite transactions with attacker-controlled addresses.
- Hijack funds silently while masking changes.
ReversingLabs (2025) reported that more than 550 GitHub files were linked to the malware which targeted Ethereum, Bitcoin, Solana, and other blockchains. Tomislav Peričin, co-founder of ReversingLabs, warned that:
“There’s no one building code with npm packages that isn’t possibly affected by this.”
Since the malware worked inside core wallet functions, the usual defences around the network weren’t enough. Real protection depends on stronger account security and checks that confirm packages haven’t been tampered with.
Impact of the Breach
According to the United Nations University (2025), the malware caused almost no direct losses, only a few cents stolen before it was removed, but the potential consequences could have been staggering.
- Millions of compromised applications.
- Theft across cryptocurrency wallets and DeFi protocols.
- Loss of trust in the npm ecosystem.
- Cascading failures in business-critical systems.
The outcome proved that even short delays in detection could have led to global fallout.
Lessons Learned & Best Practices
This breach highlights how fragile open-source ecosystems can be. To mitigate risks, developers and organizations should:
- Pin package versions and use lock files.
- Audit dependencies and clear caches after incidents.
- Reinstall packages from trusted sources only.
- Adopt frameworks like NIST or ISO 27001 for supply chain security.
- Require phishing-resistant MFA for maintainers.
- Enable package integrity verification (e.g., npm audit, npm ci with lockfile verification).
- Use Sigstore/cosign to sign and verify build artifacts.
The lesson is simple: trust is not enough. Audit, update, and defend.
Conclusion
The largest npm hack in history began with a phishing email and ended as a near miss. Actual damages were negligible, but the potential destruction was immeasurable.
This is a warning for everyone who depends on open source: without stronger supply chain security, the next attack may not be contained in time.
Should stricter requirements be imposed on open-source maintainers, or would that undermine collaboration?
References
- Junon, J. (2025, September 8). Post on Bluesky
- Palo Alto Networks. (2025, September 9). npm supply chain attack
- Aikido Security. (2025, September 9). npm debug and chalk packages compromised
- ReversingLabs. (2025). Crypto wallets targeted in widespread hack of npm, GitHub
- United Nations University. (2025, September 10). The largest npm supply chain attack: What happened, impact, and how to respond


Great Post! Thank you so much for providing a clear narrative around this complicated incident. The takeaways and detailed timeline are extremely useful. That millions of projects would have been adversely affected by a compromised account is terrifying. As much as we want open-source collaboration to remain open and convenient to contributors, we need to implement stricter security measures like MFA as well. The very future of the ecosystem is contingent upon finding a balance between openness and security itself.
Really interesting topic! It shows how even experienced and tech-savvy users can still fall for phishing attacks. These scams are definitely getting more advanced, probably with help from AI. Nowadays, no one is safe from it.
Really interesting topic! It’s surprising how even experienced and tech-savvy users can still fall for phishing attacks. These scams are definitely getting more advanced, probably with the help of AI, Phishing remains such a common attack method.
Really interesting topic! It shows how even experienced and tech-savvy users can still fall for phishing attacks. These scams are definitely getting more advanced, probably with help from AI. Nowadays, no one is safe from it.
Really interesting topic! It shows how even experienced and tech-savvy users can still fall for phishing attacks. These scams are getting more advanced, probably with help from AI. Nowadays, no one is safe from it.
Thank you for the very clear breakdown Joy! This case really shows how social engineering can bypass even the most advanced technical defenses. As you mentioned one phished credential nearly compromised billions of downloads. I also noticed how you highlighted integrity checks and MFA; those are exactly the kinds of preventive controls I have researched on my own time/in class, and it goes a long way to increase protection. I was curious, do you think requiring maintainers to use hardware security keys would be enough to stop future incidents, or would that place too much burden on open-source contributors?
Hardware security keys would definitely make it harder for phishing attacks like this to succeed, since they’re one of the best ways to block account takeovers. The tricky part is that most open-source maintainers are volunteers, so asking them to buy and manage hardware keys might push some people away. A better balance could be for platforms like npm or GitHub to step in and provide keys for high-risk maintainers, so security is stronger without putting all the responsibility and cost on individuals.
I believe stricter requirements for open-source maintainers make sense after seeing how a single phishing email almost cost them a ton of downloads. Attackers are always looking for cracks in the wall, and stronger safeguards like MFA could seal up those cracks. Nevertheless, the rules should not discourage collaborations since open source depends on free contributions of people.
I agree. This breach shows why stricter safeguards are needed. The key is making sure they don’t scare off maintainers who volunteer their time. Maybe platforms like npm or GitHub could help provide hardware keys so we boost security without hurting collaboration.
This npm incident truly highlights the vulnerability of the open-source ecosystem. A single phishing email almost resulted in billions of downloads being compromised, it’s frightening how nearly we faced catastrophe. The quick detection prevented it from exploding, but we may not be as fortunate next time. Enhanced safeguards such as phishing-resistant MFA for maintainers and improved package signing must no longer be considered optional. Trust is valuable, but in open source, combining trust with verification ensures survival
Great post, Joy! I think this is highly relevant and practical, especially for upcoming security experts and programmers like us. It’s a good reminder that phishing doesn’t just target individuals who are unaware of risks, even experienced security professionals can fall victim. That’s why companies and organizations implement strict procedures and safeguards to mitigate these threats. I also found the rapid response by third party security teams very impressive. Their quick action prevented what could have been a devastating outcome, which shows why organizations invest so heavily in contingency planning and layered defenses. Overall, this post was engaging and informative, an excellent read. Thanks for sharing!
Really appreciated how clearly you broke this down. It’s both surprising and concerning how a single phishing email can ripple through an entire ecosystem and affect packages used by millions. The quick response was reassuring, but also shows why stronger steps like phishing resistant MFA and package integrity checks are essential.
Thanks for sharing this.
This is a fantastic breakdown. It demonstrates how a single compromised maintainer account can have a ripple effect across the entire JavaScript ecosystem.
I like that you focused on both the human and technical side (Phishing).